The Trickbot steals user credentials while, recently, launched attacks ransomware. The ESET Research contributed to the business with technical analysis.
ESET researchers have been involved in a global crackdown on Trickbot, the botnet that has infected more than a million computers since 2016. Along with Microsoft, the Black Lotus Labs Threat Research of Lumen, the NTT and others, the company intervenes in Trickbot by destroying the command and control servers.
ESET contributed to this operation by providing technical analysis, statistics and known names and IP addresses of command and control servers. 
Trickbot is known to steal users' credentials from compromised computers, and more recently, it has been observed as a mechanism for carrying out more serious attacks, such as ransomware attacks.
ESET Research has been tracking its activities since it was first detected, in late 2016. In 2020 alone, ESET's botnet monitoring platform analyzed more than 125.000 malicious samples and downloaded and decrypted more than 40.000 configuration files used by the various Trickbot modules, providing a complete picture of the different C&C servers used from this botnet.
"For years we've been watching it, the Trickbot breaches that have been recorded are systematic, making it one of the largest and longest-running botnets out there. Trickbot is one of the most popular families malware and is a threat to its users Internet worldwide, ”explains Jean-Ian Boutin, Head of Threat Research at ESET.
Throughout its life, this particular malware has spread in various ways. One of them is that Trickbot attacks systems that have already been compromised by Emotet, another well-known botnet. In the past, Trickbot malware has been exploited by its operators primarily as a banking trojan, stealing user credentials from online bank accounts and attempting to make illegal money transfers.
His scouts Trickbot internationally by its telemetry system ESET from October 2019 to October 2020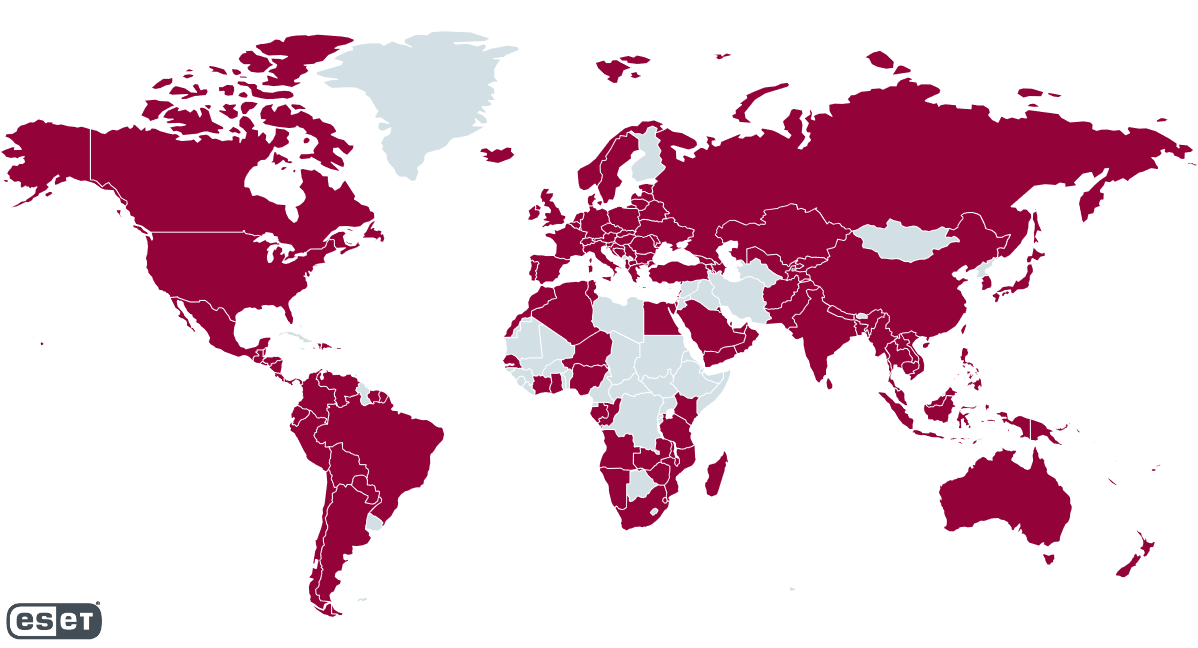
One of the earliest plugins developed for the platform allows Trickbot to use web injects, a technique that allows the malware to dynamically change what a user of an infected system sees when they visit specific website.
"Through monitoring, we collected tens of thousands of different configuration files, which allows us to know which websites the Trickbot operators were targeting. "The targeted URLs belong mainly to financial institutions," adds Boutin.
"Dealing with this threat is very difficult, as it has various alternative mechanisms and its connection with other cyber criminals in the background makes its overall operation extremely complex," Boutin concludes.
For more technical details about Trickbot, visit our WeLiveSecurity blogpost "ESET takes part in global operation to disrupt Trickbot".





