Hack Back: Tired of hackers? Some companies are willing to hack hackers, but the hack back risks are likely to be much greater than the benefits.
With hack back they will be able to locate the systems they use and delete the stolen information. They can destroy their computers, which is currently illegal. 
The above refers to a company survey Fidelis cybersecurity. The survey reports that many businesses πιστεύουν ότι έχουν την ικανότητα να αντιδράσουν επιθετικά στις επιθέσεις hacking, if they wish.
More than half of respondents said businesses should be able to attack hackers and have the technical ability to detect an attacker, penetrate his systems, and destroy any data that has been stolen after a cyberattack.
More than half of company executives said that if it were legal, they would prefer to attack to get it wrenches αποκρυπτογράφησης μετά από μια επίθεση ransomware παρά να πληρώσουν τους εγκληματίες για να ανακτήσουν access in their data.
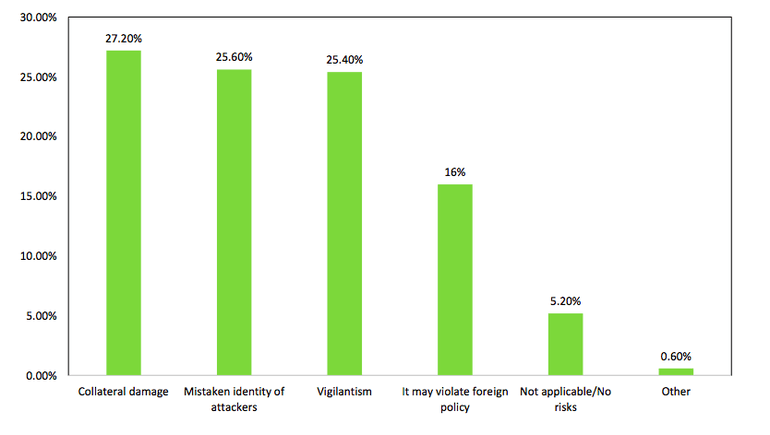
Image: Fidelis
But despite their loyalty to hackers, in fact most businesses do not have these skills, said Andrew Bushby, director of Fidelis Cybersecurity in the UK.
The main concerns about such a strategy are whether they can identify the real offender. There is, of course, the risk of collateral damage, according to the survey.
In fact, to the question of whether companies are financially responsible for any damage caused to innocent computers in a hack back, 63% said the company would be less likely to attempt it, although a 15% said it would He made.
The above is not a totally academic debate: in the US, the law that is being discussed about active cyber security would make cyber hacking legitimate.





