WordPress is the most popular CMS platform. Over 63% of websites today are WordPress. Unfortunately, 56% of these sites have significant security issues.
It's really hard to believe that such a popular platform as WordPress can turn out to be unreliable on many security issues. These threats have given hackers a huge advantage over webmasters.
In this issue, we will look at how such a powerful platform, such as WordPress, is affected by multiple cyber threats and how we can secure it.

Statistics related to WordPress Hacking
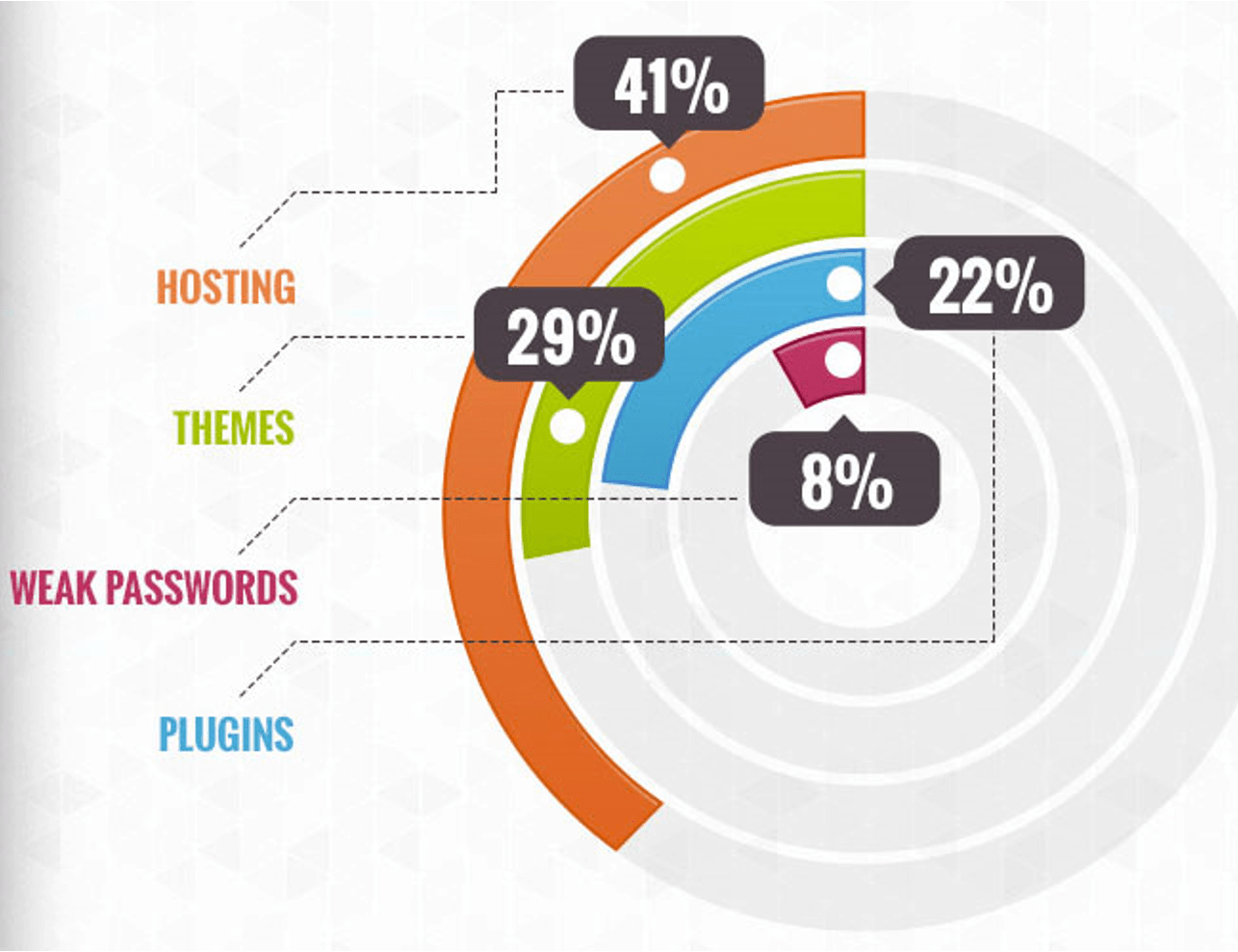
According to CVE Details, XSS (38,1%) remains the biggest threat in WordPress, followed by code execution (15,3%) and finally bypass, with (12,7%) having the third place.
