A multifaceted approach to better safety of computers is important, such as using a combination of security devices in your home (doors, windows, alarms, cameras).
This means using anti-virus software, a firewall, ensuring that your operating system is up to date with dangerous websites and phishing attacks.

Passwords
Another key element of cyber security is having a strong password. Experts recommend using a password that is at least 8 characters long and contains a combination of alphanumeric characters. This means that it must contain lowercase and uppercase letters, numbers and symbols (such as # ?! * +).
Early computer systems were easily compromised by having weak passwords such as "admin" or "admin"Password".
Going to any office you will probably find a notepad with a computer password in at least one office. This is often because people have difficulty remembering passwords such as H4fTnQ91ifW, and therefore have to write them down. A more secure solution would be to use a password management tool such as Keypass, however, it is relatively unknown among techies.
The solution - Multi-factor security
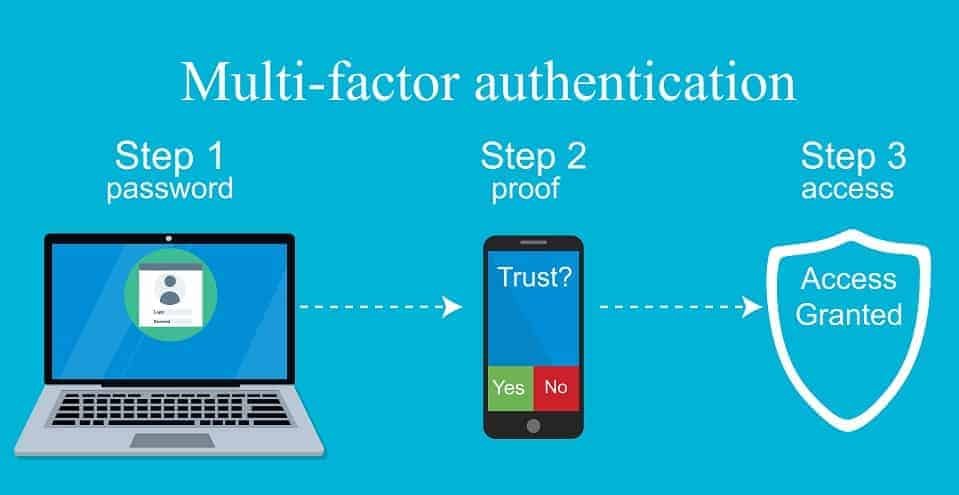
One solution to the password problem is the security of many factors. It is sometimes referred to as "two-factor security" or "two-factor authentication". This is a system where a user has to enter a third piece of information in order to log in.
Instead of being a static character string to be kept in the user's mind, this system creates a unique password that can only be used once. Popular examples include Google Verifier which generates a unique six-digit code every 30 seconds and is generated by the user's phone.
Using a multi-factor security system, a hacker may still not be able to access an account, even if it has a username and password.
The security of many factors has been widely adopted in recent years. It is possible to secure your online accounts with almost all major websites using this system. This includes social networks such as Facebook and gambling sites that use the popular validation technique SMS, while many large banks such as HSBC use a separate physical device.
The future of multi-factor security
While multi-factor security has already been successfully implemented in many parts of the internet, security experts and the public cannot be satisfied.
The improved security devices at cars they force thieves to change their approach from breaking into the vehicle itself to stealing keys from homes and unlocking the car that way. In the same way, multi-factor security forces criminals to change their approach.
The FBI recently issued a warning that hackers are stepping up their efforts to launch multi-factor security attacks or by transferring the victim's phone number to a SIM card they control so that they can receive authentication codes via SMS. Other techniques reported by the FBI include an approach that copies session cookies from the victim's computer so that they can reuse them on their own machine.
Therefore, a key battle in the future of multi-factor security will be to find and close these vulnerabilities before hackers can apply them. This is something that security experts have achieved so far.
Push Notifications

Facebook and Google use notifications push as a method of authentication by users in recent years. If you sign in to a Google Account, a pop-up window will appear on your smartphone asking if you are signed in.
They will probably be released on more systems in the coming years. They are cheaper than the physical devices still used by many banks and are also much more secure than SMS codes. The United States National Institute of Standards and Technology (NIST) recently announced that SMS authentication should be discontinued in the coming years.
Biometrics

Smartphones and some computers use biometrics like fingerprints and recognition person to allow us to log into our computers for several years. However, they are unlikely to become a critical part of multi-factor security.
Many security companies have turned off fingerprint scanners on devices they supply to their staff for many years because they are easily bypassed.
NIST says biometrics should be used in conjunction with another form of multi-factor security, as a person can be easily photographed without their permission or fingerprints being taken by an object being touched by users. Therefore, biometrics are not secret and are not strong enough to protect important data.
Multi-factor security has been a critical tool in the fight against cyber-attackers, and its effectiveness is being demonstrated by efforts to develop solutions to circumvent it.
We may see an increase in push notification systems in the future, along with SMS. However, it is unlikely that biometrics are based solely on the safety of our devices.





