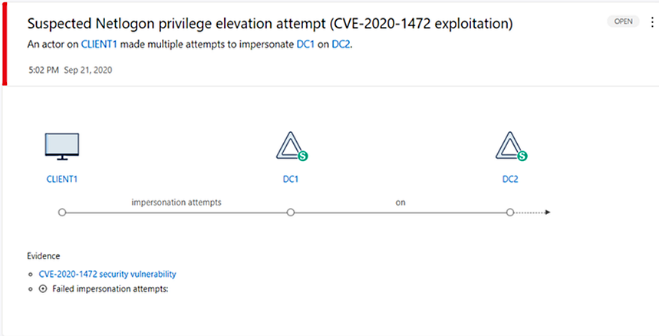
Microsoft has added Zerologon detection support to Microsoft Defender for Identity to enable Security Operations teams to detect attacks within the enterprise that attempt to abuse this critical vulnerabilitys.
Microsoft Defender for Identity (formerly known as Azure Advanced Threat Protection or Azure ATP) is a cloud-based security solution designed to leverage on-premises Active Directory signals to detect and analysis compromised identities, for advanced threats and malicious insider activity targeting a registered organization.
"Microsoft Defender for Identity can detect this vulnerability early on," said Microsoft Program Manager Daniel Naim. "It covers both aspects of exploiting and controlling the circulation of Netlogon."
Notifications that appear whenever exploit Zerologon or related activity is detected will allow SecOps teams to quickly receive information about the device or domain controller behind attack attempts.
Alerts will also provide information that can help identify targeted information if the attacks were successful.
“Finally, customers using Microsoft 365 Defender can take full advantage of the power of Microsoft Defender for Identity signals and alerts, combined with behavioral events and detections from Microsoft Defender for Endpoint Naim added.
“This coordinated protection enables you to not only monitor Netlogon exploit attempts over network protocols, but also see device process and activity files related to the exploit.”