WordPress plugins on the other hand, make our job very simple and fast. However, according to 2019 statistics, 56% of violations were done through different plugins.
All these statistics force regular users like us to question the dominant CMS in the world and its security practices. With this post, we will try to resolve some security issues and find solutions to them.
Weak links in WordPress
"People have been, are and will continue to be the biggest security issue in WordPress," says Dre Armeda when discussing WordPress security.
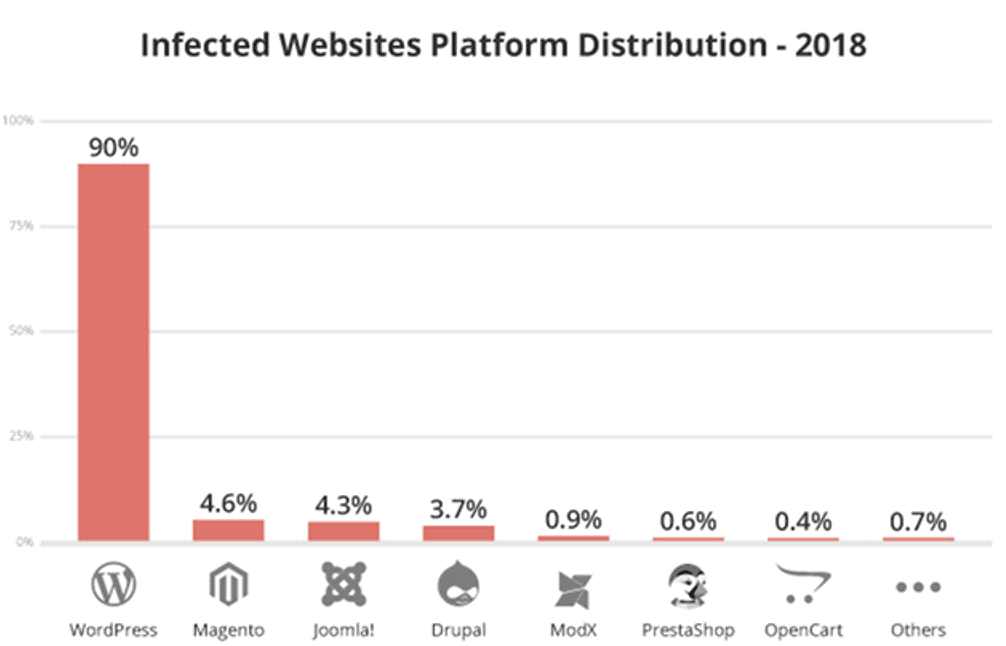
The security of the website is not only about eliminating the risks, but also about reducing it. Most of the users believe that just by installing an SSL certificate for the site, they can provide 100% security to all types of issues and threats to the security of the site.
The most dangerous type of WordPress security issue occurs before or immediately after a site breach. The motivation of one hacker is to gain unauthorized access to the site in WordPress and to damage the site by gaining administrator privileges. Let's take a closer look at the root of all these WordPress security issues
5 Important Safety Gaps You Should Know:
1. Brute Force Attacks
WordPress brute force attacks are nothing more than a trial and error method of entering multiple usernames and passwords. Hackers use different combinations of passwords over and over again until a successful combination is discovered.
The brute force technique was developed to take advantage of the simplest way to access sites: The WordPress login page, however, by default, does not limit login efforts. Thus, bots can attack the WordPress login page using the brute force attack method.
