The Network Security Toolkit (NST) is a bootable ISO image (Live DVD / USB Flash Drive) based on Fedora 28, providing easy access to leading Open Source Network Security applications and should run on most x86_64 systems.
The main purpose of developing this toolcases was to provide the security professional and network administrator with a comprehensive set of network security tools. Most of the tools published in the article: Top 125 Security Tools from INSECURE.ORG are available in the toolkit.
An advanced web user interface (WUI) is provided for system / network management, navigation, automation, network monitoring, host geographic location, analysis network and configuration of many network and security applications found in the NST distribution.
In the virtual world, NST can be used as a security analysis, validation, and monitoring tool on virtual enterprise servers that host virtual machines.
Specifications
- Multi-Tap Network Packet Capture
- Web-Based Network Security Tools Management
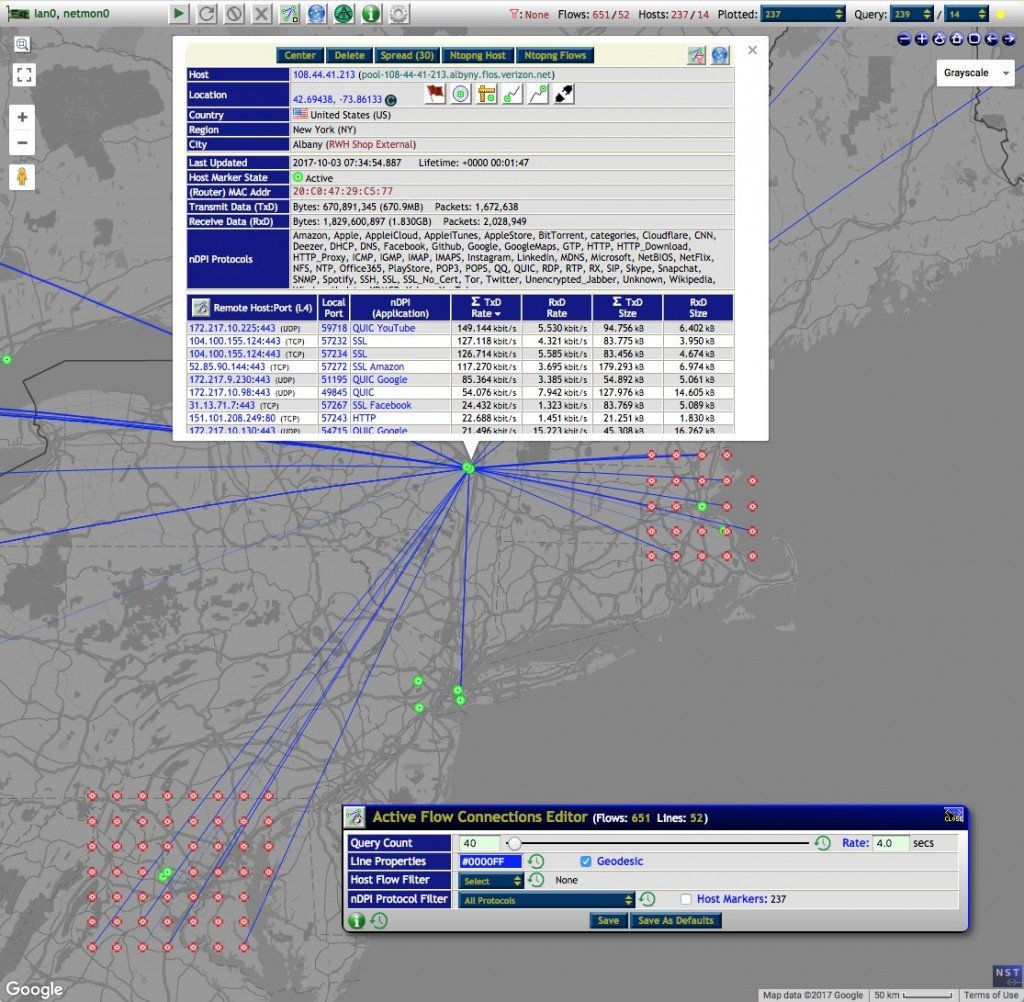
- Host/IPv4 Address Geolocation
- Network / System Monitoring
- Network Intrusion Detection
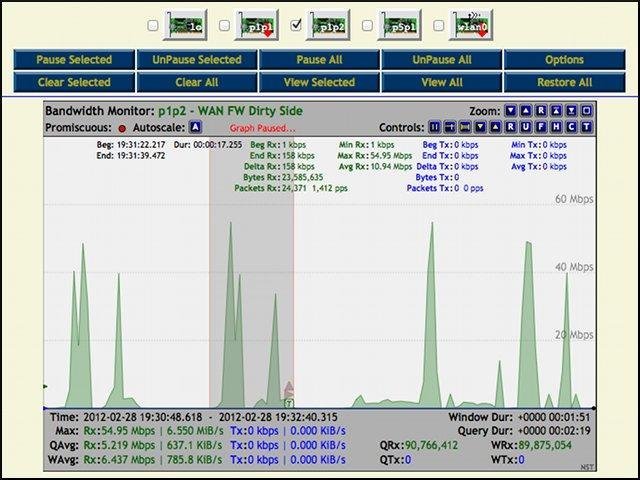
- Network Interface Bandwidth Monitor
- Web-based Snort IDS Integration
- Active Connections Monitor
- Network Segment ARP Scanner
- Network Packet Capture CloudShark Upload Support
- Multi-Port Terminal Server
- VNC / RDP Desktop Session Management
You can download the program from here.





