Microsoft seems to have fixed some security issues in Microsoft Teams that could be used in chain attacks to retrieve user accounts - all with the help of a .GIF file.
CyberArk researchers they announced today the vulnerability of a subdomain, which in combination with a malicious .GIF file, could be used to "collect user data and eventually obtain all the Teams accounts of an organization".
The team said the security issues affect Microsoft Teams on both desktops and the web version of the program.
Microsoft's communications platform seems to have gained an expanded customer base like other competing services (Zoom, GoToMeeting etc) due to appearanceto him COVID-19. The Microsoft Teams app is used to keep businesses running, and among other things, it offers sharing of corporate data. This fact makes the application a very tempting target for hackers.
During the review of the platform by CyberArk, the team found that each time the application is opened, the Teams client creates a new temporary access badge, which is authenticated through the subdomain login.microsoftonline.com. Other tokens are created to access other supported services such as SharePoint and Outlook.
They noticed two being used cookie για τον περιορισμό των δικαιωμάτων πρόσβασης στο content, “authtoken” and “skypetoken_asm.” So they used these files to obtain a Skype token by sending it to teams.microsoft.com and the subdomains it uses. In two of them they were able to perform a subdomain takeover.
"If an attacker can somehow force a user to visit subdomains occupied (by hackers), the victim browser will send a cookie to the attacker's server. "The attacker (after acquiring the authtoken) can create a distinctive Skype", the team states. "After all this, the attacker can steal the data of the victim's accounts."
However, the chain of attack is complicated, as it was necessary for the attacker to issue a certificate for all the violated subdomains subdomains.
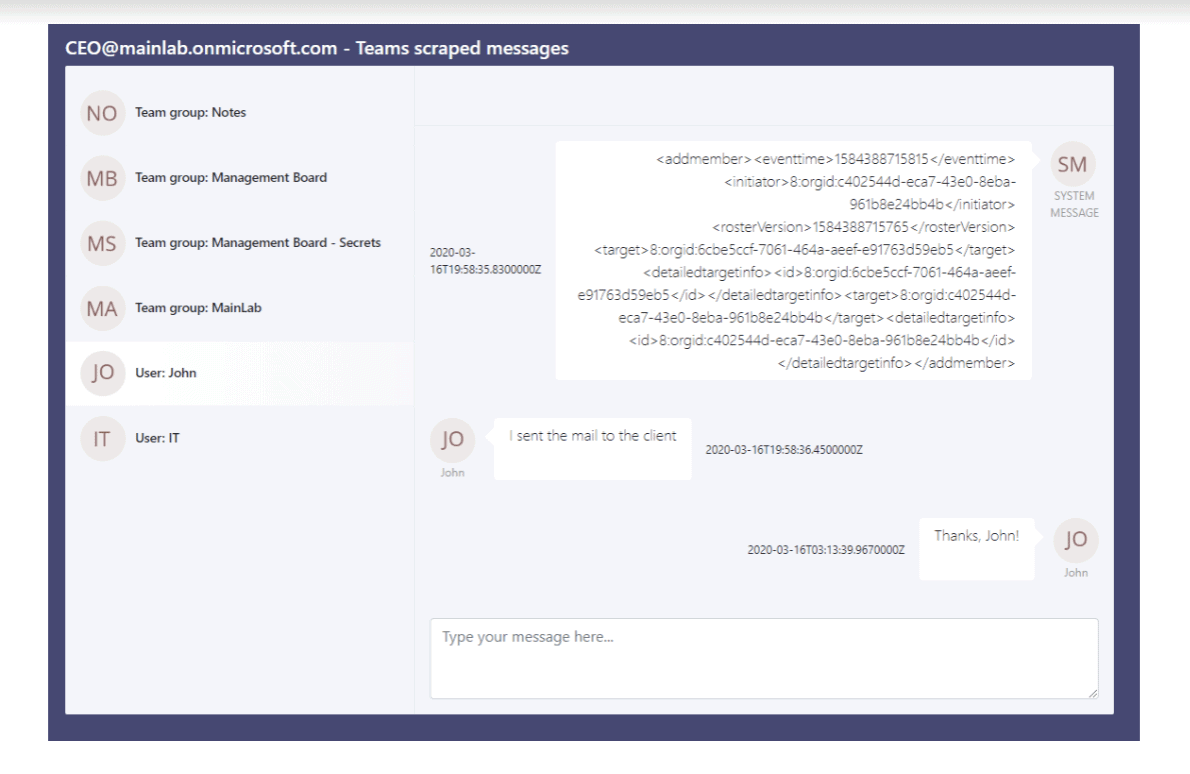
But as subdomains were vulnerable, this challenge was overcome by either sending a malicious link to the subdomain or sending a .GIF file to a group. This could lead to the creation of the required badge needed to violate a Microsoft Teams session of a victim, as the image only displayed could affect more than one person at a time.
CyberArk has released a PoC showing how attacks could have taken place, along with a script that could be used to stop Teams conversations.
The researchers partnered with the Microsoft Security Response Center (MSRC) as part of the Coordinated Vulnerability Disclosure (CVD) program to report their findings.
CyberArk reported the defect on March 23. On the same day, the Redmond-based company corrected the DNS configuration of the two subdomains, and on April 20, an update was released that completely fixes the problem.





