Sudomy is a tool for subdomains collection and analysis domain with automated recognition. This tool can also be used for OSINT activities.

Specifications
Active Method
Sudomy uses Gobuster tools due to its high speed in executing DNS Subdomain Bruteforce attack (wildcard support). The word list used comes from SecList Combined Lists (Discover / DNS) containing about 3 million entries
Passive Method
Looks for information through top third-party applications to show you the best results. The information pages are as follows:
https://dnsdumpster.com
https://web.archive.org
https://shodan.io
https://virustotal.com
https://crt.sh
https://www.binaryedge.io
https://securitytrails.com
https://sslmate.com/certspotter
https://censys.io
https://threatminer.org
http://dns.bufferover.run
https://hackertarget.com
https://www.entrust.com/ct-search/
https://www.threatcrowd.org
https://riddler.io
https://findsubdomains.com
https://rapiddns.io/
https://otx.alienvault.com/
https://index.commoncrawl.org/
https://urlscan.io/
Recon Worfklow
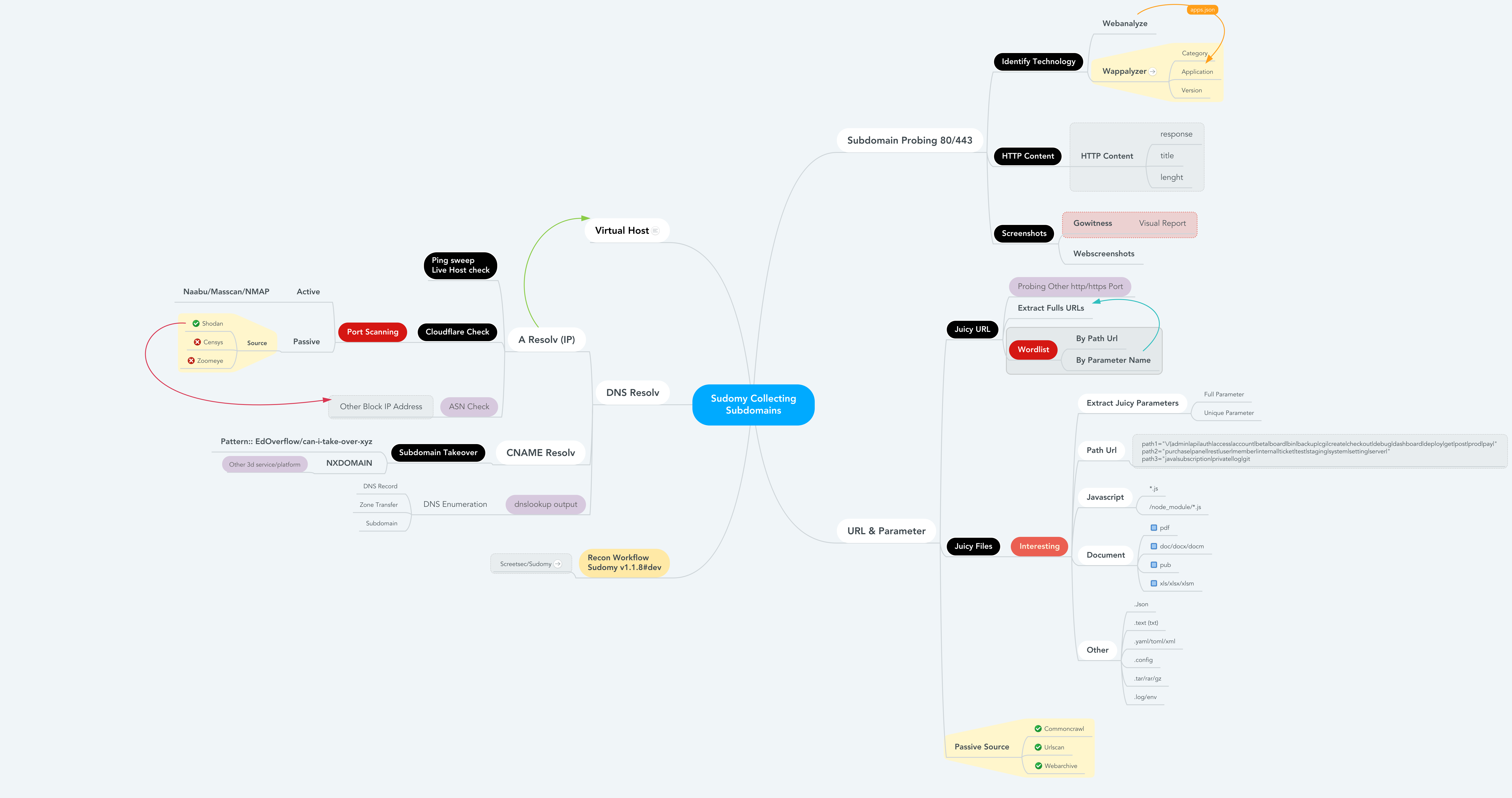
Information details
——————————————————————————————————
– subdomain.txt — Subdomain list – httprobe_subdomain.txt — Validate Subdomain – webanalyzes.txt — Identify technology scan – httpx_status_title.txt — title+statuscode+lenght – dnsprobe_subdomain.txt — Subdomain resolv – Subdomain_Resolver.txt — Subdomain resolv (alt) – cf-ipresolv.txt — Cloudflare scan – Live_hosts_pingsweep.txt — Live Host check – ip_resolver.txt — IP resolv list – ip_dbasn.txt — ASN Number Check – vHost_subdomain.txt — Virtual Host (Group by ip) – nmap_top_ports.txt — Active port scanning – ip_dbport.txt — Passive port scanning
——————————————————————————————————
- Passive_Collect_URL_Full.txt - Full All Url Crawl (WebArchive, CommonCrawl, UrlScanIO)
——————————————————————————————————
– ./screenshots/report-0.html — Screenshoting report – ./screenshots/gowitness.db — Database screenshot
User guides
