Lynis is one tool ελέγχου ασφαλείας ανοιχτού code . It is used by system administrators, security professionals, and penetration testers to assess the security defenses of Linux and UNIX-based systems.
It runs on the host itself, so it performs more extensive security scans than vulnerability scanners.
Supported operating systems
Lynis runs on almost all UNIX-based systems and versions, including:
- AIX
- FreeBSD
- HP-UX
- Linux
- MacOS
- NetBSD
- OpenBSD
- Solaris
- and other
It even runs on Appliances Raspberry Pi or QNAP.
Optional installation
Lynis is lightweight and easy to use. Installation is optional: just copy it to one system and use the "./lynis audit system" command to start the security scan.
It is written in a script shell and is released as open source software (GPL). Software packages are available from the project repository.
Use
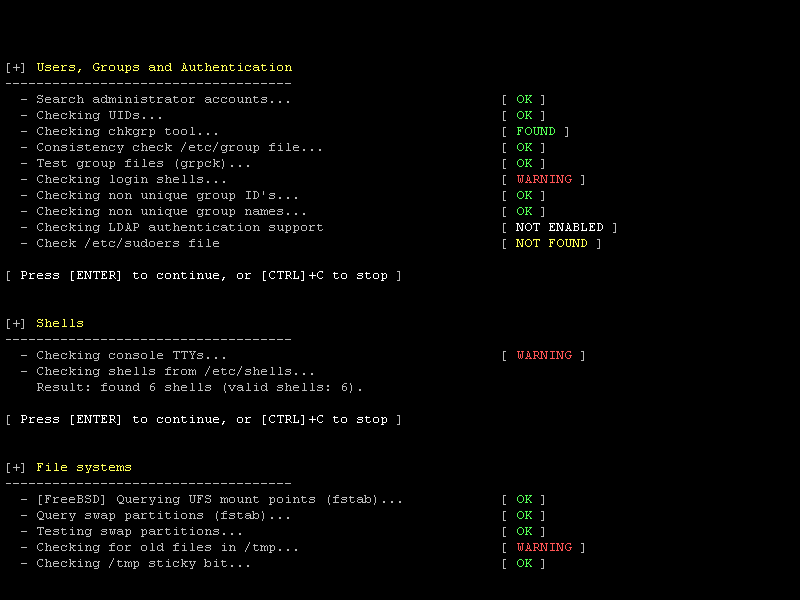
Performs hundreds of individual tests. Each test helps determine the security status of the system. What happens during a scan with Lynis:
Steps
- Identify the operating system
- Search for available tools and utilities
- Check for Lynis updates
- Perform tests with enabled plugins
- Perform safety tests by category
- Report the status of the security scan
In addition to the data displayed on the screen, all technical details about the scan are stored in a log file. Any findings (warnings, suggestions, data collection) are stored in a reference file.
Application snapshots
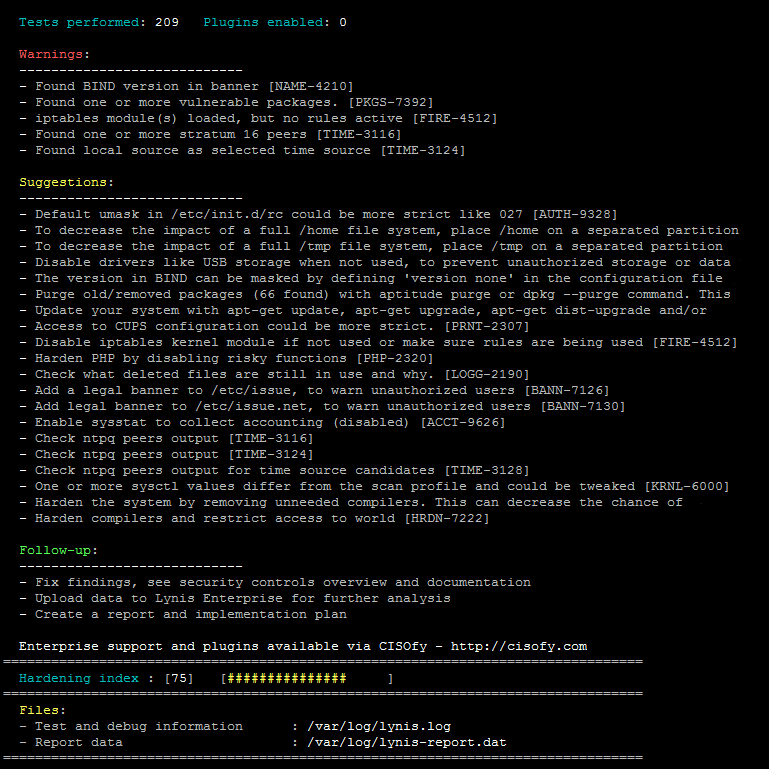
You can download the program from here.





