Russian hackers are using new malware to steal information from their victims. Named Jupyter, the threat maintains a low profile and has benefited from a rapid growth cycle.

While the purpose of Jupyter is to collect data from various software, malicious code that supports its delivery can also be used to create a backdoor on an infected system.
A variant of the malware appeared during an attack on an incident at a US university in October. However, forensic data show that older versions have been developed since May.
Researchers at cybersecurity firm Morphisec found that the developers of the attack kit were very active, with some items receiving more than nine updates in just one month.
The latest version was created in early November, but does not include significant changes. Constant modification of the code, however, allows it to avoid detection and allows Jupyter to collect more data from compromised systems.
Jupyter is based on .NET and focuses on stealing data from programs browsing ιστού Chromium, Mozilla Firefox και Google Chrome: cookies, credentials, certificates, autocomplete information.
The "thief" process begins with downloading an installer (Inno Setup executable) to a ZIP file that appears as legitimate software. According to Morphisec, some of them have not been fully detected on the VirusTotal scanning platform for the past six months.
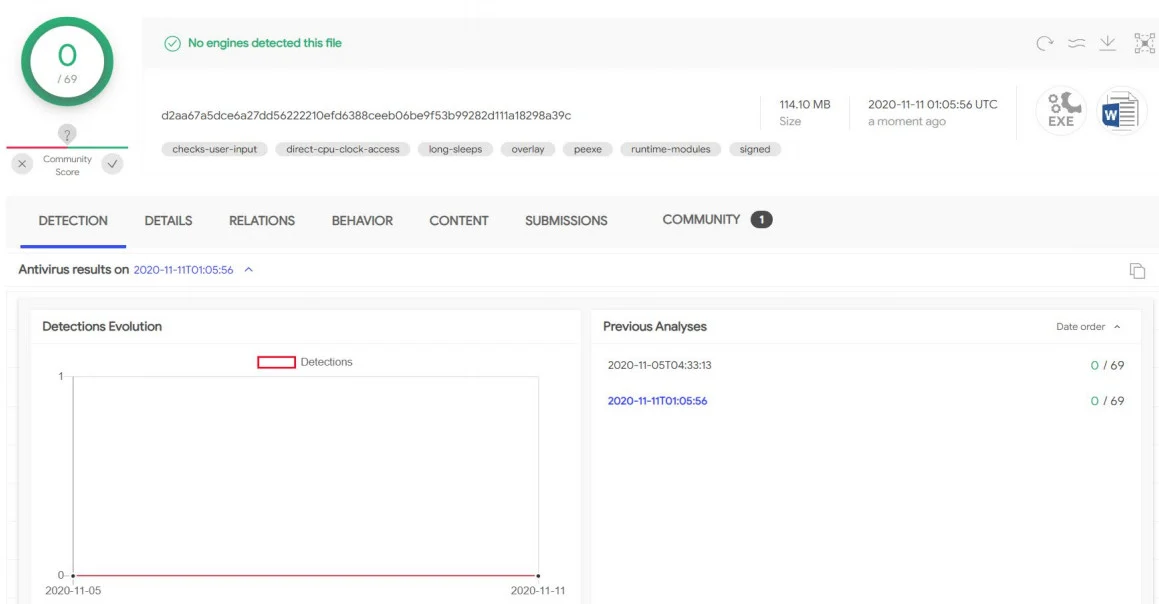
"Next, the client downloads the next step, a PowerShell command that runs the Jupyter .NET drive in memory," explains Morphisec.
In a newer version of the installer, the developers changed the process to a PowerShell command to run in memory.
Installers run legitimate tools such as Docx2Rtf and Magix Photo Manager to create a diversion, throwing in the background two PowerShell scripts, one encrypted and the other decoded.
The latest versions of the original installer are also based on the PoshC2 framework used in the penetration test to determine the persistence of the machine by creating an LNK shortcut file and placing it in the boot folder.
The Morphisec publication reports technical details about the tools and scripts used in a Jupyter attack, tracking the evolution of the elements and revealing their internal mode.
Russian links
Researchers say many of the C2 Jupyter servers were located in Russia. A large number of them are currently inactive.
The connection with Russian developers, however, seems to be valid, as Morphisec noticed a typo mentioning the name Jupyter, which was changed from Russian.
Further evidence to support this theory came after a reverse search image of Jupyter, which showed a result in a Russian forum.