Even if these attacks are unsuccessful, they can damage your server. This is because login attempts can overload your system and slow down your site.
2. File Inclusion Exploits
Another security issue is the vulnerabilities in the PHP code of the WordPress site. These attacks are the next common security issue that can be exploited by hackers.
PHP is the code responsible for the management του ιστότοπού σας στο WordPress, μαζί με τις προσθήκες και τα θέματα σας. Τα File Inclusions εμφανίζονται όταν χρησιμοποιείται ένας ελαττωματικός κώδικας για τη φόρτωση απομακρυσμένων αρχείων. Αυτά τα φορτωμένα αρχεία επιτρέπουν επιπλέον στους hackers να αποκτήσουν πρόσβαση στον ιστότοπό σας. Λόγω αυτών, οι εισβολείς μπορούν να αποκτήσουν πρόσβαση στο archive wp-config.php of your WordPress site.
This, as we all know, is one of the most important files in WordPress installation.
3. SQL Injections
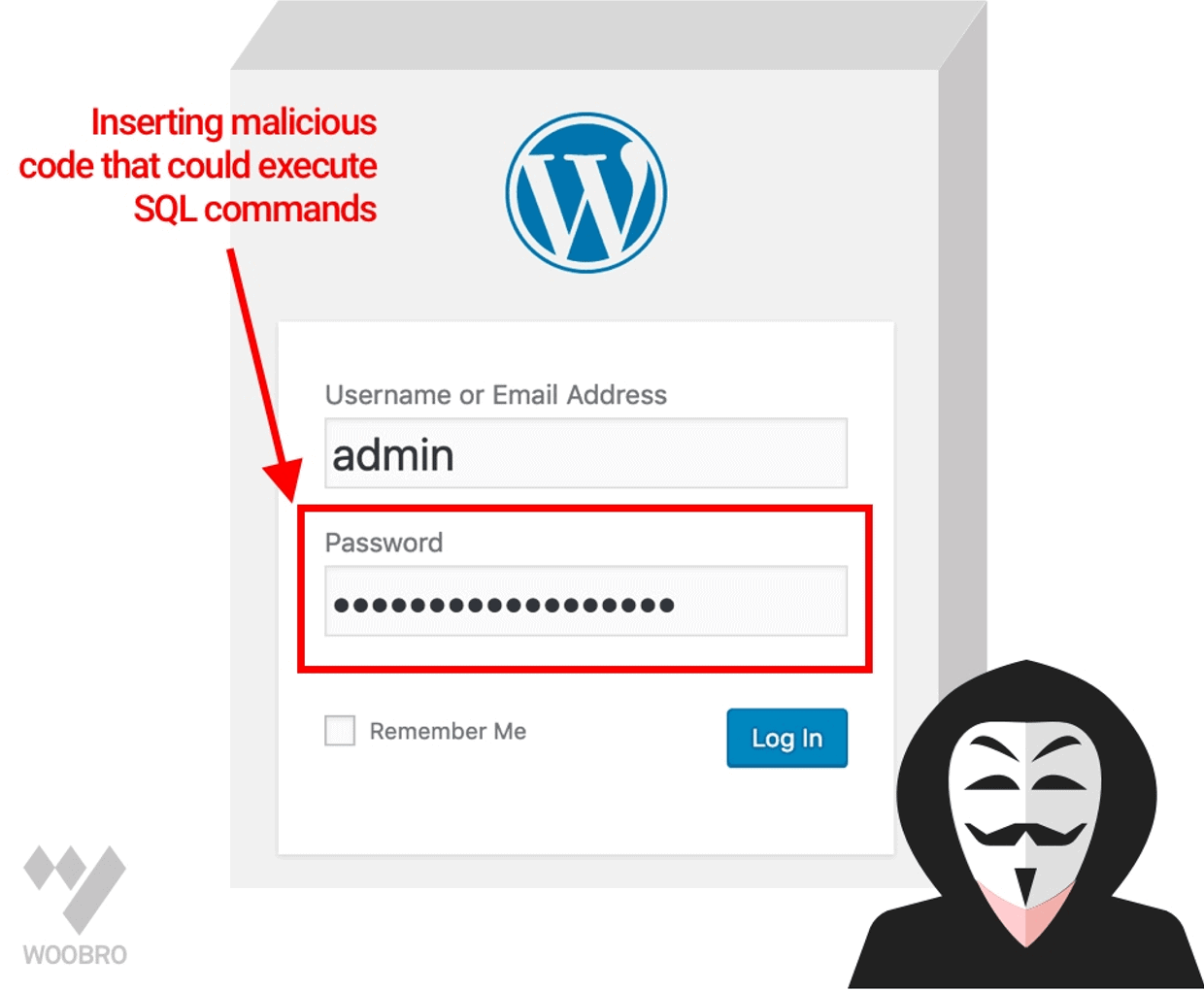
WordPress uses a MySQL database to work. The vulnerabilities SQL Injection in wordpress occur when a hacker accesses the WordPress database.
