You may have heard the term Zero Trust from your IT. Maybe not and you just felt it, when you suddenly realized that you can do almost nothing either on the Internet or on the Intranet. What exactly is Zero Trust?

The Zero Trust or in Greek Zero Trust Architecture, has recently become the buzzword of cyber security. This is a strategy that helps prevent successful data breaches by eliminating the concept of it confidences from an organization's network architecture.
Based on the principle «never trust, always verifyZero Trust is designed to protect modern digital environments by leveraging network segmentation, preventing lateral breach, providing Layer 7 threat prevention, and simplifying user access control.
For the record, the Zero Trust logic was created in 2010 by John Kaidevag, during his tenure as its vice president and principal analyst. Forrester Research. Then he realized that traditional security models operate on the antiquated assumption that everything inside an organization's internal network must be trusted.
According to this old model of trust, it is considered that one user's identity is not compromised and that all users act responsibly and IT can trust them.

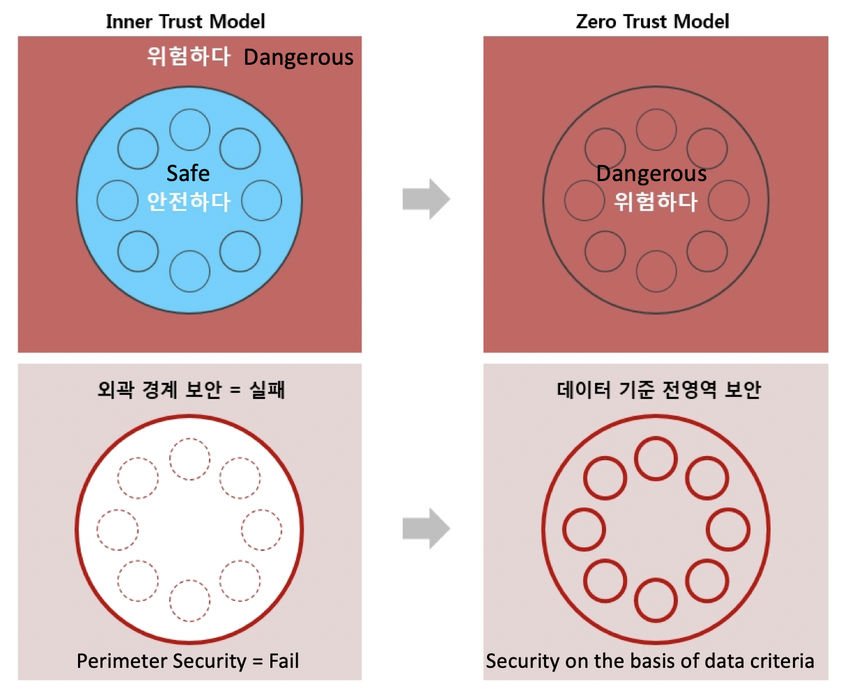
The traditional security of the computer network is based on the idea of the Castle-and-the-Trench. Castle and moat security is difficult to access when you are offline, but everyone on the net is trusted by default. The problem with this approach is that when an attacker finally gains access to the network, he has a free kingdom over everything inside.

The Zero Trust model recognizes that trust is a vulnerability. He believes that once connected to the network, users, including malware and any threats that may be present on their PC, are free to access, move and view any data. In short, there is no limit to what they see.
Η philosophy behind a Zero Trust network assumes that there are intruders both in and except of the network, so no user or machine should be automatically trusted.

So in the Zero Trust model there is always a "protect surface". It houses the most critical and valuable network data, assets, applications and services for the functions an organization. This surface is very small in relation to the total attack surface.
And then there are Microsegmentation. This technique creates security perimeters (small zones within the protective surface) to maintain separate access for separate parts of the network. The model is not to recognize the whole system as one, but to divide each factor as a micro-segmentation and to apply to each one a perimeter application, as a way of security.
For example, a network of files in a single data center that uses security perimeters may contain dozens of separate, secure zones. A person or program with access to one of these zones will not be able to access any of the other zones without a separate authorization.
That is, if you have a company that manufactures and sells clothespins, with Zero Trust your accountant will not have access to the warehouse files or even to the materials archiving program. Accordingly, the storekeeper will not view the accounting records or the accounting program. The sellers will only see the warehouse but they will not be able to change it and from the accounting they will only see the invoices that are cut to the customers. And so on…..
So if the protective surface "falls" or even if one or two micro-parts "fall" the damage will not be universal and above all it will be easily detectable.
A key safety net of zero confidence is Multi-Factor Authentication (MFA). Anyone who has access to something, a simple password will not be enough to enter the system. MFA simply means requiring more than one piece of evidence to authenticate a user. Entering a password is not enough to gain access.
In addition to user access controls, zero trust also requires strict device access controls. Zero Trust systems need to monitor how many different devices are trying to gain access to their network and ensure that each device is authorized. This further minimizes the attack area of the network.
In general, we would say that the principles of the Zero Trust are:
- Explicit verification of each user and material
- Implement the minimum possible access rights
- You assume that there is already an infringement
Once you have established a zero-confidence policy around your protective surface, you continue to monitor and maintain traffic in real time, looking for things, interdependencies, etc. that have not yet been considered, as well as ways to improve the policy.





