The new WordPress 5.2 που θα κυκλοφορήσει σήμερα θα φέρει μια νέα τεχνολογία για τις αυτόματες ενημερώσεις, σαν ένα νέο μέτρο άμυνας, εναντίων πιθανών attacks to servers that distribute the updates. The new version along with everything else we have already mentioned, will also carry offline digital signatures for all key updates, themes, plugins and translations.

This new feature complements WordPress Automatic Update, first introduced with version 3.7 on October 24, 2013. The new security feature prevents any potential intruder from making malicious versions of the CMS even if it has gained control. in all WordPress installations and infrastructures.
Prior to the release of WordPress 5.2, this was possible because there was no signature verification mechanism for packages promoted by the update server.
So since automatic updates will now be enabled "by default, for kernel versions and translation files" according to the WordPress documentation site, such an attack could lead to the immediate infection of approximately 33,8% of all websites on the Internet.
"A failure of this magnitude would be catastrophic for the World Wide Web and provide a huge attack platform for the attacker, who could control millions of web hosting accounts from which new attacks could be launched," WordFence said.
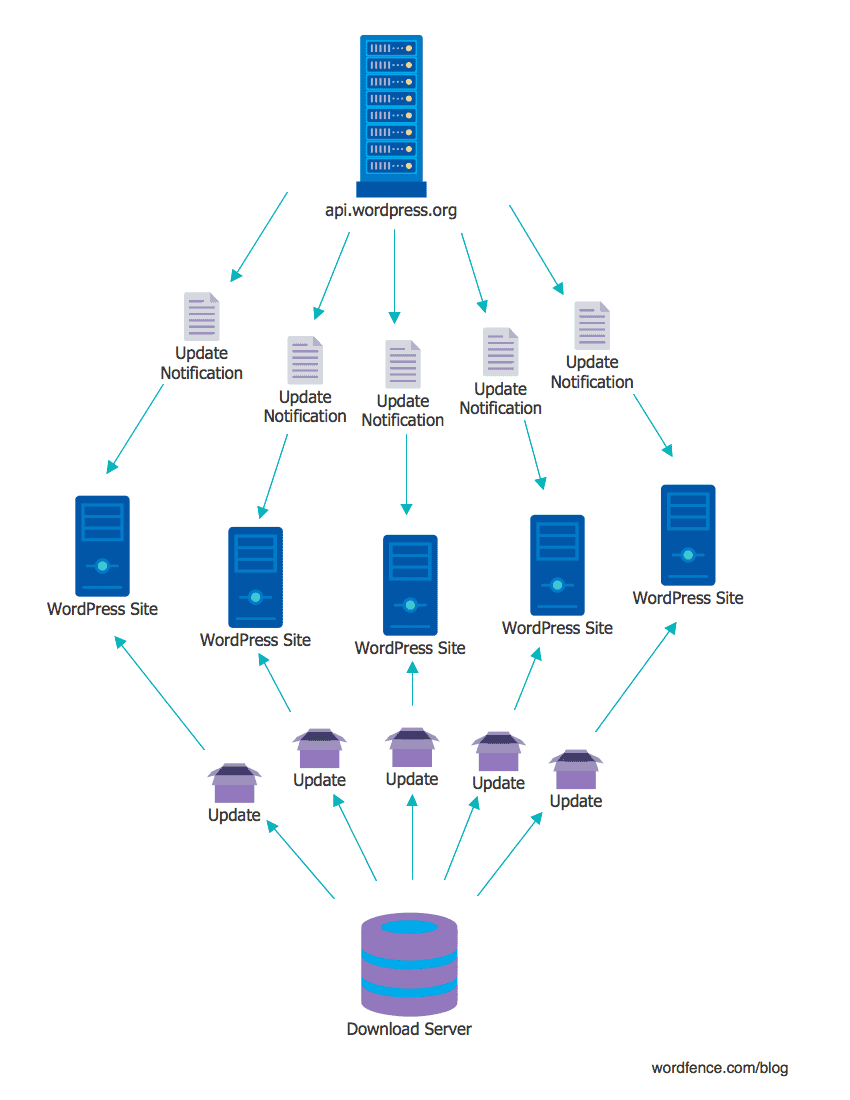
The offline digital signature feature that will be released today with the new WordPress 5.2 adds a real layer of defense to an attack from compromised infrastructure (on the servers of addressς api.wordpress.org).
Paragon Initiative Enterprises first put forward the proposal to shield WordPress from the attacks we described above, and many of its suggestions were included in the base WordPress 5.2 data.
Such as he explains Arciszewski of Paragon Initiative Enterprises:
Before WordPress 5.2, if you wanted to infect every WordPress website on the Internet (about 33,8% of websites at the moment), you just had to hit the update server. This way, you could use the auto-update feature to install malicious code that allowed you to do everything (eg create the largest DDoS botnet in the world).
From WordPress 5.2 onwards, you should perform the same attack but you should also have the digital signatures from the WordPress core. After WordPress 5.2 only the basic CMS updates will be digitally signed. Plugins and themes will be signed later.





