Blockchain Development Technology is a hot topic not only in the areas of finance, encryption, etc., but also in the field of cyber security.
This technology is still in its infancy, as a 'work in development». Therefore, I think it would be too early to call it a 100% safe technology.

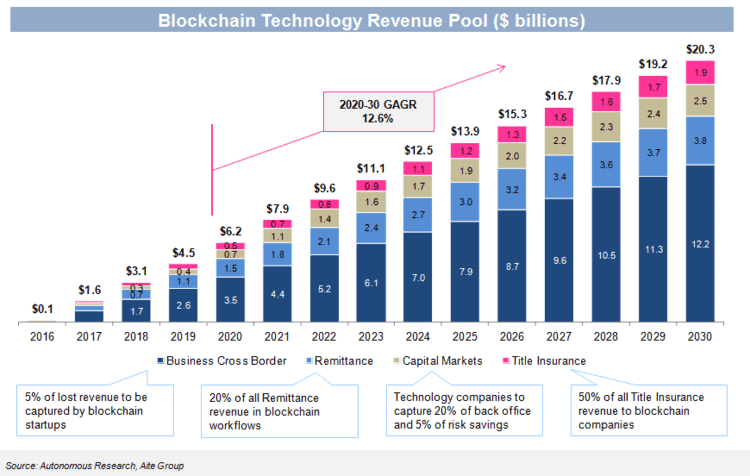
It is estimated that blockchain-based technology companies expect their revenues to grow beyond $ 6 billion by 2020.
Blockchain application development aims at security, but it takes even more effort to achieve it. Exchanges can be accessed Bitcoin in open and public networks where anyone can create a node, but with corporate blockchain applications, they are different from public ones. They are private and networks and are not accessible to everyone.
Although blockchain can be a difficult target for a hacker, it is not unlikely that this will happen. Blockchain experts have warned that blockchain developments could bring vulnerabilities that organizations need to be aware of.
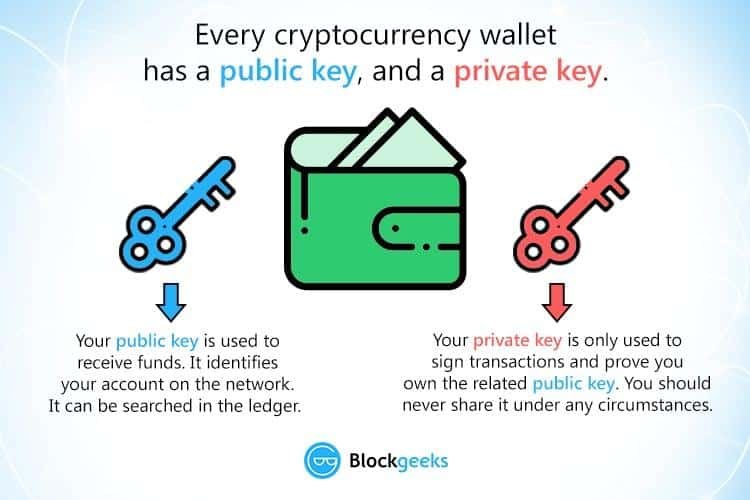
Blockchain access - public or private key:
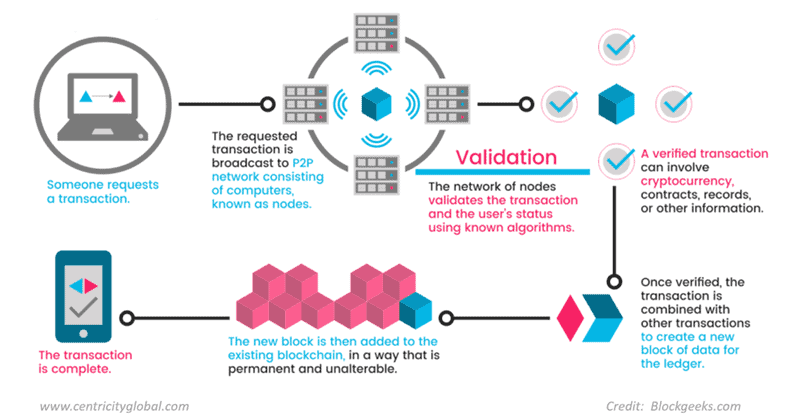
One of the most likely reports comes from the blockchain application itself. The terminal or technically called "end point" is the point of contact between people and blockchain technology.
Blockchain can be accessed via public or private keys. These keys are encrypted character strings of appropriate length to make it almost impossible to guess. Since it is impossible to access data in the blockchain without the precise combination of private and public keys, this shows both the strength and the weakness of this technology.
Possession of keys is as possible as possession of the entire blockchain. The best way to get these keys is to note the user's device - laptop or mobile.
Risk around sellers:
As blockchain becomes more popular, the market for third-party solutions will increase. Top blockchain applications where we can expect the biggest third-party solutions include blockchain integration platforms, wallets, payment platforms, etc. This urgent need for blockchain solutions will create a growing market for blockchain developments.
Along with this, there is also the possibility of exposure through the seller's risks. Organizations can have secure blockchain solutions if they have reliable suppliers. Weak security on their own platforms, incorrect code and staff vulnerabilities can expose customers' credentials and blockchain information to the illegitimate entity. This threat carries more risks with regard to "smart contracts".
In the "full scale" scenario of the beam:
The blockchain architecture is inherently scalable, but no one knows what will happen on a full scale? When certain changes are made, it is scaled by one node. Developing a blockchain involves two major risks, according to the FSOC (Financial Stability Oversight Council) - a US-based federal agency.
First, today's blockchain is limited and therefore we are familiar with handling and solving problems only in this "limited" area. But with every GB expansion, the experience will come with a price, which so far isn't high enough to be significant change in the complete system.
Second, we may be vulnerable to what is being said problems of 51%, a scam in which the majority of the participants may not be legal and conspire against the other participants. This threat could be real if a large number of mining enterprises are established in countries where electricity is easily accessible.
The absence of principles and statutes:
The Forbs ad reported that one of the main weaknesses of blockchain security is the lack of principles and laws. The mere mention of laws and standards puts the roots of the blockchain on alert. The absence of standard procedures and protocols means that blockchain developers cannot learn from the mistakes of others.
If every company, every association and every application operates and follows rules that are "apples" and "oranges", there are risks arising from a custom technology of any kind. In addition, sometimes, chains may be needed to integrate. Lack of standards will result in security threats from merging different technology applications.
Hypothetical code:
Despite its existence for 8 years with Bitcoin, the blockchain that is not related to encryption remains experimental and hypothetical. Just to advertise, some organizations are willing to develop their tried and tested code into an existing blockchain or a completely new blockchain. An example of such activity is the DAO attack.
The DAO is a decentralized autonomous organization developed on the blockchain. Its purpose is to run code for main business smart contracts. One such DAO was created in 2016 by team Ethereum, which had been experimenting while making history by raising $150 million in crowdfunding.
The attacker was aware of the weaknesses of the DAO code and created a DAO affiliate account and made repeated requests to transfer money from the first account to the chain. Since the code did not reduce the original balance after each transfer, nothing could prevent the repeats from playing almost 40 times. After transferring $ 55 million from Ether, the hacker completed the theft. The reason behind which the violation stopped is still unknown.
Blockchain, on the one hand, has great potential to change the world, but on the other hand, it is in its infancy with its own vulnerabilities. Therefore, organizations need to consider business use cases, risks, platform weaknesses, etc. and then implement their solutions with high security and input and output tests.





