To stay safe on the Internet, one must learn to recognize malicious attachments commonly used in phishing emails to distribute malware.

When distributing malware, hackers create malicious campaigns that pretend to be invoices, invitations, payment information, shipping information, eFaxes, voicemails and more. These e-mails include malicious Word and Excel attachments or links to them, which, when opened and activated macros, install malware on a computer.
BazaarLoader
BazarLoader is a malware that targets companies and was developed by the same team behind the TrickBot trojan. During installation, hackers use BazarLoader / BazarBackdoor to remotely access your computer, which is then used to compromise the rest of your network.
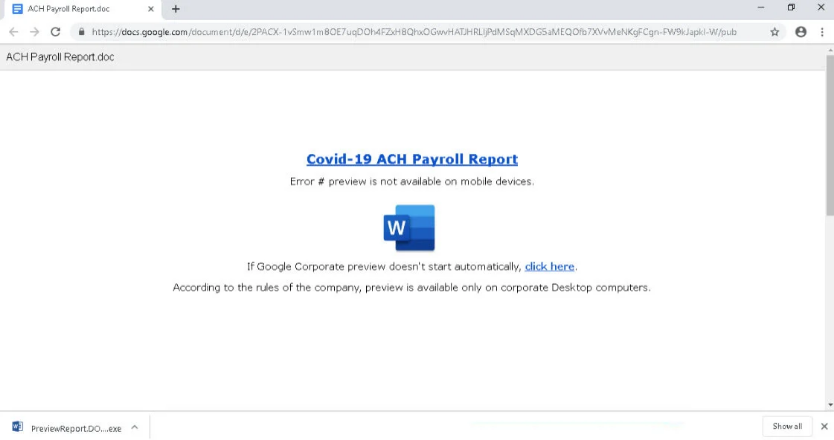
Dridex
Dridex is an advanced and modular banking Trojan that was first detected in 2014 and is constantly updated.
When it infects a machine, Dridex downloads different modules that can be used to steal passwords, provide remote access to a computer, or implementation other malicious activities.
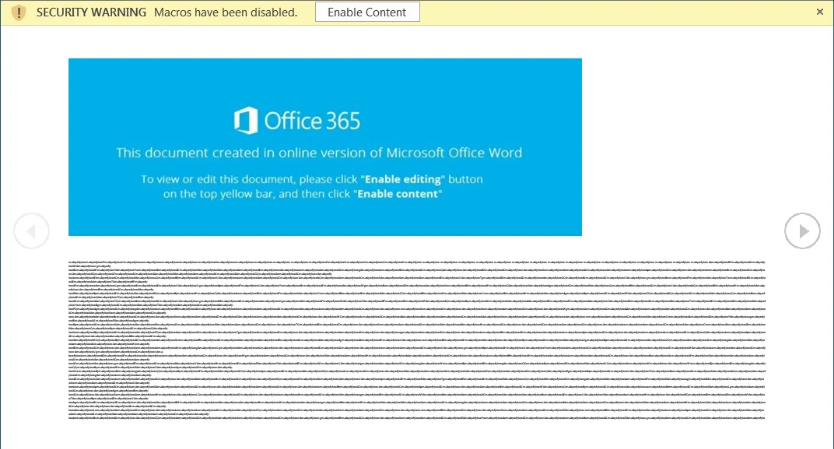
Emotet
The Emotet is the most widespread malware through spam messages emails containing malicious Word or Excel documents. Once it infects a machine, Emotet steals the victim's email and uses the infected computer to send spam to recipients worldwide.
The users infected with Emotet will eventually be further infected with trojans like the TrickBot and QakBot. Both Trojans are used to steal passwords, cookies, files, and gain access to an entire organization's network.
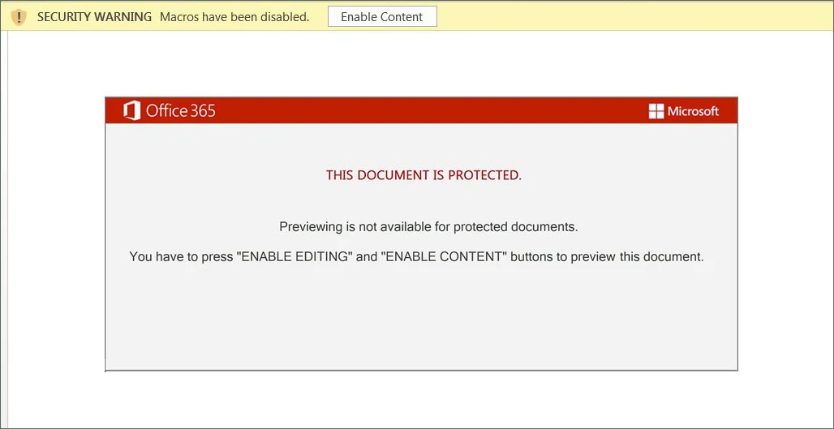
QakBot
QakBot, or QBot, is a banking trojan that spreads through phishing containing malicious documents. Microsoft Word, usually in business.
QakBot is a modular Trojan that includes the ability to steal banking information, install other malware, or provide remote access to an infected machine.
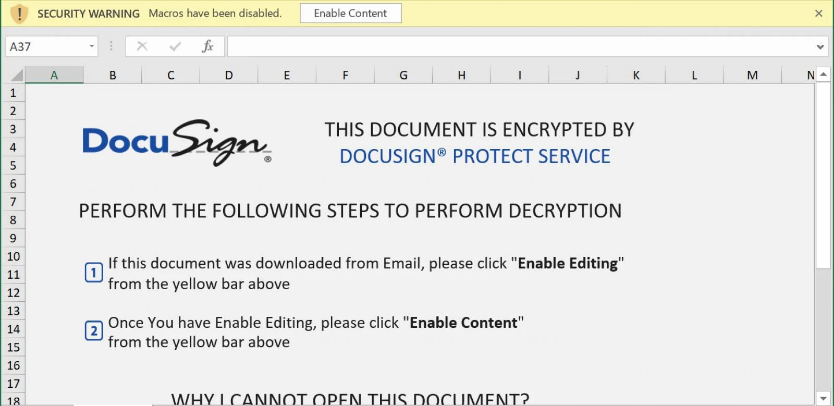
summarizing
Finally, you should never open attachments that end with extensions .vbs, .js, .exe, .ps1, .jar, .bat, .com or .scr, as they can be used to execute commands on a computer.
As most email services, such as Office and Gmail, block "executable" attachments, malware distributors send compressed files to password protect them. The password is included in the email.
Unfortunately, Microsoft has decided to hide file extensions by default, which allows malicious users to defraud their victims.
If you receive an email containing one of these file types, it is almost certainly malicious and should be deleted immediately!