- Offline User Guide: Sudomy - Subdomain Enumeration and Analysis User Guide v1.0
- Online User Guide: Subdomain Enumeration and Analysis User Guide - Up to date
Installation
$ pip install -r requirements.txt
git clone –recursive https://github.com/screetsec/Sudomy.git
Use
Sud⍥my - Fast Subdmain Enumeration and Analyzer
http://github.com/screetsec/sudomy
Usage: sud⍥my.sh [-h [–help]] [-s [–source]] [- d [–domain =]]
Example: sud⍥my.sh -d example.com
sud⍥my.sh -s Shodan, VirusTotal -d example.com
sud⍥my.sh -pS -rS -sC -nT -sS -d example.com
Optional Arguments:
-a, –all Running all Enumeration, no nmap & gobuster
-b, –bruteforce Bruteforce Subdomain Using Gobuster (wordlist: ALL Top SecList DNS)
-d, –domain domain of the website to scan
-h, –help show this help message
-o, –outfile specify an output file when completed
-s, –source Use source for Enumerate Subdomain
-aI, –apps-identifier Identify technologies on website (ex: -aI webanalyze)
-dP, –db-port Collecting port from 3rd Party default = shodan
-eP, –extract-params Collecting URL Parameters from Engine
-tO, –takeover Subdomain TakeOver Vulnerability Scanner
-wS, –websocket WebSocket Connection Check
-cF, –cloudfare Check an IP is Owned by Cloudflare
-pS, –ping-sweep Check live host using Ping Sweep method
-rS, –resolver Convert domain lists to resolved IP lists without duplicates
-sC, –status-code Get status codes, response from domain list
-nT, –nmap-top Port scanning with top-ports using nmap from domain list
-sS, –screenshot Screenshots a list of websites (default: gowitness)
-nP, –no-passive Do not perform passive subdomain enumeration
-gW, –gwordlist Generate wordlist based on collecting url resources (Passive)
–Httpx Perform httpx multiple probers using retryablehttp
–Dnsprobe Perform multiple dns queries (dnsprobe)
–No-probe Do not perform httprobe
–Html Make report output into HTML
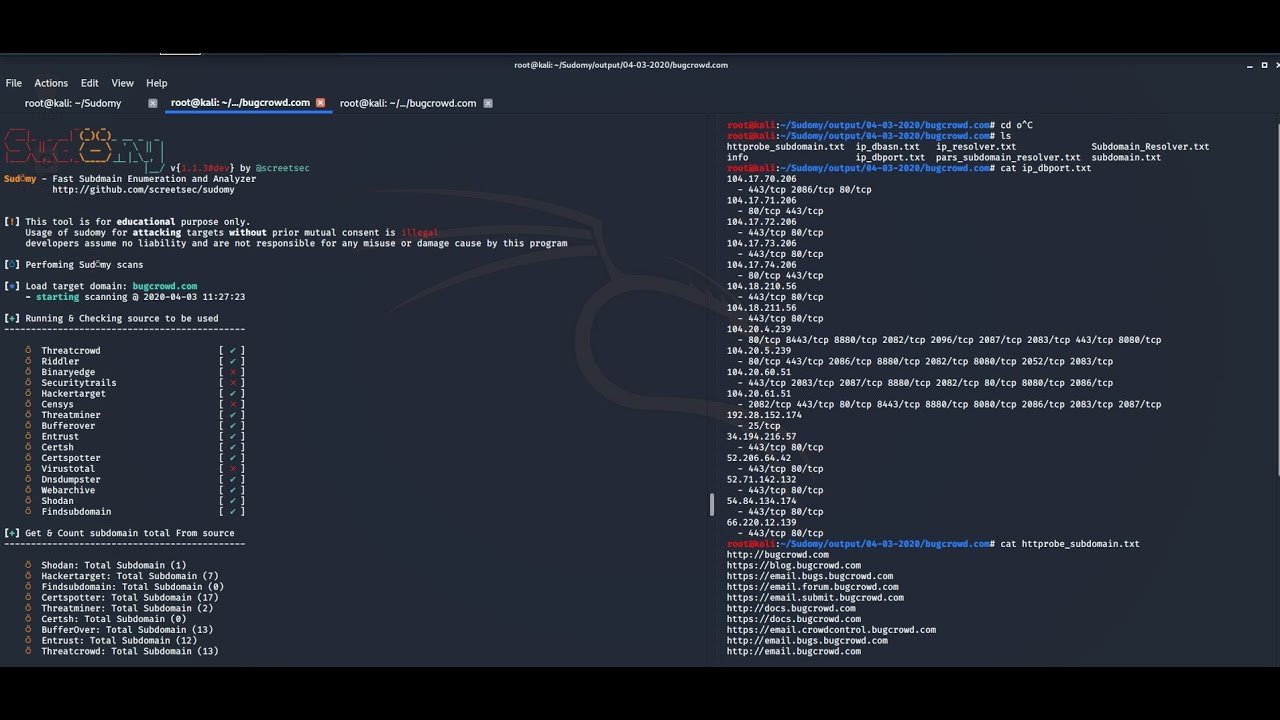
Application snapshots
Video guide
https://www.youtube.com/watch?v=vifjAlIfvx4
You can download the application from here.





