Universal Radio Hacker (URH) is a tool for analysis unknown wireless protocols. With the rise of the Internet and Things (IoT), such protocols appear frequently.
Many IoT devices operate on frequencies such as 433,92 MHz or 868,3 MHz and use proprietary communication protocols. Reverse engineering protocols can be exciting and reveal serious security leaks e.g. when bypassing smart alarm systems and door locks.
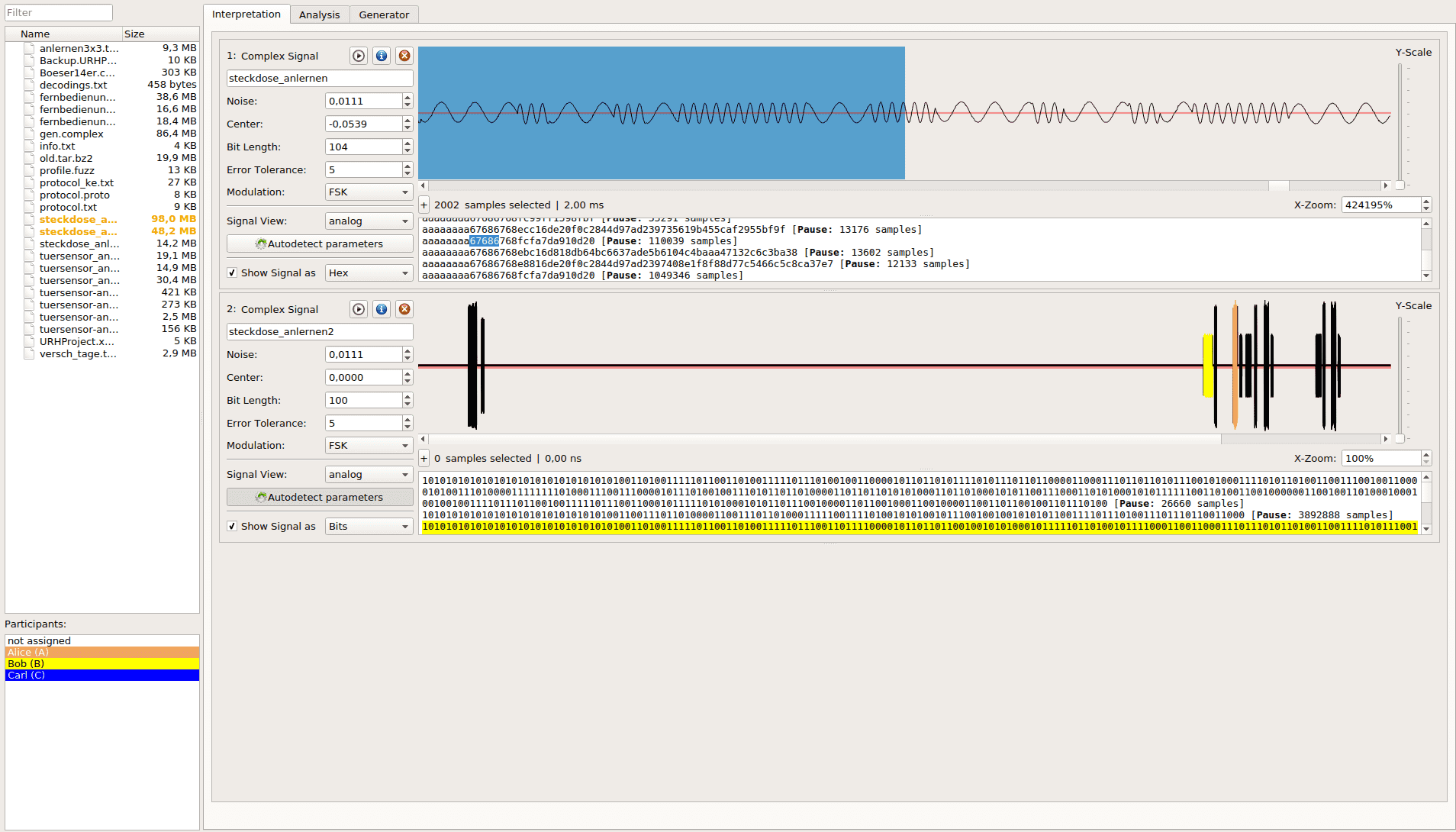
Universal Radio Hacker is software for exploring unknown wireless protocols. Features include:
- hardware interfaces for Radio software
- Easy demodulation of signals
- Retention of your data
- Customizable decodings to break even sophisticated coding such as CC1101
- Assign tags to reveal the logic of the protocol
- Fuzzy component to find security leaks
- Configuration support for data injection back into the system
As the name suggests, SDRs require software to function properly. This is where the Universal Radio Hacker comes in: It takes the samples from the SDRs and converts them into bits. But that's just the beginning: URH is designed to help you throughout procedure attack of the wireless communication of IoT devices.