This way it further exploits all your website data. With one SQL Injection, a hacker can create a new one account admin level user. With its help, it gets full access to your WordPress site.
These types of threats can also be used to bring new data into your database, which includes links to malicious or unwanted websites.
4. Cross-Site Scripting (XSS)
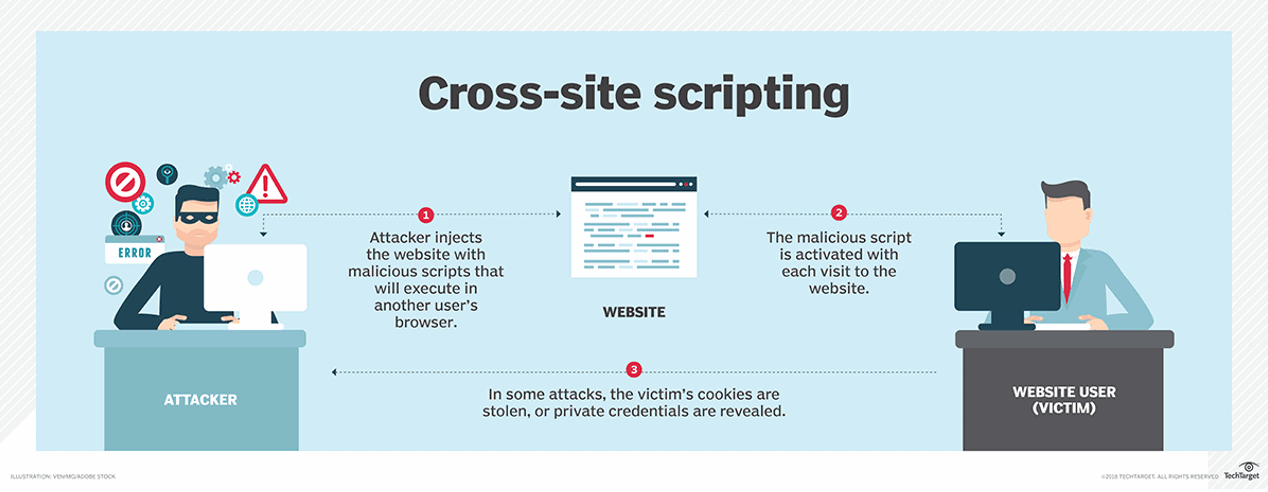
84% of all web site security issues are related to Cross-Site Scripting or XSS attacks. WordPress plugins are full of cross-site scripts.
Mechanism: When a user, knowingly or unknowingly, uploads web pages with insecure javascript scripts, these scripts are used to steal data from their browsers. An example of a Cross-Site Scripting attack would be a form of violation that appears to be on your site. If a user enters data into this form, that data will be stolen
5.Malware
Malicious software is code used to gain unauthorized access to the targeted site. These codes are entered into the site to collect sensitive data. However, there are thousands of types of malware infections on the internet. WordPress is not vulnerable to all of this.
