This RobbinHood doesn't give a damn.. A lot productsecurity features include tamper protection (tamper protection) which makes it very difficult to disable software, at least without leaving a trace.
The instant updates they also make it harder for malicious users to break into vulnerable systems because they shut down security gaps and they cannot exploit them.

Similarly, system services often keep their critical files in permanent use, which means that they cannot be easily deleted or modified, which prevents malicious users from destroying them with an attack. ransomware.
But the best one wins… ..
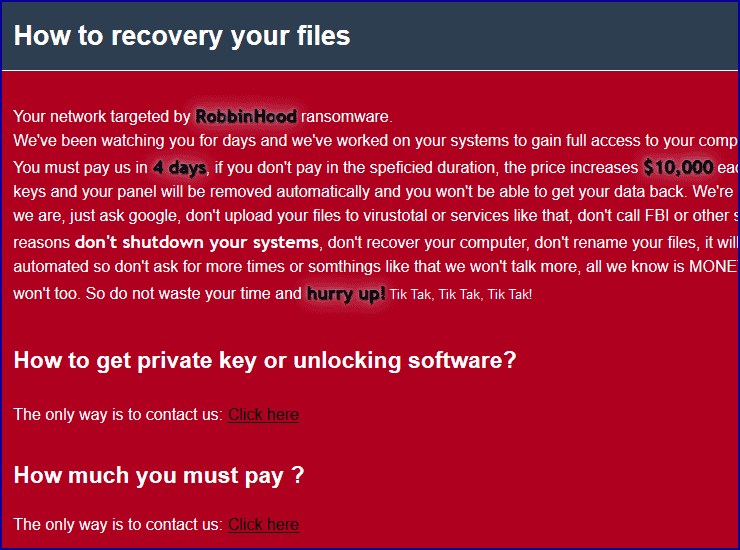
This could be the difference between a ransom claim that you can not avoid paying, because everything is coded and you can not ignore it because all your important data does not exist and your business can not work. .
This is where RobbinHood malware comes in:
Malicious users have discovered a way that helps them bypass all of the above much more easily and gain access to any "secure" system. We wrote the safe with quotes because we consider it a very big tale for the security companies and the peb testers to get rich.
The owners of RobbinHood, instead of looking for vulnerabilities in the operating system and software of the system, just brought their own error!
The way it works is a fascinating story, told in great detail in a SophosLabs survey. If you want more technical details about the attack that we will describe (in a few words) below, see here.
In short, scammers along with ransomware πρόσθεσαν και ένα παλιό αλλά buggy Windows kernel driver.
The old driver is not malware, but it is an official software component of the Gigabyte motherboard, so it is digitally signed by the company. Of course the signature is certified as genuine by Microsoft itself.
So Windows will load the wizard because of the signature…
After that, everything is easy, as as we mentioned the driver may be genuine but it contains an error, which fraudsters can exploit to trick Windows into letting them upload their own, unsigned and malicious files!
And the driver gives them low-level access to the kernel, processes and files of the system, which means that they can kill programs they want and delete files that are usually locked.
Distorting kernel behavior on its own can cause a number of problems, such as programs that stop working properly, or corrupted data, or even BSoD.
But fraudsters do not care.
The moment you notice minor problems, the damage has already been done, and if the computer is on a network, all systems will be locked. Meanwhile, only the scammer has the key to decrypt it.





