Digital forensics is the application of research techniques to solve digital crimes, from viruses that hold your computer and ransom data to intrusions that redirect customers to alternative sites.
Forensic scientists can analyze the available data to help solve these crimes.
The forensic scientist can help you identify what really happened as well as identify the perpetrators. Digital "forensics" can be employed by law enforcement agencies or even private companies to help them understand how they receive an attack and what they can do to shut down security gaps.

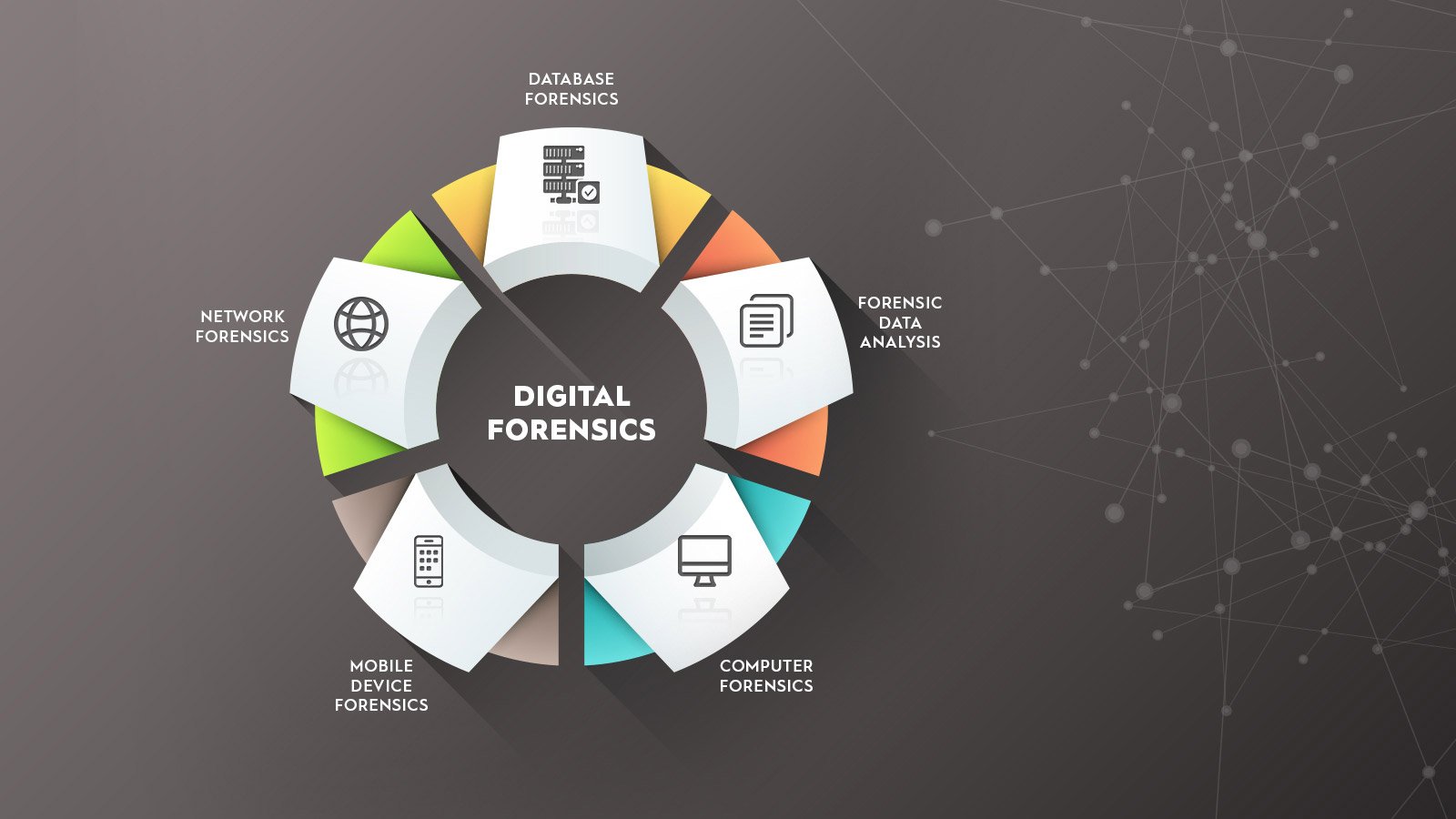
What are the different phases of Digital Forensics?
Digital forensics is a science in itself. As with all scientific investigations, they must be carried out in a methodical manner. There are several frameworks that can be used during the processtreatment of an investigation. But the following are probably the most commonly used and easiest to understand:
- Recognition: In order to be able to start your research, you need to know exactly where to look. This first step determines where the data you need will be stored. This could be anything from mobile devices to servers. You also need to think about where these devices are located and who will be managing them.
- Keep: you need to keep the information you need for your research. This could mean physical protection of the devices from further use, as well as taking photos and other information about the "crime scene". You will want to document everything, including how the evidence was collected.
- Collection: this can include everything from copying data to printing. Often, this can really require the removal of drives or portable equipment to access the information you need for your research.
- Analysis: here comes your expert. He uses his skills and experience to examine the available data and evidence to determine what really happened. He will be able to draw useful conclusions based entirely on the available data.
- Report: If the investigation is part of a criminal investigation, then it is vital that the information is presented in a formal manner that cannot be challenged by others. The methods used should be able to reproduce the same results for any other researcher reviewing the available data.
How does digital criminology solve cybercrime?
We all use digital devices and many will find application developers to create tools that users will use to communicate with each other. However, there are always those who will want to use application developers for more "ugly" tasks. There are those who will create apps for the purpose of stealing information from us without our knowledge. THE codes can be hidden inside complex applications which can be difficult for users to detect. Forensics can be used to detect any malicious use, as well as to identify who are the people who benefit from the collected data.
Others may use applications that are readily available to commit crimes. For example, the spread of child pornography or even terrorism. While you may be hiring application developers to create something that you think is completely innocent, be aware that some may find ways to use this application for other purposes.
From local police to federal investigators, they are increasingly turning to digital forensics. There is a wealth of information stored on our devices that can be used to indicate someone's intent to provide information about where they were at the time of a crime.
No matter how much smart may think they are a criminal, they often leave behind information that a good criminologist can uncover. They can do everything from cracking passwords to recovering information believed to have been deleted or encrypted. This can provide the information needed to convict the criminals in question.
But, like any information that can be used in court, it must be strong, how to recover a deleted file or how to read the encryption can have a significant impact on whether this information can be used. That is why there is a real need for specialized "medical examiners" on the internet.
Qualified researchers are considered experts in their field and their reports can be used in all cases, from fraud to murder. Criminology is no longer just about finding the causes of security breaches, it is a fast-growing and respected career path for those who want to do something a little different in computer science.

Would you like a career in cybercrime?
Whether you want a role in Internet security within a company or you want to work in law enforcement, there are many opportunities out there for those who specialize in digital forensics. It is a growing sector that offers more and more opportunities.
Criminals become more complex in how they commit fraud and other cybercrime. This makes the role of the digital forensics team more difficult. So if you are looking for a challenging career that will really interest you, then you might be interested. Look for it.





