WhiteScope security researchers have discovered over 8.600 security blanks in third-party pacemaker systems and routines used in their various subsystems.
These security gaps are of various kinds ranging from simple code errors to misconceived design choices that endanger the lives of patients.
The researchers they discovered these defects in seven different products from four different manufacturers. All research is presented in detail in one report released by the team this week.
The emphasis on their research was on implantable devices such as pacemakers, implantable cardiac-defibrillators (ICDs), pulse generators, and heart rate monitors (CRMs). We will collectively refer to this article as "pacemaker systems" and we should know that all these systems are remotely controlled by special devices (pacemaker programmer) and under the instructions of the physician monitoring the patient.
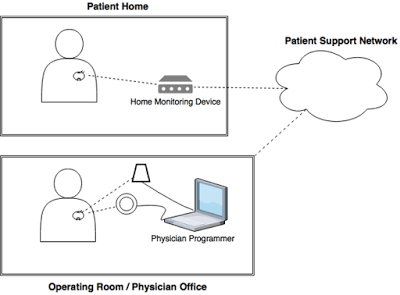
What the researchers found is that most of these pacemaker systems work on a similar architecture that includes the actual implanted medical device, a home monitoring device, a cloud-based infrastructure from which they are transmitted data to a physician and a pacemaker programmer, and that the physician uses this data for implant settings.
The denergy security audit of this entire infrastructure resulted in the discovery of over 8.600 vulnerabilities, most linked to an outdated library used for software owned by pacemaker developers.
In addition, there are also basic design issues that pacemakers have to deal with.
For example, pacemaker developers and the implanted pacemaker, although they must belong to the same manufacturer, do not validate each other, allowing a malicious a third programmer who can get close enough to the victim to be able to change the implant settings.
Likewise, pacemaker programmers do not need the control ID carddoctor's, meaning if a third party steals one of these devices they can use it to do harm.
Last but not least, the data of the pacemaker systems are stored in unencrypted file systems on removable media, meaning that anyone can get one of these systems and read secret medical information.
Naturally the team did not mention the names of the manufacturers. Nevertheless, the researchers said they had contacted ICS-CERT and transmitted their findings so that organizations could address security gaps, at least privately.
The fact that pacemakers and other implantable medical devices have blatant safety holes is already known. From 2013 there have been many warnings from both ICS-CERT as well as by FDA. The FDA also issued a guide on how to ensure medical devices.
Nevertheless, security researchers have still found vulnerabilities in these devices in the years that followed, including in addition to pacemakers and insulin pumps.





