Address Space Layout Randomization or ASLR: Windows 8, Windows 8.1 and later versions of Windows 10 are reported to be incorrectly implementing ASLR, making us a very critical security feature of Windows.
Address Space Layout Randomization or ASLR is a security technique that selects random memory addresses to run the code of an application.
The ASLR feature was originally released in OpenBSD in 2003 and has since been added to all major operating systems, Linux, Android, MacOS and Windows.
Microsoft has first added ASLR to Windows with 2006 Vista. To enable the feature, users had to install Microsoft EMET and use their GUI to choose to use ASLR in system-wide or application-specific situations.
With the release of Windows 10, ASLR was added to Windows Defender Exploit Guard and users can activate it through the Windows Defender Security Center.
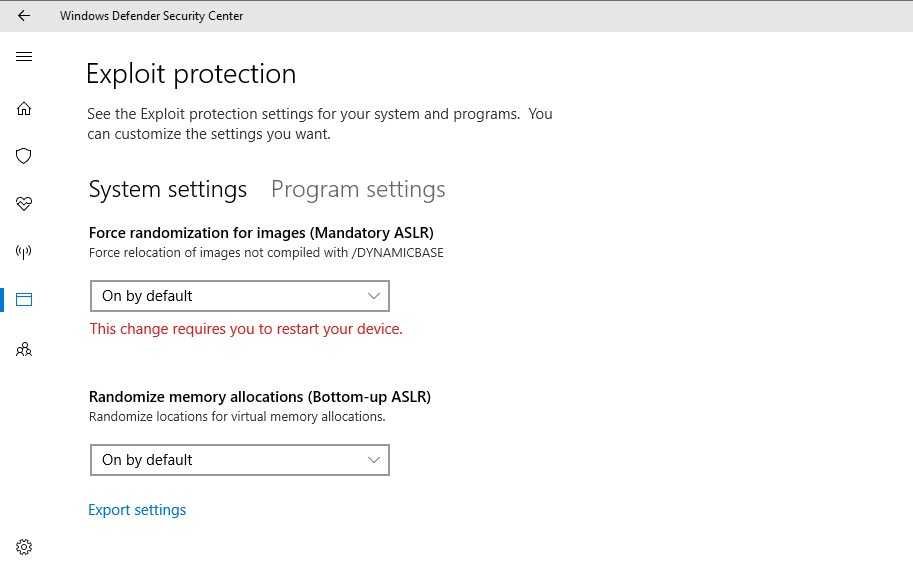
A vulnerability that exists here and 17 years (was recently revealed) that affects the Microsoft equation editor Office, demonstrated that ASLR did not randomize memory code addresses in application files under certain conditions.
According to CERT/CC Vulnerability Analyst Will Dormann, when users enable system-wide ASLR protection, it was errorthe ones that did not allow the creation of random memory addresses.
"The result is that programs used the same address every time on all reboots even on different systems," Dormann said in a statement. published in CERT.
This in practice means that the ASLR is not used though it is turned on, which means that the security feature users are open to attacks of re-using memory addresses of an application containing malicious code.
The researcher says that this issue only affects Microsoft systems from Windows 8 and then because the company changed the registry values through which the ASLR starts.
Of course Microsoft is expected to fix that problem in some future update and for now, the only way to trigger the ASLR feature to work is a wiggle tweak in the Windows registry.
How can I protect:
Create a text file and type the following text:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel] "MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00
Save the .reg file instead of .txt, for example, iguru.reg.
Optionally, you can download the file we made for you, and run it with a double click (after exporting it from .zip)
Right click save as:





