A IP address - web protocol address (English IP address - Internet Protocol address) is a unique number used by devices on a network computers which uses the Internet Protocol standard for mutual recognition and communication.
TCP and UDP are the two basic Internet protocols used to exchange data between two computers. Each TCP and UDP packet in addition to the data includes a header that lists the packet characteristics.
Among them one can locate the port of the sender, from which the package started, and the port of the recipient, to which it is directed. Once the package is delivered to the appropriate port of the recipient, then the corresponding application receives it and uses the data contained in it.
(WikiPedia source).
Here are some ports you will find during procedure of the scan:
- Port 21 - FTP (File Transfer Protocol)
- Port 22 - SSH (Secure Shell)
- Port 23 - telnet
- Port 25 - Simple Mail Transfer Protocol (SMTP)
- Port 53 - DNS (Domain Name Server)
- Port 80 - HTTP (Hyper Text Transfer Protocol)
- Port 110 - POP3 (Post Office Protocol)
- Port 143 - IMAP (Internet Message) Access protocol)
- Port 443 - HTTPS (Secure Hyper Text Transfer Protocol)
Scan open ports with the ss command
The ss command works like any command on the Linux platform. The ss command is used to reject dump socket statistics and displays information in a similar way (though simpler and faster) as the netstat we will see below.
The ss command can also display even more TCP and status information from tools such as netstat or lsof.
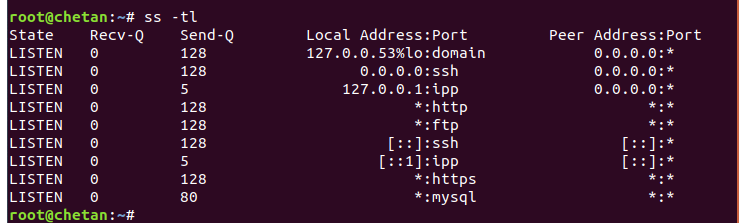
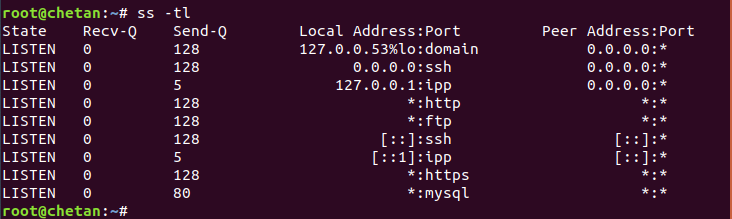
To display listening TCP connections using ss, the command is:
Mandate: ss -tl
Where, t means TCP port and l means listening sockets.
To view the listening UDP Connections, the command is:
Mandate: ss -ul
Where u means UDP port.
And in case you want to display TCP and UDP connections, the command is:
Mandate: ss - lntup
Where p means the name of the process
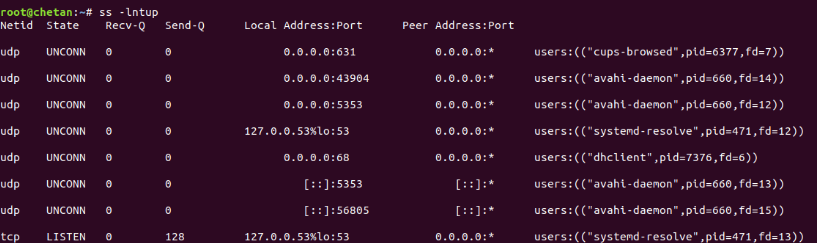
If you want to display all socket connections, then you can just use the ss command.
Scan open doors with netstat
Netstat comes from the words network and statistics is a program that works through the command line.
Provides basic statistics for all network activities and informs users about which ports and addresses the corresponding connections are running on (TCP, UDP) and which ports are open for work.
To check all open ports with netstat, the command is:
Mandate: netstat -pnltu
Where p stands for service-related process ID, n stands for the port number you are running, λ stands for listening sockets, t stands for TCP connection, and u stands for UDP connection.
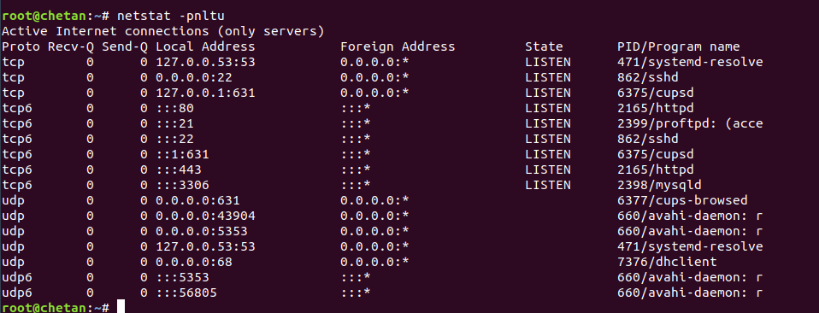
On Windows operating systems, you can use the netstat services via the command line (cmd.exe).
Scan open doors with lsof
Lsof is a command line utility for all Unix and Linux systems and helps us locate all open ports.
The lsof command is mainly used to retrieve information about files opened by various processes. Open files on a system can be of different types such as disk files, network sockets, named pipes and devices.
To display open ports, type the following command:
Mandate: lsof -i
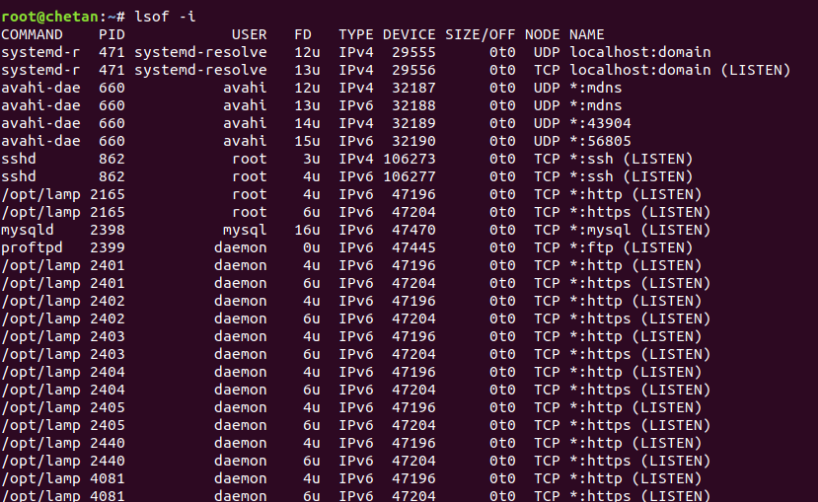
And in case you want to display only the open sockets, then you can use the following command:
Mandate: lsof -n -P | grep LISTEN
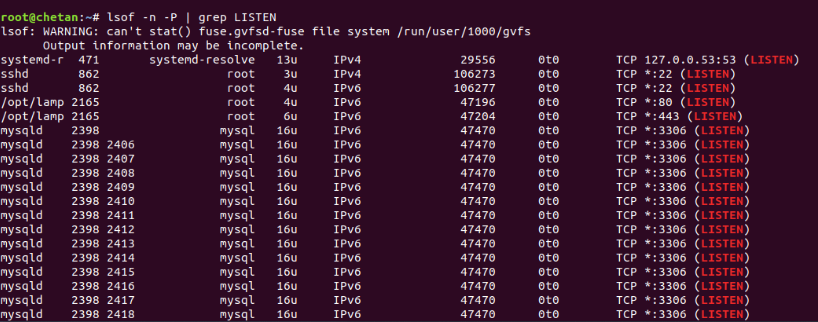
To display only TCP connections, enter:
Mandate: lsof -i tcp

Scan open doors with Nmap
Nmap is one of them free, open network security scanners, commonly used to locate devices within the network and to monitor the security of the network itself. Among other things, you can also use NMAP for scanning open ports and monitoring network servers.
In Kali Linux, Nmap is already pre-installed, but in case you use it Ubuntu or any other Linux distro, you can install Nmap by typing the command “sudo apt install Nmap”.
For the Windows operating system, the Nmap installation package comes with a front-end Nmap GUI called Zenmap.
To scan open TCP ports, type:
Mandate: nmap -sT -O localhost
The above command will start a TCP connection scan on the destination host. A TCP connection scan is the default scan performed if TCP SYN cannot be scanned. This type of scan asks the underlying operating system to try to connect to the host server / port.
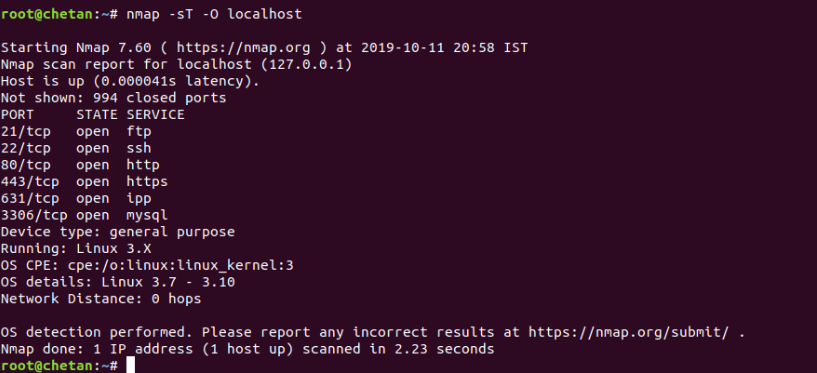
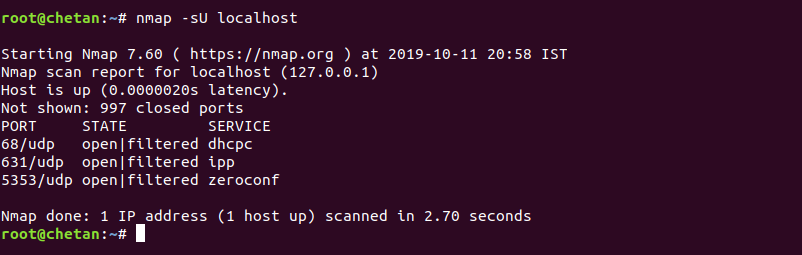
And for UDP, the command is:
Mandate: nmap -sU localhost
The above command will start a UDP port scan on the destination host. A UDP scan sends a UDP packet to the destination ports. If a response is received, the port is classified as "Open". If no response is received after multiple transmissions, the port is classified as "open / filtered".