PeaceMaker Threat Detection is one auxiliary program (kernel-mode utility) designed to detect various methods commonly used by advanced forms of malware.
Compared to a simple antivirus, PeaceMaker targets the techniques that usually uses the malware to "catch" it while it's running.
In addition, PeaceMaker is designed to provide incredible detail when detecting a malicious technique, allowing for more effective containment and response.
Specifications
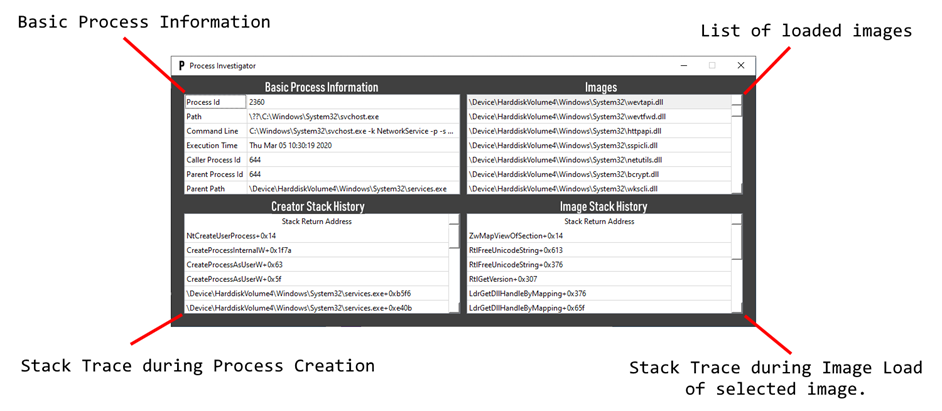
- See which code started a process (stack trace).
- See which code loads an image in a process (stack trace)
- Detect uncharted (hidden) code through common Stack Walking features such as:
- Creation process
- Upload image
- Creating threads
- Detect remote thread creation.
- Detect parental process identity forgery.
- Detect threats in unmatched (hidden) code.
- Block basic breach functions in the GUI client.
- Block file system/registery, record, delete, or perform operations that violate a user-defined filter.
- Detect file / registry, write, delete, or perform functions that violate a user-defined filter.
- Records the source process and stack of operation.
- Filter for known false positives.
Remarkable properties
- Meticulous analysis of the code.
- All detection routines are in the kernel driver.
- Designed to detect user-mode malware.
- Tested using Driver Verifier standard configuration
- Tried putting it on my daily laptop and watching for problems (nothing happened).
Information on installing and using the program, you will find here.