A set of actions to help you execute a brute force attack with a dictionary at a WPA3 access point. Wacker utilizes the wpa_supplicant control interface to control daemon functions and to collect target information during brute force process attempts.
Useful files
The wacker has many details. Its files are in the path / tmp / wpa_supplicant /
- wlan1: one end of the uds
- wlan1_client: one end of the uds
- wlan1.conf: initial wpa_supplicant conf needed
- wlan1.log: supplicant output
- wlan1.pid: pid file for the wpa_supplciant instance
- wlan1_wacker.log: wacker debug output
Use
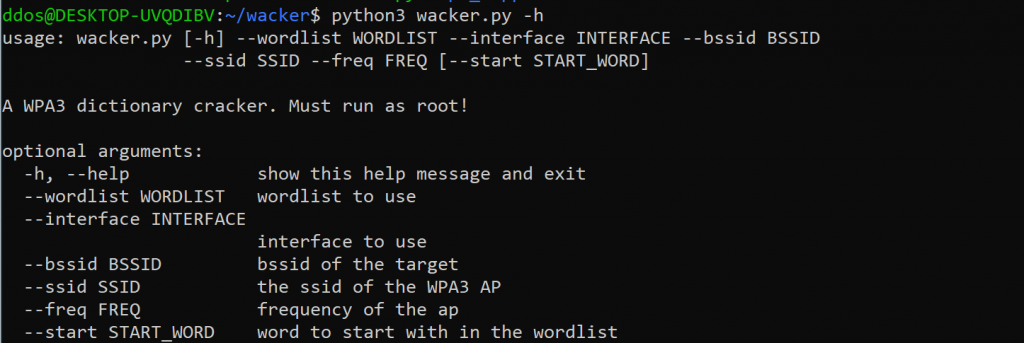
# ./wacker.py --help usage: wacker.py [-h] --wordlist WORDLIST --interface INTERFACE --bssid BSSID --ssid SSID --freq FREQ [--start START_WORD]
A WPA3 dictionary cracker. Must run as root!
optional arguments: -h, --help show this help message and exit --wordlist WORDLIST wordlist to use --interface INTERFACE interface to use --bssid BSSID bssid of the target --ssid SSID the ssid of the WPA3 AP --freq FREQ frequency of the ap --start START_WORD word to start with in the wordlist
Information on installing and using the program, you will find here.





