Panther was created by StreamAlert's core architect, an cloud solution for automatic log analysis from Airbnb.
Panther is the next step for teams security who need a modern alternative to traditional SIEMs. They designed Panther for a massive scale, with a rich and intuitive user experience, in-program Python rule processing browsing and AWS support.
Its mission is to provide an open platform for the effective protection of businesses from threats and their security in cyberspace.
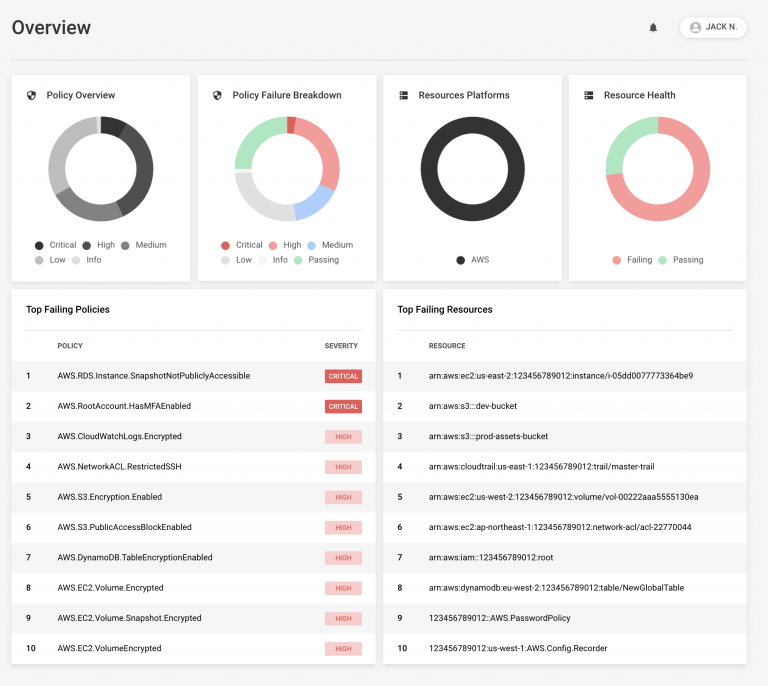
Panther is a powerful open source SIEM program code cloud-enabled, designed to be:
- Flexible: Detect and support notifications with base Python for PagerDuty, Slack, MS Teams and more
- With scalability: Built-in server-free technologies for scale and cost-effectiveness
- Fast: Real-time rule analysis, notification and automatic restoration
- Built-in: So analyze them archives security logging as well as cloud resources for ultimate visibility
- Automated: Quick and easy solutions with AWS CloudFormation
- Safe: Less privileges and encrypted infrastructure you control
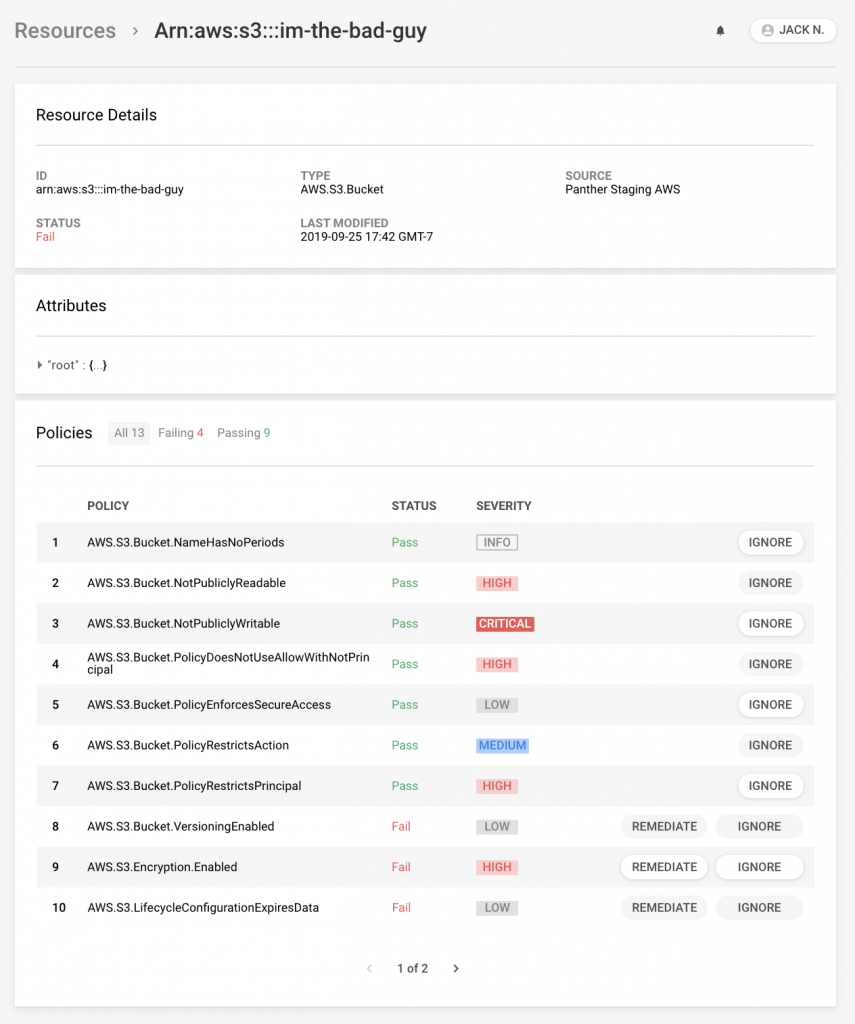
- Log analysis: Collection and analysis of log data with rules for threats and suspicious activity
- Incident response: SQL queries for long-term data, analytics, log correlation, and criminology.
- Cloud Information: Detect cloud infrastructure configuration and apply best practices.
- Automatic recovery: Automatic infrastructure correction where needed
Information on installing and using the program, you will find here.





