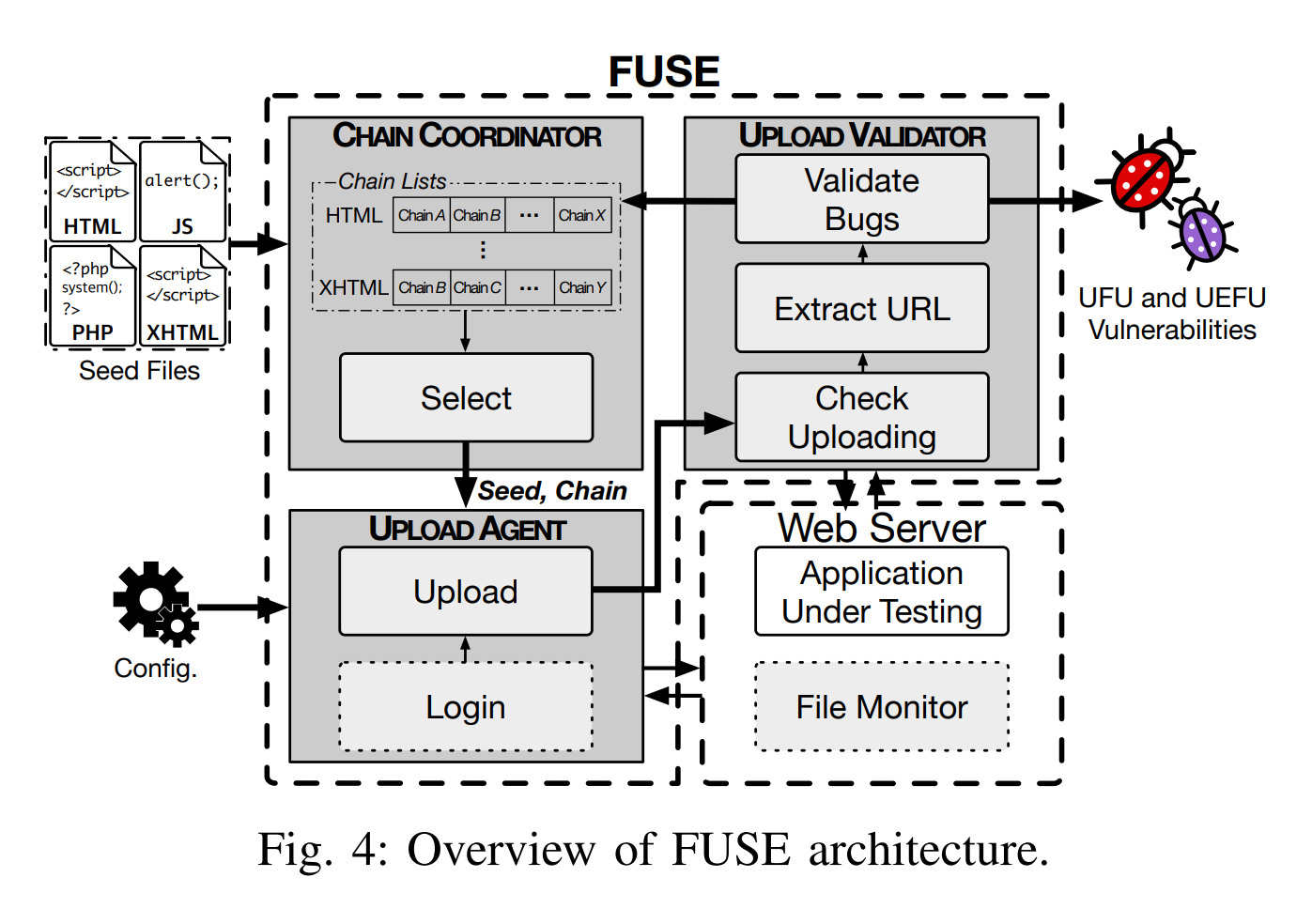
FUSE is a penetration testing system designed to detect Unlimitedrecut Executable File Upload (UEFU) vulnerabilities. Details of the testing strategy can be found at σελίδα us.
Installation
# apt-get install rabbitmq-server # apt-get install python-pip # apt-get install git
Use
Configuration
FUSE uses one file configuration set is provided by the user and defines parameters for a PHP application. The script must be completed before essay of a web application. You can view the file README and examples of configuration files .
Configure to monitor files (Optional)
$ vim filemonitor.py ... 10 MONITOR_PATH='/var/www/html/' Default port of File Monitor 12 EVENT_LIST_LIMITATION=8000Implementation
FUSE
$ python framework.py [Path of configuration file]File tracking
$ python filemonitor.pyResult
- When FUSE completes the penetration test, a [HOST] directory and a [HOST_report.txt] directory are created.
- A [HOST] folder stores files that have been uploaded.
- [HOST_report.txt] file contains test results and information related to U (E) FU-enabled files.
You can find the program here.





