Machete: Her researchers ESET have discovered an ongoing cyberespionage campaign targeting high-profile organizations in Latin America. More than half of the compromised computers belong to the Venezuelan military. However, attacks they have also been recorded in other institutions such as the police, educational institutions and external affairs agencies.
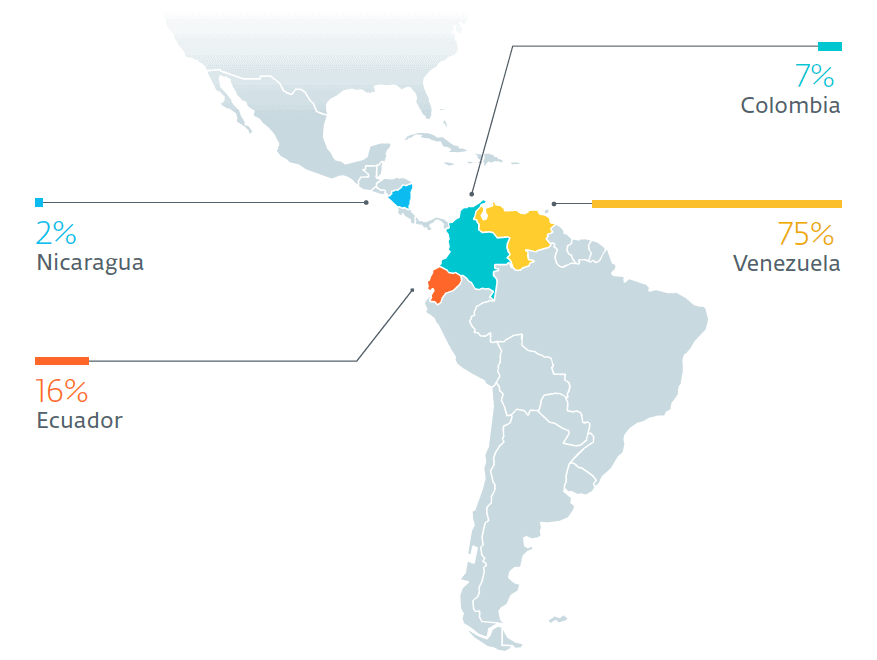
The majority (75%) of the attacks took place in Venezuela, while 16% in Ecuador, targeting military forces. The invaders behind it Machete they stole every week gigabytes confidential documents. The campaign, which is still very active, is taking place at a time when there are tensions, both regionally and internationally, between the United States and Venezuela.
Her researchers ESET were watching a new version of the malware Machete which first appeared a year ago. In just three months, between March and May 2019, the ESET noticed that more than 50 compromised computers were communicating with servers Command & Control belonging to cyber spies. Intruders regularly change their malware, infrastructure, and campaigns spear Phishing.
"Cybercriminals operating Machete use effective techniques spear Phishing. Having long experience in attacks on countries of Latin America, have managed to gather information by refining their tactics over the years. They know their targets, how they can integrate into routine communications and which documents are worth stealing," says ESET Researcher Matias Porolli.
"The intruders export specialized types of files used by S softwaresystem Geographic Information (GIS). They are especially interested in files with navigation paths and locating locations with MGRS coordinate grids ", he adds.
His cybercriminals Machete send very specific emails directly to the victims, modifying them each time. To deceive unsuspecting targets, they use authentic previously stolen documents, such as secret military documents, including "Radiograms”, documents used for communication within the military in Venezuela. Possessing knowledge at the level of military terminology and protocolWell, attackers use these documents to compose very convincing phishing emails.
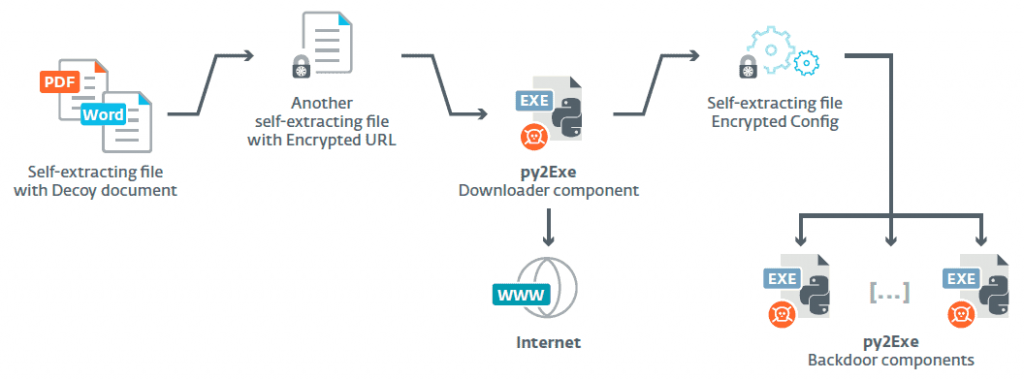
The attack starts with an auto-export file containing a document as "bait" and continues with the download and installation backdoor cuts. It backdoor cuts consists of a spyware program that runs indefinitely, copies and encrypts documents, takes screenshots and records keylogs. Every 30 minutes a program responsible for installing other programs runs, while every ten minutes there is communication with the intruders in order to send the stolen data to the server Command & Control. All the preletterthey misuse the word "Google»In their file names to hide their malicious intent.
"The activation of his team Machete is stronger than ever and our research has shown that it is able to evolve fairly quickly, sometimes within a few weeks. From different elements we have seen in its code Machete "Assessing its infrastructure, we conclude that it is a Spanish-speaking group", explains Matias Porolli.
Its individual programs Machete according to her research ESET 
More details is available on article «Sharpening the Machete» as and on relevant white paperMachete just got sharper: Venezuela's military under attack» on WeLiveSecurity.com.
______________
- Beware of emails asking you to "confirm your deletion"
- Check Point World Threat List June 2019
- Microsoft VBScript disables it by default





