AdbNet is an Exploitation-Framework which allows you to scan for vulnerable devices Android around the world and take advantage of them.

Specifications
-Post-Exploitation modules for its control and regulation deviceto which you are connected.
- Scanners to search for vulnerable Android devices around the world for exploitation.
- Options for managing the connected devices.
- Options to check if the devices you are connected to are connected or offline.
-IP-Search to retrieve information on a specific IP.
- Options to dump the IP addresses of vulnerable Android devices.
Installation
Obtain the required API keys
Create a free account on censys.io, then go to your account page and get the free api_id and api_secret key, open 'adbnet.py' and edit the api id and api key as shown in the image below:
![]()
Create a shodan.io account and go to your account to get the free api key, once you copy it, open 'adbnet.py' and edit the api key as shown in the image below:
![]()
sudo apt install pq
sudo apt install adb
pip3 install colorama
pip3 install requests
python3 adbnet.py or python adbnet.py or py adbnet.py
Use

First, run the "dump shodan" or "dump censy" command (dump shodan is recommended) to dump the IP addresses of vulnerable devices.
Then, after finding an IP address you want to test, run the "connect" command where you will be prompted to enter the destination IP address. Once you enter the destination IP address, you will be given the input command for the port you are trying to connect to. For the port, you can try entering "5555" or "4444", as these are the most common. If you want, you can try to find this port, but it may take a little longer.
AdbNet will now try to connect to the vulnerable Android device.
If it fails to connect, try another IP.
If you can connect to a device, you can check if you are actually connected using the "devices" command.
You can only connect to one device at a time! To kill sessions use the 'killall' command!
To open a shell and run commands on the vulnerable device, use the command “terminal".
Application Screenshots
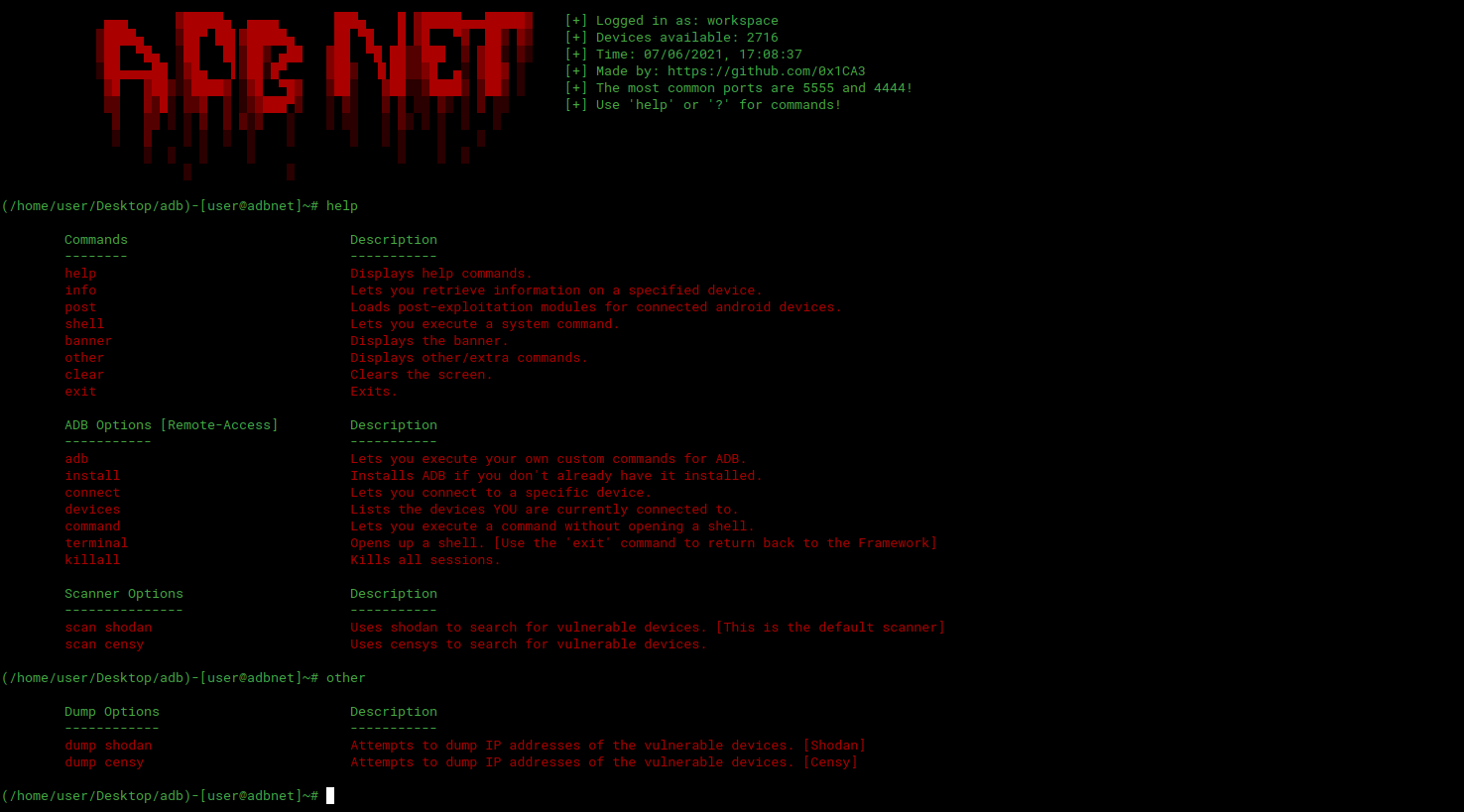
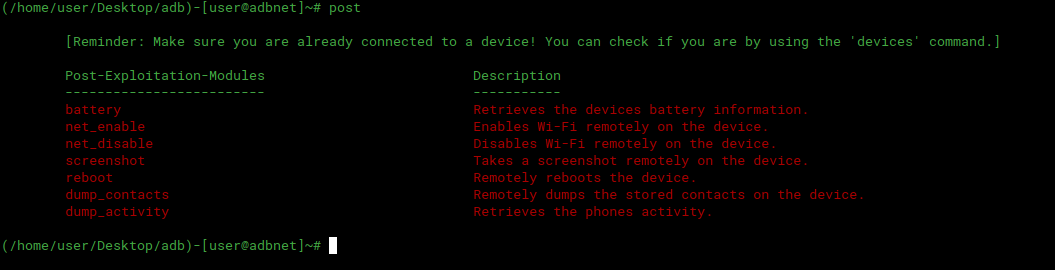
You can download the program from here.





