Every year, hackers and researchers ασφαλείας συρρέουν στο Λας Βέγκας για το συνέδριο ασφαλείας του Black Hat (και μερικοί παραμένουν για το DEF CON), για να δουν και να μοιραστούν τις τελευταίες έρευνες ασφαλείας.
This year, everyone had to stay home because of COVID-19, but there was still a lot to worry about attending this year's conference.

Work like Black Hat from home
The ongoing COVID-19 pandemic in the US has hit many security infrastructures from what appeared to be. This year, both Black Hat and DEF CON (along with HOPE 2020 and others) used live and pre-recorded video in conjunction with chat platforms.
It worked surprisingly well and could be a model for other rallies to follow.
That said, the experience did not have the fun of a personal event and it is difficult to devote time to a video session when you need to take your dog for a walk. Let's hope that 2021 will be a beautiful year for all of us.
Watch the "trackers"

It has long been known that law enforcement (and others!) Use mobile phone tracking devices in real time and in some cases even to block data from these devices.
Some are called IMSI catchers. All of these devices operate under the guise of cell towers to deceive the connection of mobile devices.
Φέτος, η EFF παρουσίασε τον Crocodile Hunter, ένα εργαλείο που εντοπίζει ύποπτους πύργους σε πραγματικό χρόνο. Οι ερευνητές έθεσαν επίσης μια τολμηρή πρόταση να σταματήσουν εντελώς τις χειρότερες χρήσεις τους: Η Apple και η Google θα πρέπει να κάνουν χρήση του φτωχού φάσματος 2G για μεγαλύτερη ασφάλεια.
Easy data interception via satellites

Η espionage on a Wi-Fi network is difficult because you have to be quite close to your target. But not with Internet via satellite.
Information is often not encrypted, can be intercepted with very cheap equipment and contains extremely valuable information. And a VPN can not help because of the special speed modifications used by satellite ISPs. Fortunately, the researchers have come up with their own solution to this problem.
Arrest for legal intrusion

Justin Wynn and Gary Demercurio were hired to do some “penetration tests”. Βασικά, πραγματικές επιθέσεις έκαναν για να δουν αν θα μπορούσαν να εισέλθουν σε κυβερνητικά κτίρια παρά την ασφάλειά τους και από τη στιγμή που ήταν μέσα, να ελέγξουν ότι τα συστήματα των υπολογιστών που βρίσκονται εντός, αν είναι σε θέση να προστατευτούν.
All of this was in progress, with permission from the state of Iowa and the knowledge of the local authority, but a sheriff arrested the couple for this "intervention".
Solving puzzles…

Matt Wixey creates puzzles, not just because they are fun, but because he believes that puzzles can make you a better solver. And what is hacking other than complex problem solving?
Violation of public opinion and censorship

Renée DiResta of the Stanford Internet Observatory spends a lot of time thinking about how government agencies use the Internet to advance their goals.
In its presentation, it showed that while China has a huge army of online accounts, Russian Internet companies have been much more efficient with much less investment.
The good news: An event chain is used to make online effects effective, which means that the chain can be broken.
The bad news is that Russian "memes" really work.
Light bulbs may have "ears"…

If you plan to have a secret conversation, you may need to do it in the dark… This is because researchers have developed a way to capture small changes in light caused by the sound of a light bulb.
With some know-how, the sound can be reconstructed from a long distance. Researchers have named their creation Lamphone.
What are the Russians doing in the US elections?

The Americans had a close look at what Russian interference in the 2016 election looked like, but it was not the first time Russia had intervened in the US system. Nate Beach-Westmoreland controlled a decade of Russian military intelligence operations and found many of the same tactics the Americans saw in 2016: Defamation of officials, hackers and information leaks and dissemination by playing on existing cultural sections.
The Spectra fights with Bluetooth and Wi-Fi

Your phone, computer, and smartwatch should communicate wirelessly through many different radio frequencies, and these radio frequencies should avoid communicating with each other.
This is called mechanism of coexistence and researchers have shown how access to Bluetooth or Wi-Fi can use this coexistence to extract information, turn off communications and even send certain machines to a tailspin. It's an attack called Spectra.
A closer look at the Kr00k
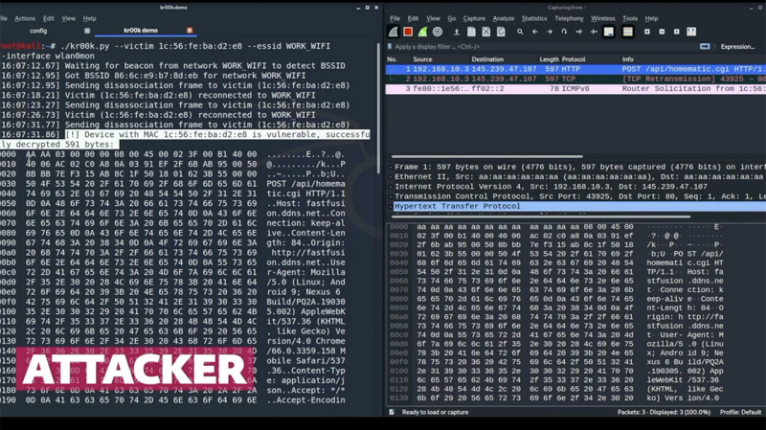
Robert Lipovsky and Stefan Svorencik from ESET have long considered the vulnerability of Kr00k, which was revealed a few months ago. This attack leverages the security features of Wi-Fi, so that some packets are sent with an extremely insecure multi-zero encryption key.





