Technical details about a high-severity vulnerability in its Instagram app Facebook for Android and iOS show how a malicious user could exploit it to gain full control over the victim's account.

For this technique to work, the malicious user will need to send a specially crafted image to the target via a shared messaging platform or via email.
The issue was how to parse images from Instagram, as long as the app has access to it to display it as choice in a post. Then the vulnerability would start by allowing dangerous actions.
Technically, vulnerability is a buffer overflow (CVE-2020-1895) that happens when Instagram tries to upload a bigger image believing it is smaller.
Facebook fixed the problem in the spring, after the company disclosed Check Point and issued safety advice to deal with it.
In a detailed technical report today, Gal Elbaz of Check Point points out how custom third-party code implementation on Instagram could lead to serious, remote code execution risks.
The weak point, in this case, was a fixed hardcoded value that Instagram developers added when integrating Mozjpeg, an open source JPEG encoder that Mozilla modified libjpeg-turbo to better compression of JPEGs.
Check Point began testing Mozjpeg for potential flaws that could be meaningfully exploited. The purpose was to find out if Instagram could be affected by the library.
They found that the function that handles image sizes when analyzing JPEGs had an error that caused memory allocation problems during the decompression process.
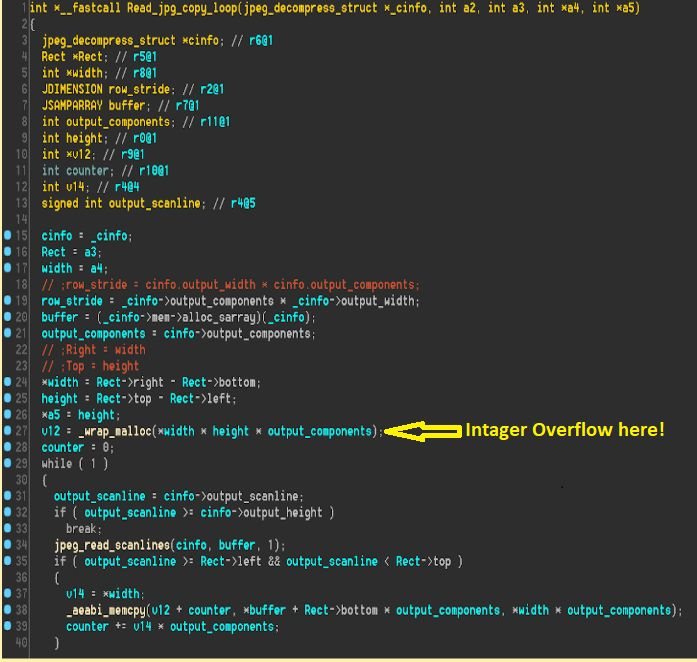
This could be used to damage memory, which can have dangerous consequences. At best, this type of error could throw Instagram, but if exploitable, it can lead to critical risks.
According to Check Point, Instagram has extensive permissions on the device, which include access to contacts, storage, device location, camera and microphone.
So in addition to checking the device owner's Instagram, a hacker could use the device as a spy tool without suspicion.





