Ερευνητές ασφαλείας κυκλοφόρησαν exploits για την ευπάθεια των Windows Zerologon CVE-2020-1472 που επιτρέπουν σε έναν hacker να πάρει τον έλεγχο ενός domain of Windows.
As part of the Patch Tuesday, August 2020, security updates, Microsoft fixed a critical security vulnerability with a 10/10 rating known as “CVE-2020-1472 | Netlog Elevation of Privilege Vulnerability".

After successfully exploiting this vulnerability, attackers can elevate their privileges on a domain, and become administrators with full access.
The company Secura, which discovered this vulnerability, released a detailed description of the vulnerability, which it named Zerologon.
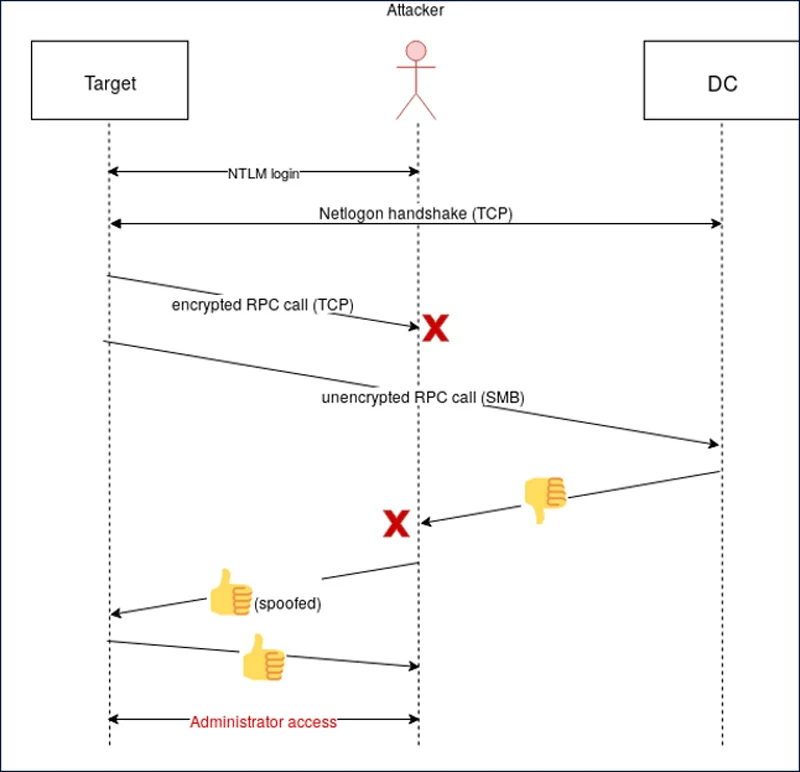
When a user connects a Windows device to a domain, they use the Netlogon Remote Protocol (MS-NRPC) via RPC to communicate with the controller and authenticate the user.
If a user logs in with the correct credentials, the domain controller tells the device to enable authentication with the appropriate permissions. Those who have the wrong credentials will obviously not be able to log in.
As authentication efforts are critical, Windows sends authentication requests over an encrypted, secure RPC connection
Secura researcher Tom Tervoort has discovered that it is possible to force domain controllers to return an unencrypted RPC communication when executing authentication requests.
After he returned no safe RPC communication, Tervoort could use a flaw in Netlogon's AES-CFB8 encryption negotiation algorithm to try to fake a successful connection.
In Tervoort tests, it took an average of 256 attempts to forge a successful connection.
This manipulation can deceive a device and connect the user to the system as a domain administrator.
Once a hacker gains administrator rights on the network, he gains full access to the domain controller. So it can change users' passwords and execute any command it wishes.
What makes this vulnerability so frightening is that an attacker does not even need credentials on the domain but can forge them to make any login attempt successful.
Rich Warren of the NCC Group and many others released various PoCs yesterday that allow you to gain domain administrator privileges in ten seconds.
0-Domain Admin in 10 seconds with Zerologon (CVE-2020-1472)
Using @_dirkjan 's NetrServerPasswordSet2 commit to impacket 😀🥳 pic.twitter.com/PELfKJCQLV
- Rich Warren (@buffaloverflow) September 14, 2020
Yeah, I can confirm that public insurance exploit for Zerologon (CVE-2020-1472) works. Anybody who has not installed the patch from August's Patch Tuesday already is going to be in much worse shape than they already were.https://t.co/SWK2hUDOYc https://t.co/0SDFfageQC pic.twitter.com/Lg8auMdtVU
- Will Dormann (@wdormann) September 14, 2020
As fixing a vulnerability in Zerologon could cause some devices to be authenticated incorrectly, Microsoft has begun repairing it in two steps.
The first phase was released on August 11 in the form of an update that prevents Windows Active Directory domain controllers from using unsecured RPC communication.
This update also records all authentication requests from devices that do not use secure RPC communication.
On February 9, 2021, as part of the Patch Tuesday updates, Microsoft will release a second update that will require all network devices to use secure RPCs unless expressly permitted by an administrator.
It is recommended that Windows administrators develop the first step in updating Active Directory domain controller to protect their network.
Secura has been released a tool which allows you to check if the domain controller you are using is vulnerable to Zerologon vulnerability (CVE-2020-1472).





