Faraday introduces a new idea, IPE (Integrated Penetration-Test Environment). An IDE Penetration testing, designed to distribute, index, and analyze data generated during a security check.
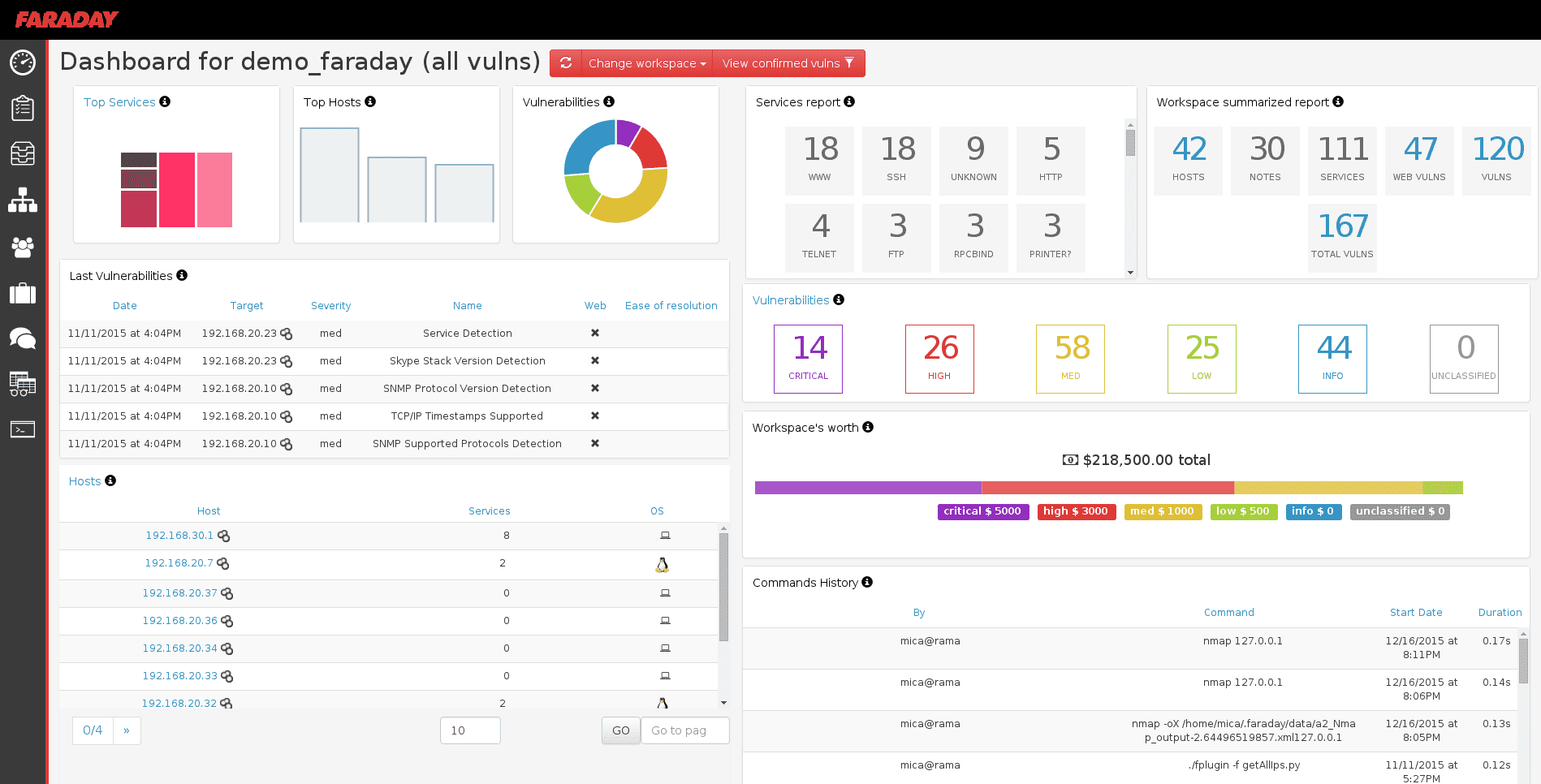
Faraday's main purpose is to reuse the available tools of his community and exploit them in a complex way.
Designed with simplicity, users do not notice any difference between their own terminal application and that included in Faraday.
It was developed with a specialized set of functions that help users to improve their own work. Faraday does the same thing to the IDE for you when planning, but from the perspective of a Penetration testing.
Plugins
Faraday works flawlessly, it currently has more than 50 tools, including the most popular Penetration testing platforms:

There are 3 types of plugins:
- Plugins that monitor commands, giving a direct command when a vulnerability is detected in the console. Be the whole n procedure automatically and requires no action from you.
- Plugins that import reports files. You must copy the reference to $HOME/.faraday/ report / [workspacename] (replacing [workspacename] with the real name of your workspace) and Faraday will automatically detect, edit, and add it to HostTree.
- Plugin for local or internet connections (BeEF, Metasploit, Burp), connected to external APIs or databases or connected directly to Faraday RPC API.
