There are many, many tools on the internet that can "break", "fish", "bypass" your passwords on anything. Each of these tools is specialized and addresses from your operating system code, your wifi code, to your connection code to a service.

Learn to protect yourself. These courses are not intended to show you how to become a hacker, but what methods hackers use and how effective they are.
Lesson 1 - The tools
Hackers in principle do not work under windows, in most cases at least. Most tools are made for the Linux environment. So if you want to do any testing on your own systems for how unsafe it is, then you should seriously consider installing linux.
There are many ways to get a linux machine up, such as buying a new laptop and putting it on linux (a pretty expensive solution), or using some of your hard drives and installing a second operating system there (easy, cheap solution , but rather hard on the unconscious) or just start your machine from a live cd, a cd that has the linux up, ready, pre-loaded.
And since our logic is not to "break" the neighbor or Microsoft, but to test our machines and our connections, and in order not to enter into expenses and painful procedures, we will recommend starting linux from a live cd and not even from a cd, but from a simple 4 GB usb stick. From one live usb Well.
Because we will need usb us (we all think we all have a usb, even advertising), a linux environment and some applications that hack specific devices and processes, for convenience we will suggest you take them all in one once they are ready on the internet .
Try them out Kali LinuxOr Backtrack. Our test will be done with the Time. Both are ready linux based on Debian, loaded with ready-made gadgets. There are several online videos (some of which will show you here) about how each tool works.
Let's start on this lesson to build a usb with Kali Linux in, ready and instantly bootable:
Our materials: a usb stick at least 3 GB (4GB is even better), a computer with wifi - prefer a laptop and an internet connection.
Methodology:
- Download Kali Linux from here (we chose 32bit full release, if you can try 64bit)
- In the environment Windows download it win32-image-writer (it's a tool to write to the usb, wait for 5 seconds and it will open a window to download it) (A also pretty easy program for the same job is Universal USB Installer. Download it and follow the instructions provided by official webpage)
-
Insert the usb stick into a usb port on your computer
- Run win32-image-writer
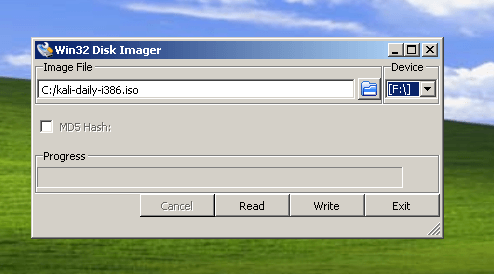
Select the file ISO of Kali Linux which you have downloaded and the device that is your stick.
Click "Write" and wait for the recording to finish.
WARNING: You will lose anything that you have already written on your stroller. Kali Linux registry has the concept of format. Be sure not to cry for lost data which may be present in the stick.
- Once the recording is finished you can remove the stick from your computer, close it all and restart your computer.
- On reboot you will need to enter the bios of your machine and tell it to boot first from the usb port, then from the dvd and then from your hard drive. Here we can not give you specific information since each machine has a different bios. You have to find out for yourself.
- Insert the stick into a port on your computer and reboot your machine by booting from the stick. On the first screen of Kali linux select “Live 686 -pae”. Let it load normally. You are now working in a linux environment and you are doing well Kali Linux they've seen all your peripherals, from your camera to your wireless network card.
- Try having fun with linux and connect either wired or wireless to the internet.
The original one administrator it is called “root” and code is “toor” (all words without quotes)
In the next lesson we will see how easily and quickly one breaks Wireless network with WEP encryption and why we should not put on wireless router our codes with WEP encryption.
Dimitris - iGuRu.gr






You can easily do many things without even having Linux.
Many attacks have been made from windows environments.
As you can also do it with android.
Kali Linux and backtrack is for what specialized stuff.