Microsoft is monitoring an ongoing e - fishing campaign on Office 365 which uses various methods to avoid automated analysis in attacks against corporate targets.

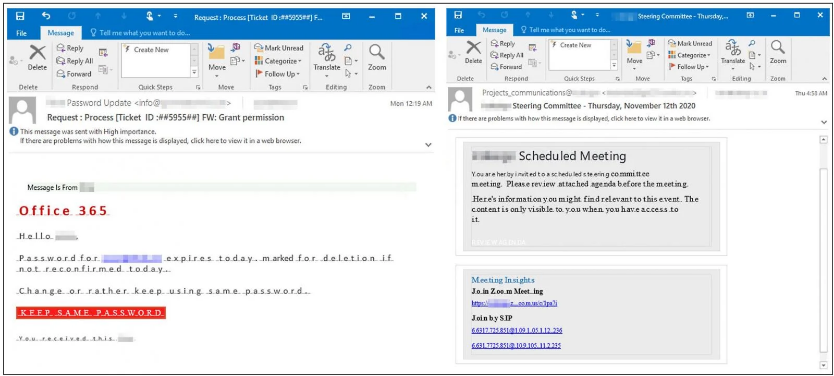
“The campaign uses enticing texts related to remote work, such as updates code access, conference information, helpdesk tickets, etc.”
Automatic redirection to valid domains
One of the avoidance tactics used in this credential theft attack is the use of redirect URLs with the ability to detect inbound links from sandbox environments commonly used by security investigators to obtain more information about the attack.
Once such a connection is found, the attacker changes it Mission of potential victims to a phishing landing page while redirecting any automated analysis attempts to legitimate websites.
This allows the "fishermen" to make sure that the phishing pages they have created will only be visited by real users, thus drastically reducing the chance of blocking their attacks and increasing the chances of having victims.
The phishing emails used in this campaign are also vague to ensure that security solutions will not be able to detect malicious emails and block them automatically before landing on target inbox.
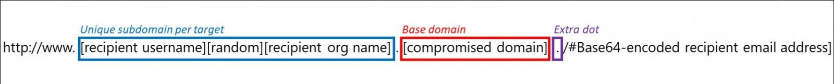
This campaign also creates custom subdomains for each of the targets as a way to make the phishing URLs more believable to the targets, thus increasing the success rate of the attacks.
These subdomains are created using a variety of formats, but will almost always contain the target username and domain name of their organization.
Display name patterns such as "Password Update", "Exchange Protection", "Helpdesk- #", "SharePoint" and "Projects_communications" are also used to make the malicious website look real.