In the following sections, you will learn how to useste URH and reverse engineering protocols in minutes.
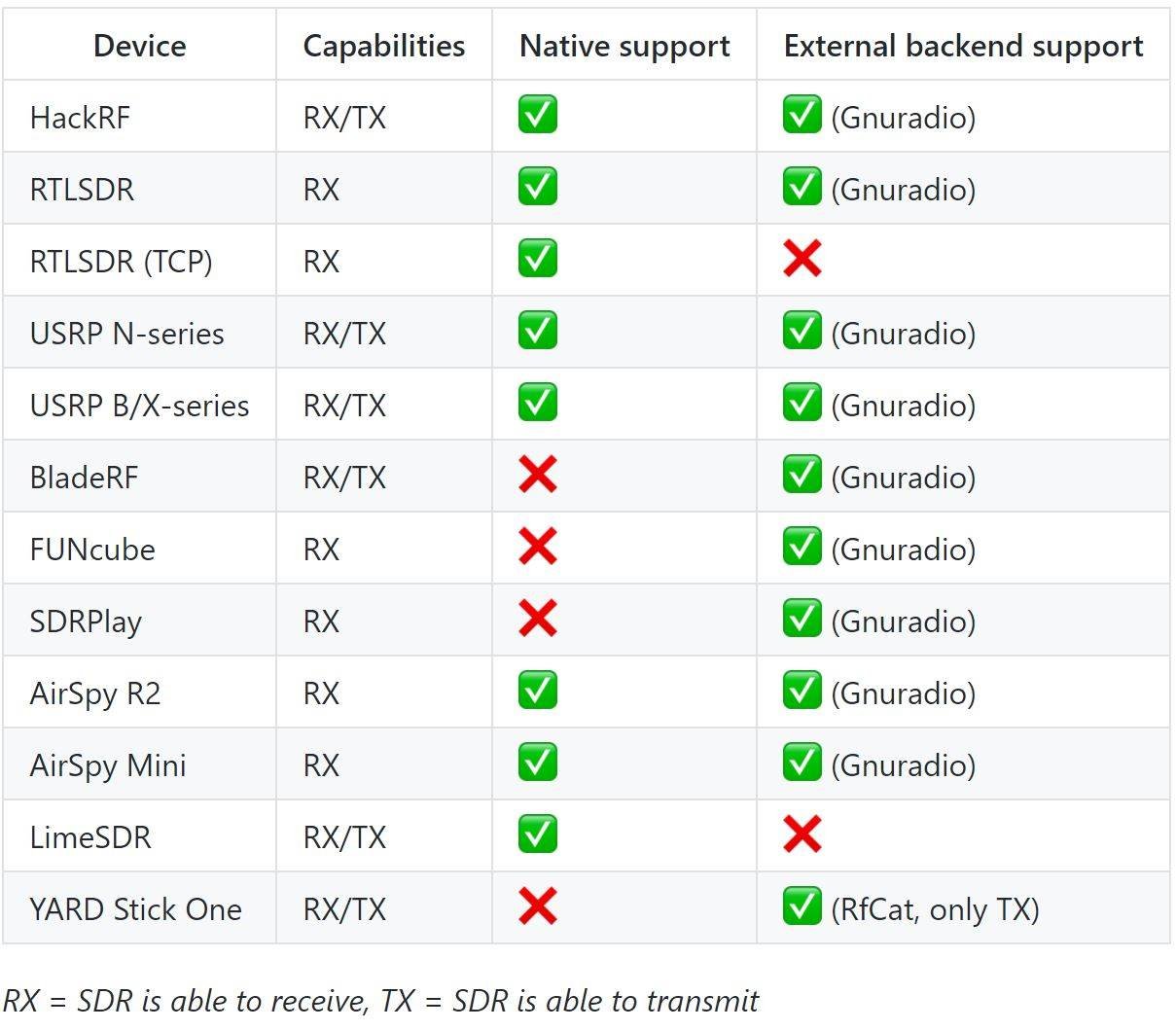
Supported devices
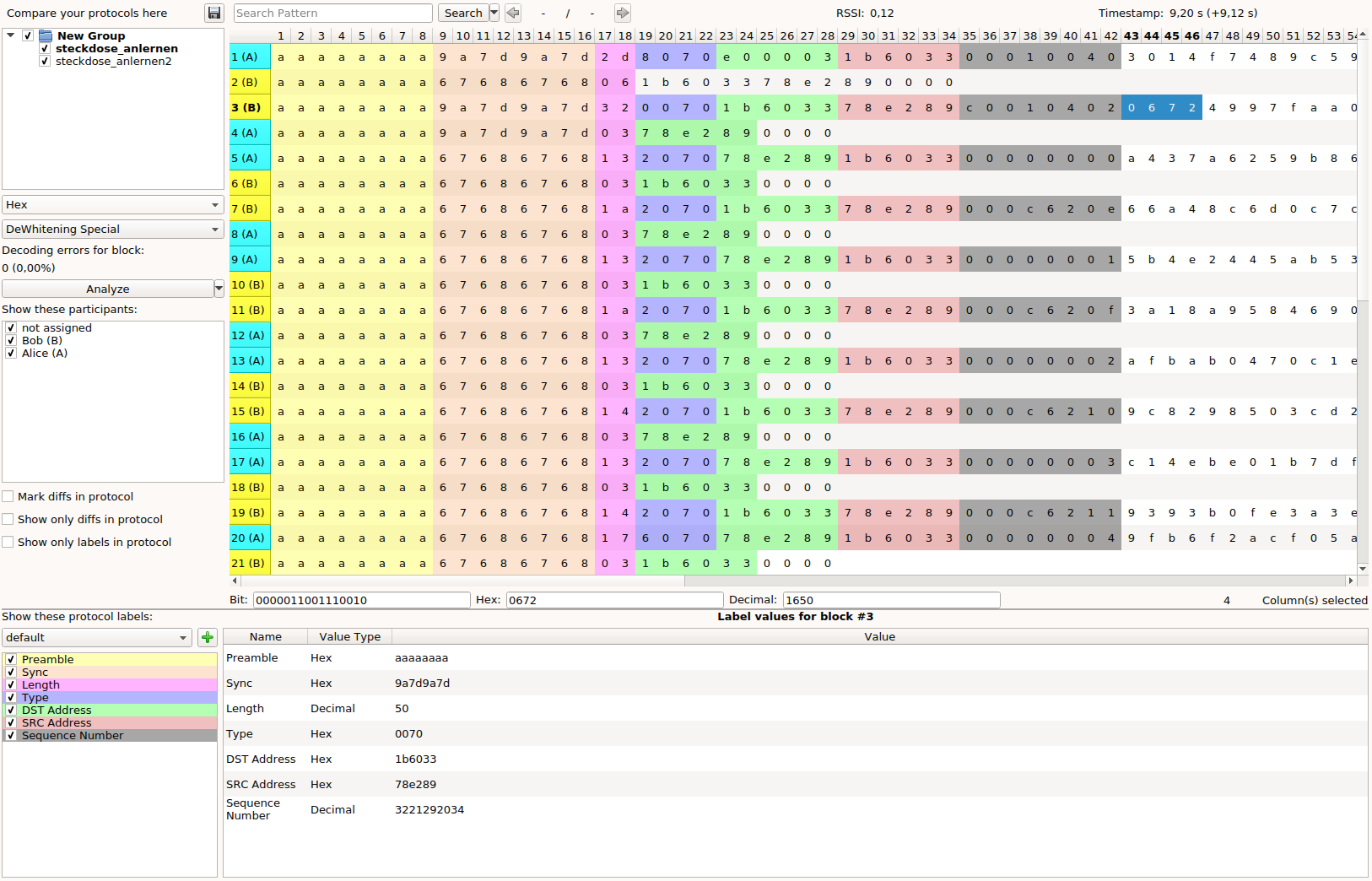
Snapshots applicationς
