Cloudtopolis is one tool which helps us crack multiple hashes on the Google Cloud Shell platform, quickly and without any checks.
The program is free.

Conditions
A Google Account
Installation
The installation of Cloudtopolis takes place in two phases:
Phase 1
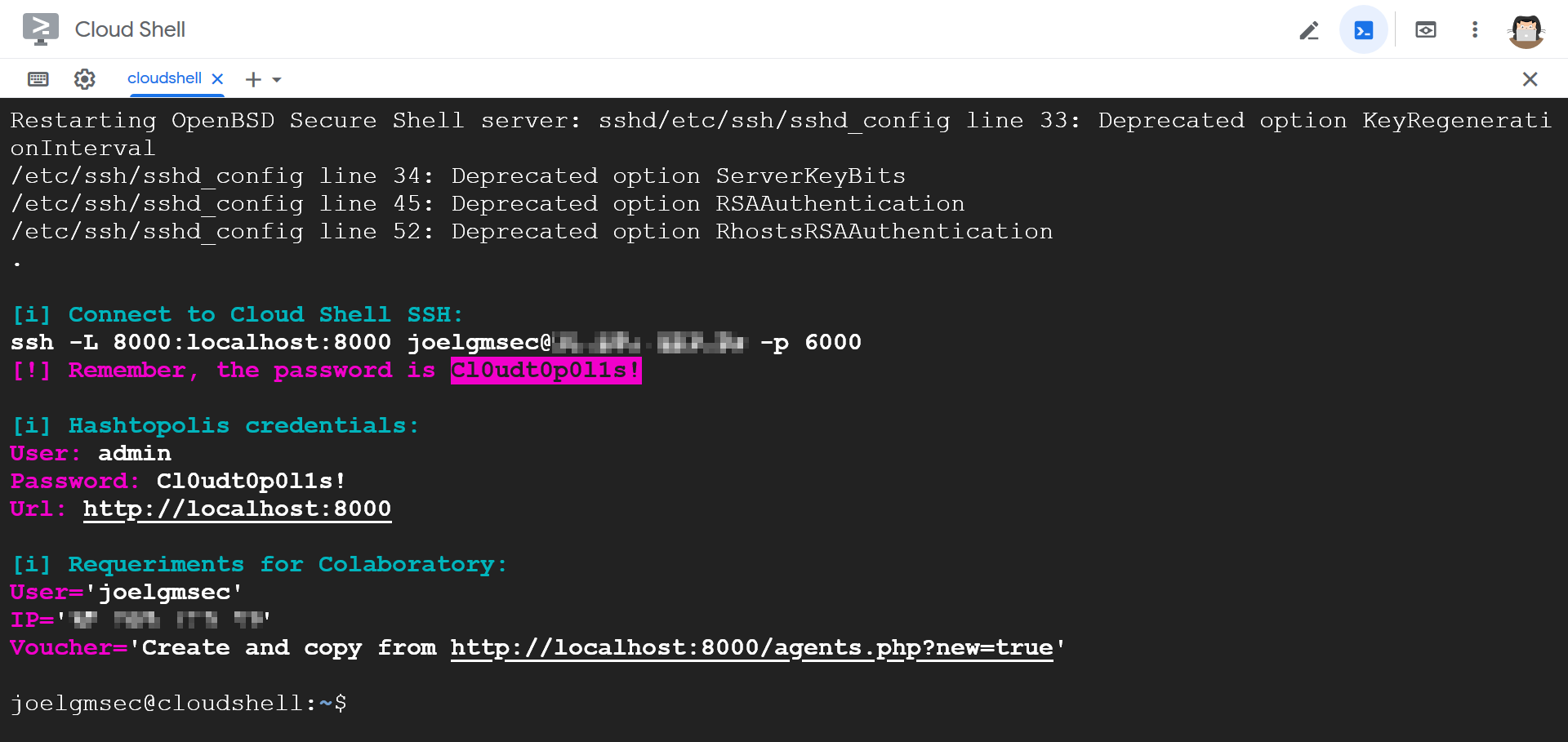
Get access in Google Cloud Shell from the link below:
https://ssh.cloud.google.com/cloudshell/editor?hl=es&fromcloudshell=true&shellonly=true
Then run the following commands in a terminal:
wget https://raw.githubusercontent.com/JoelGMSec/Cloudtopolis/master/Cloudtopolis.sh chmod + x Cloudtopolis.sh ./Cloudtopolis.sh
Phase 2
Access Google Colaboratory via the following link:
https://colab.research.google.com/github/JoelGMSec/Cloudtopolis/blob/master/Cloudtopolis.ipynb
It is necessary to fill in the fields in the “Requiriments” section with the data that you put in Google Cloud Shell and Hashtopolis.
You can also access Hashtopolis directly from the following url:
https://ssh.cloud.google.com/devshell/proxy?authuser=0&port=8000&environment_id=default
Or via an SSH tunnel, following the instructions that appear after running the first script.
Use
Once the installation is complete, more factors can be added, repeating phase 2 as many times as you want.
For this, it is necessary to use 1 Google Account for each execution of Colaboratory. It is not necessary to repeat phase 1 each time. You can also use other Google accounts if you have one or your friends' accounts.
Application snapshots
You will find a detailed guide for installing and using the program here.