There are four commonalities Malware infections in WordPress:
- Backdoors
- Drive by downloads
- Pharma hacks
- WordPress Malicious redirects
WordPress is aware all of these security issues. It gives the user various options and techniques to ensure security against cybercrime.
Secure WordPress with 3 easy steps:
WordPress Backup Solution:
Backups are your first defense against any security issues. Remember, nothing is 100% safe.
Installation one Web Application Firewall:
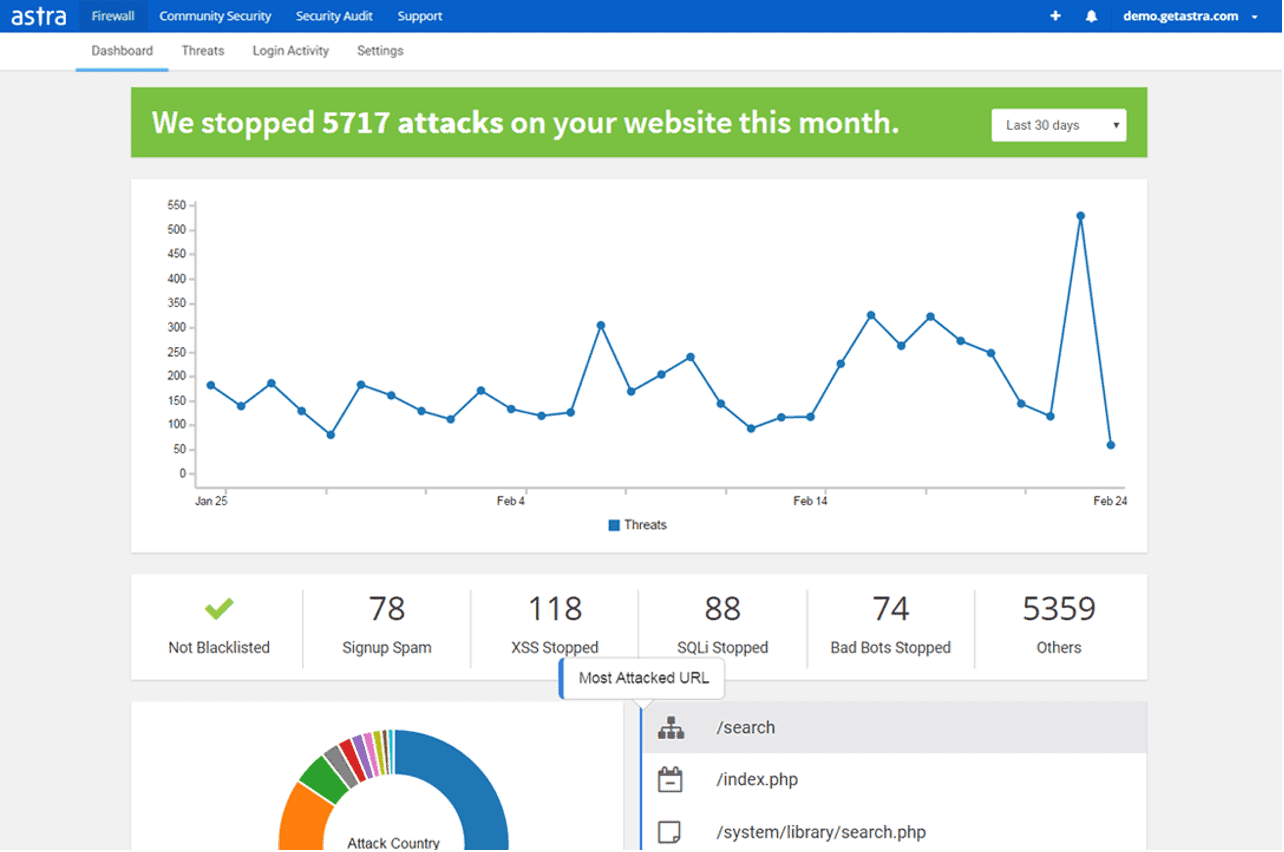
A Firewall blocks all malicious traffic before it even reaches your site. Web Application Firewall (WAF) is an application-level security solution that controls the traffic coming to your server. It takes the necessary action to protect it from hackers and malware.