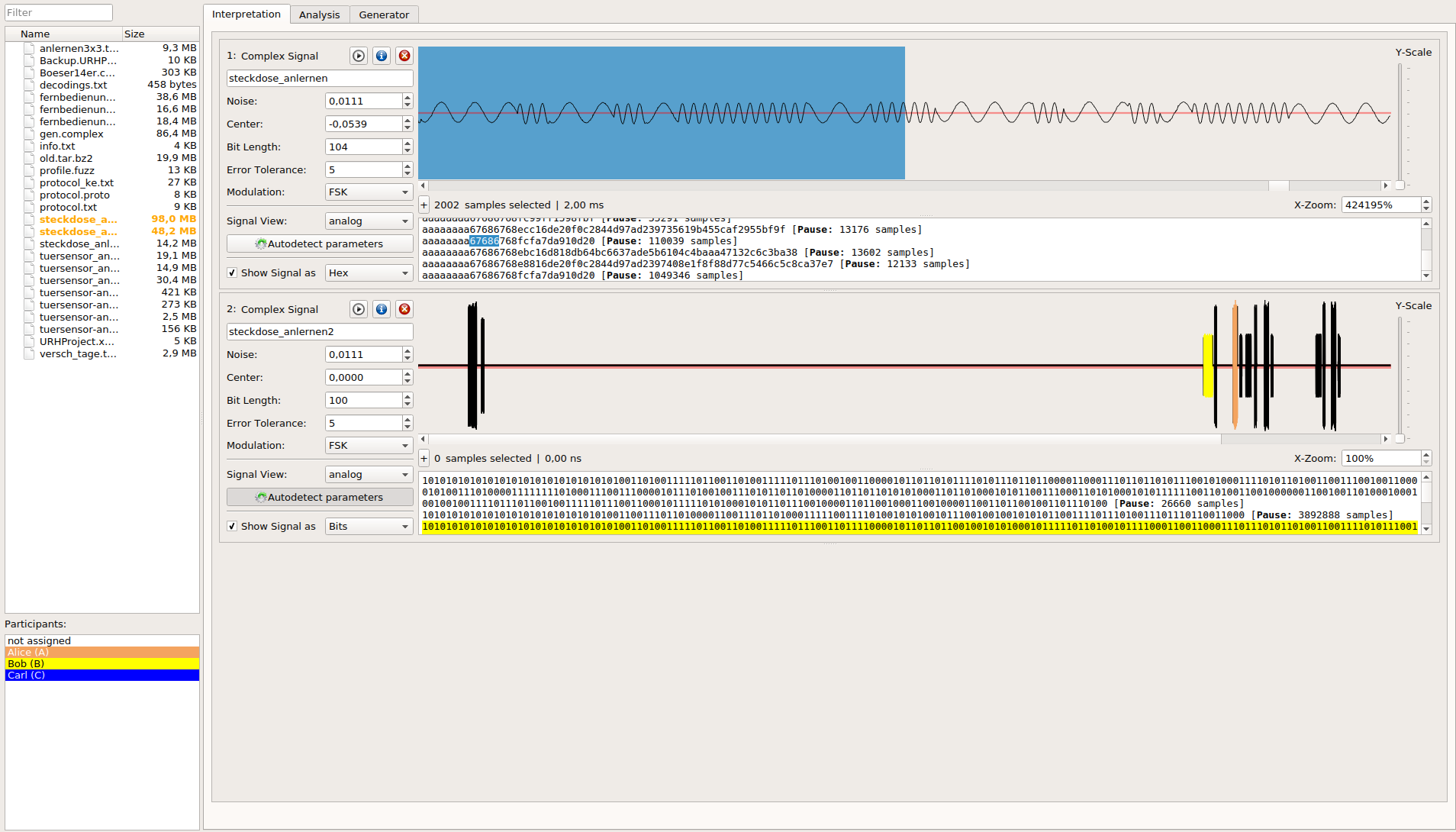

Instructions for installing and using the program can be found here





