If your computer is infected with Ransomware Thanatos and you are looking for a solution, before you pay a ransom, try a free decryption tool from Cisco Talos to decrypt your files.
Investigators better safetyCisco Talos researchers discovered a weakness in Thanatos ransomware code that allows victims to unlock their encrypted files without paying a ransom to the criminals.
Like all ransomware threats, Thanatos encrypts files and asks its victims to pay a ransom in multiple cryptocurrencies, including Bitcoin Cash (BCH), Zcash (ZEC), Ethereum (ETH) and more, to decrypt their files. Once a computer is infected, all affected encrypted file extensions are changed to .THANATOS and then a note appears asking for a ransom and instructing where to send the money in order to decrypt the files.
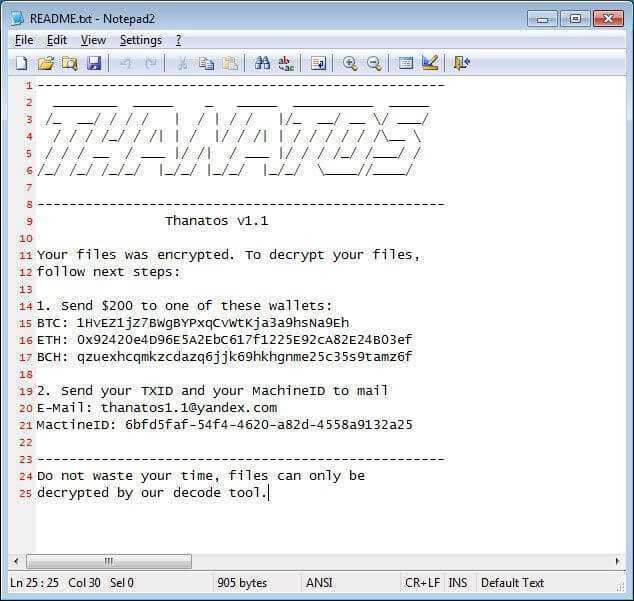
However, because Thanatos uses a different system of different encryption keys for each file, and without storing them somewhere, it is impossible for malicious programmers to send the passwords, even if the victims pay the ransom.
Cisco researchers analyzed malware code and found a loophole in the design of the Thanatos file encryption methodology, based on which they developed a free ransomware decryption tool to help victims decrypt their files. It is called Thanatos Decryptor, is completely free, you can download it from GitHub website, and works for versions 1 and 1.1 of Thanatos ransomware
Since the encryption keys used by Thanatos are based on the number of milliseconds since the last boot of the system, the researchers were able to reverse this logic and recreate the same 32-bit encryption key using brute force attack and Windows Event Logs. For more details on ransoware Thanatos, you can refer in the detailed article published yesterday by Cisco Talos.
To decrypt your encrypted files from Thanatos Ransomware, you need to download Thanatos Decryptor and save it to your desktop. You also need to make sure that you have it installed Microsoft Visual C ++ Redistributable for Visual Studio 2017 otherwise when you try to run Dectyptor you will see one error about missing DLLs.
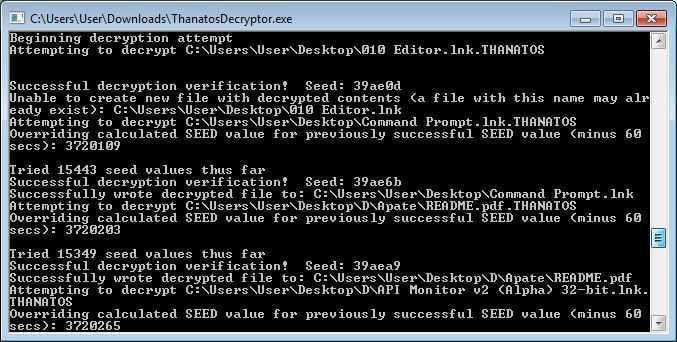
Once you have everything you need, just double-click the executable file (exe) and the decrypter will start looking for files to decrypt. It will only decrypt the following file types:
Image: .gif, .tif, .tiff, .jpg, .jpeg, .png
Video: .mpg, .mpeg, .mp4, .avi
Sound: .wav
Document: .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, .odt, .ods, .odp, .rtf
Other: .zip, .7z, .vmdk, .psd, .lnk
Cisco recommends that you run the decryptor on the same computer where the files were encrypted. THE procedure decryption may take some time, so be patient.