Disable file editing:
WordPress has a built-in code editor that lets you edit the theme as you add it. These files can be edited directly from the WordPress admin area. If access gets into the wrong hands, it can cause a lot of security issues. Therefore, it is recommended that you disable this feature.
Waiting for your move
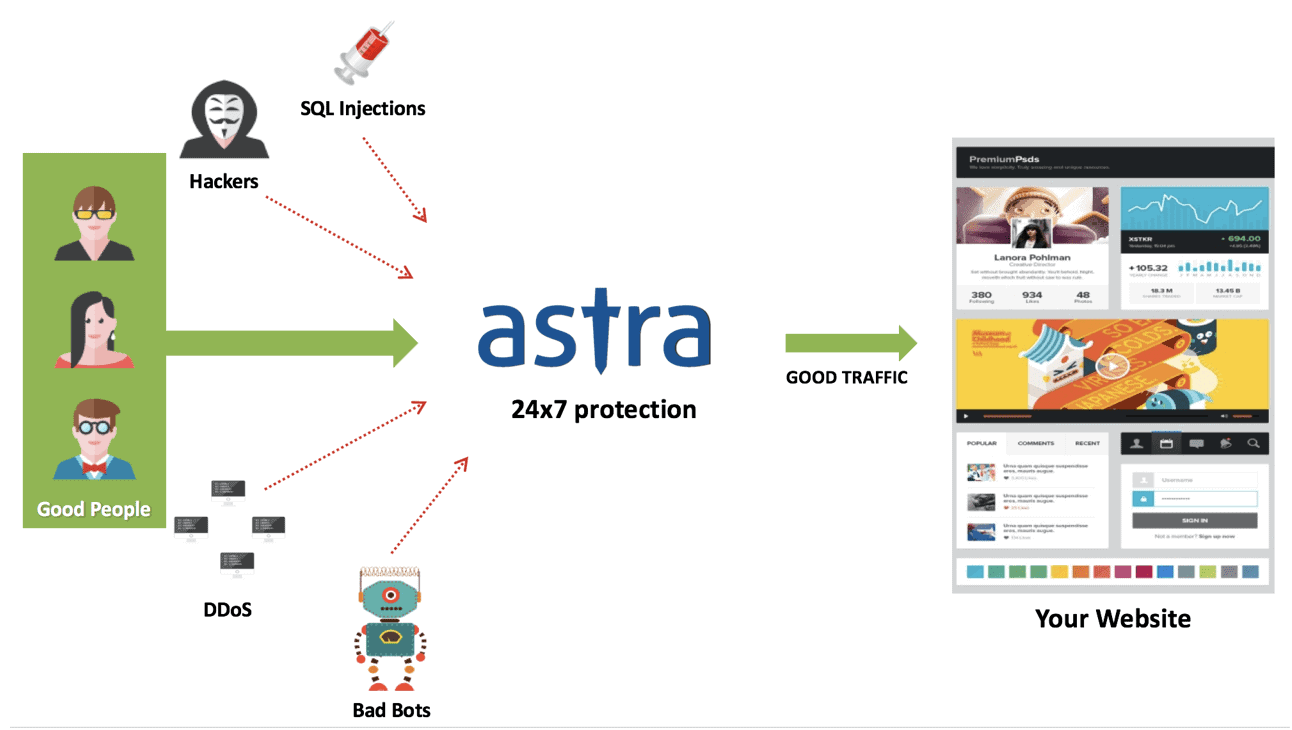
With all the details we mentioned, it is your turn to secure and fill all the security gaps on your site
So what are you waiting for?
Secure your page and manage it securely.