Application snapshots
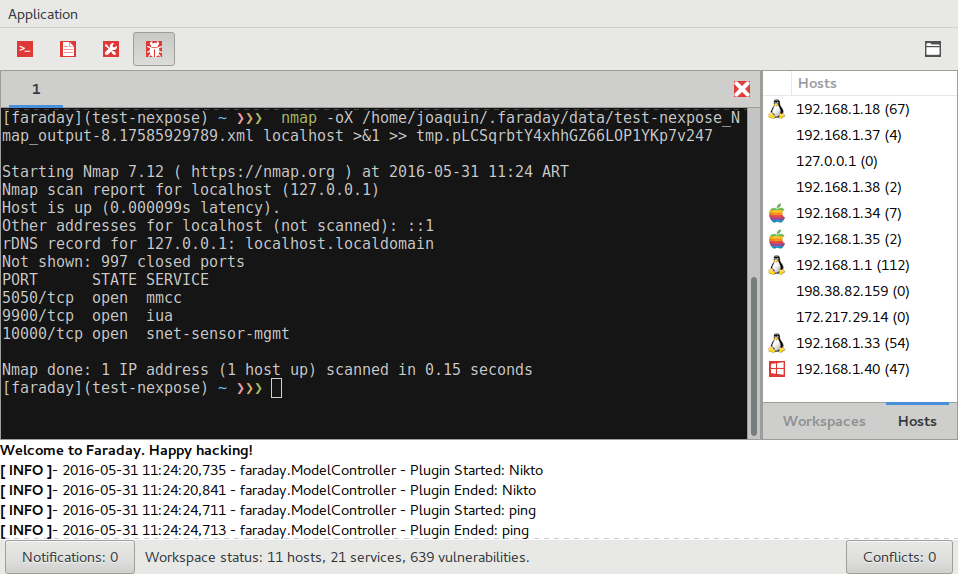
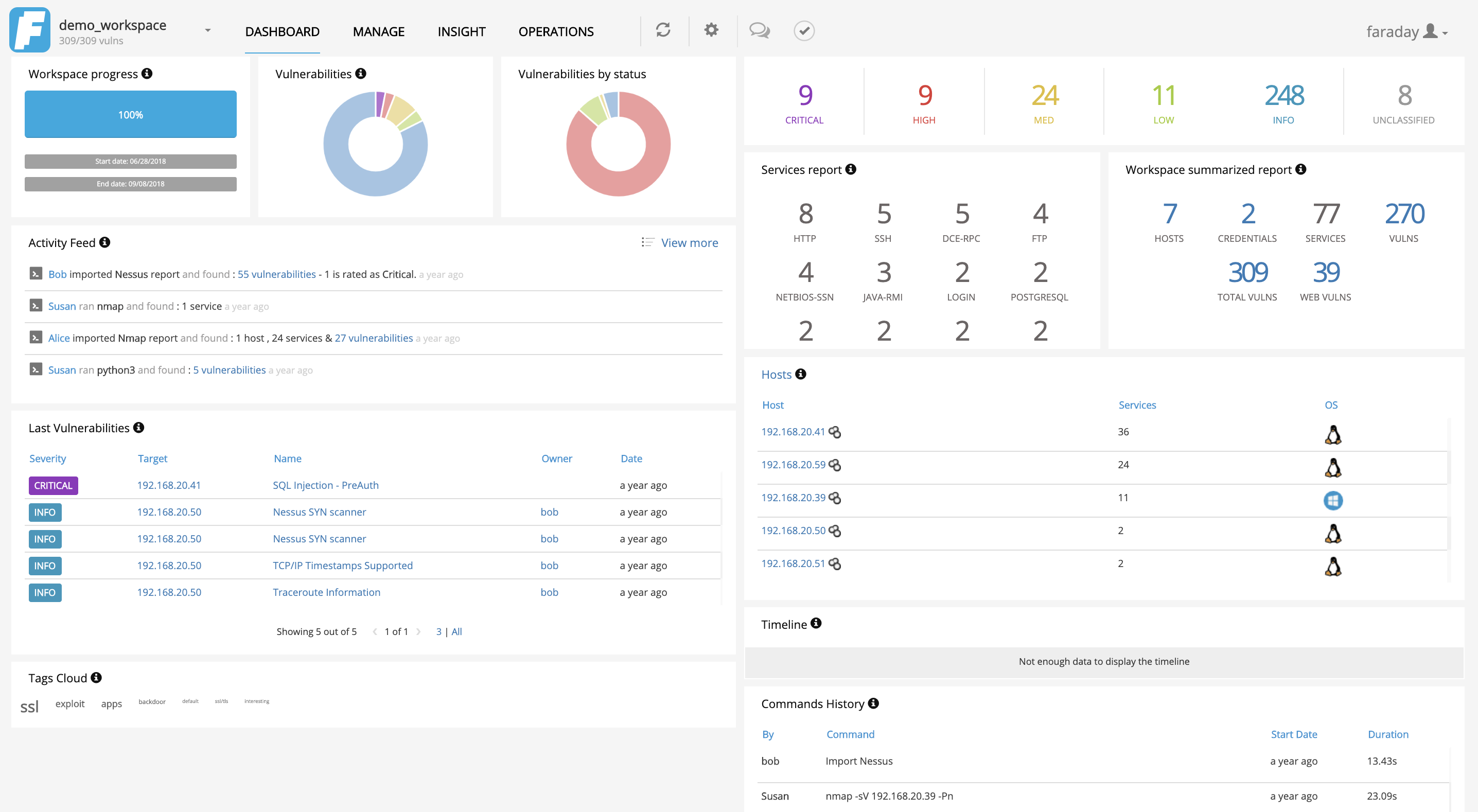
The program comes pre-installed on penetration testing distributions such as Kali or you can alternatively download it from here





