Shodan is one of the most popular and at the same time dangerous machines searchs, which provides you with information from network devices, such as routers/switches/traffic-lights/scada/cameras, etc.

There are many ways to find webcams through Shodan. Usually, using your webcam name is a good start. Remember, Shodan distributes the information on the camera banner, not the content.
Today we will show you how you can easily find vulnerable cameras with the help of Shodan and the Metasploit Framework. To start the Metasploit Framework on a Kali Linux machine, type “msfconsoleAt your terminal.
Enter “search shodan”To see all available modules / exploits related to the shodan search engine.
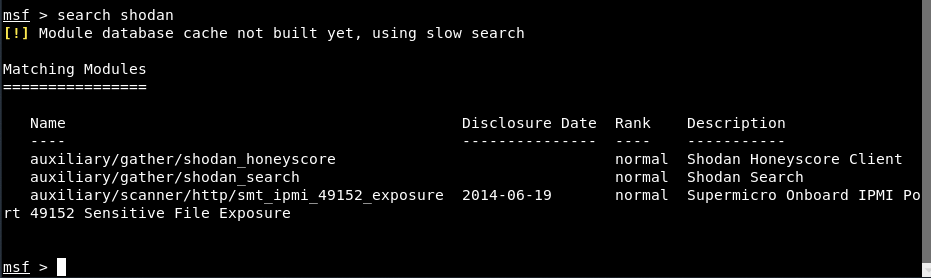
From all the above results, just type “use auxiliary / gather / shodan_search"
This module uses the Shodan API to search Shodan. Output from the module is displayed on the screen and can be stored in a archive or in the MSF database. Enter “Show options” for all the required options related to the above module.
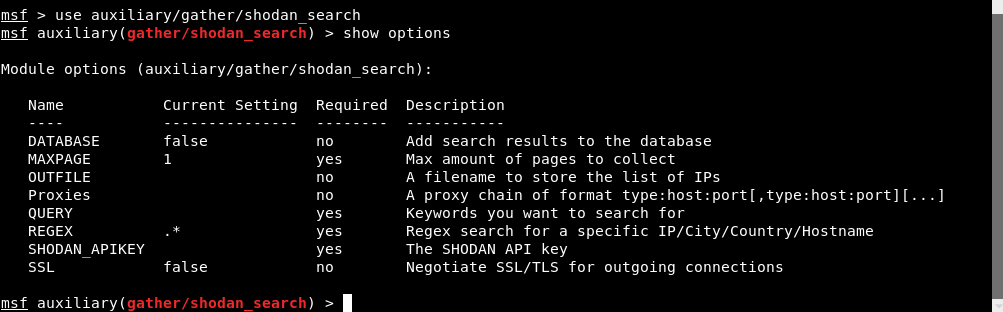
Now, go to the Shodan website for more information on API key .
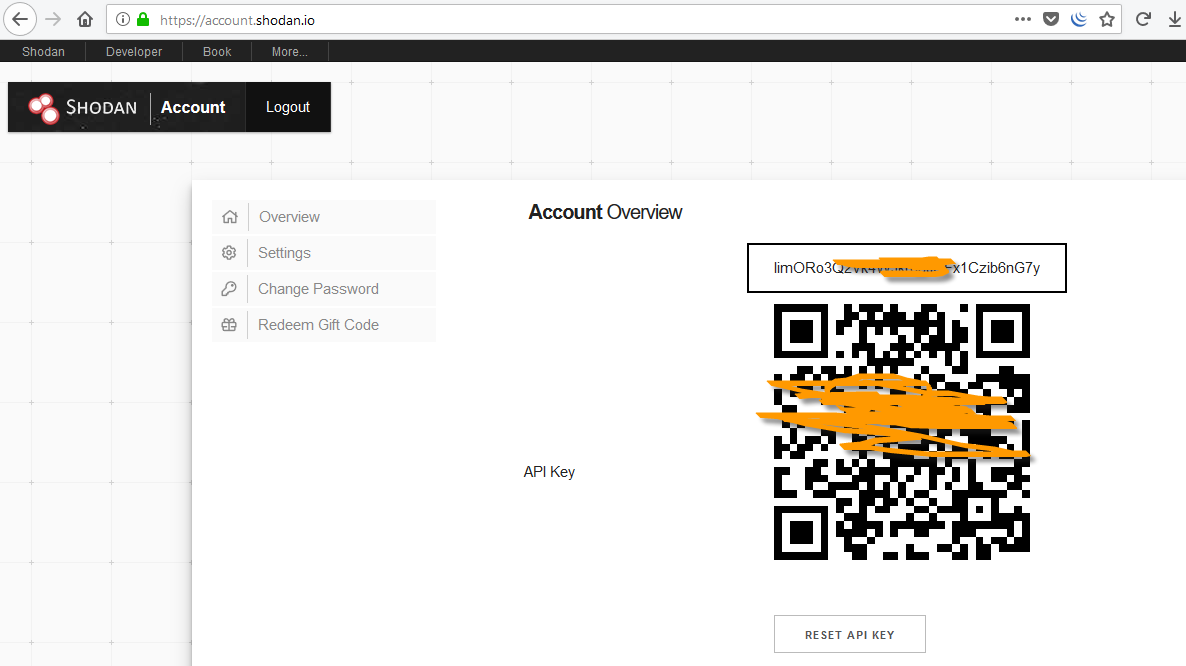
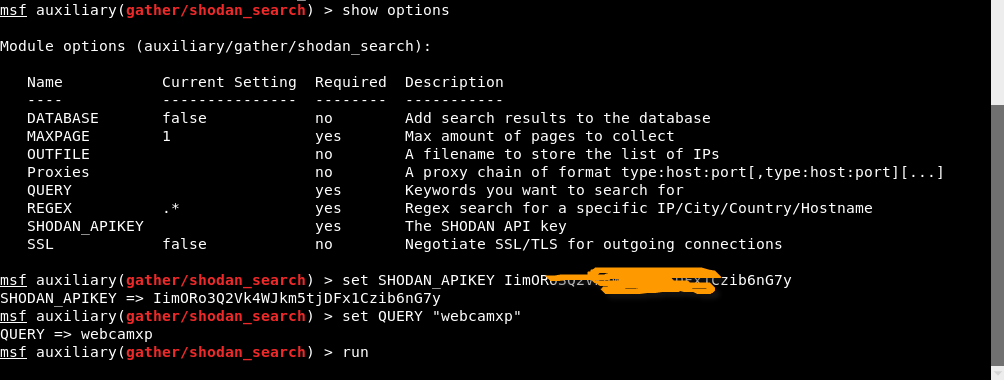
To set the Shodan key, enter “set SHODAN_APIKEY ”And you must also specify the query you want to search.
In our case, we will show the vulnerable Webcams, so type “set QUERY webcamxp”And then run the module by typing either run either exploit on the Metasploit console
Once you run the module, you will receive all the results shown by all the vulnerable open webcams hosted in different locations.
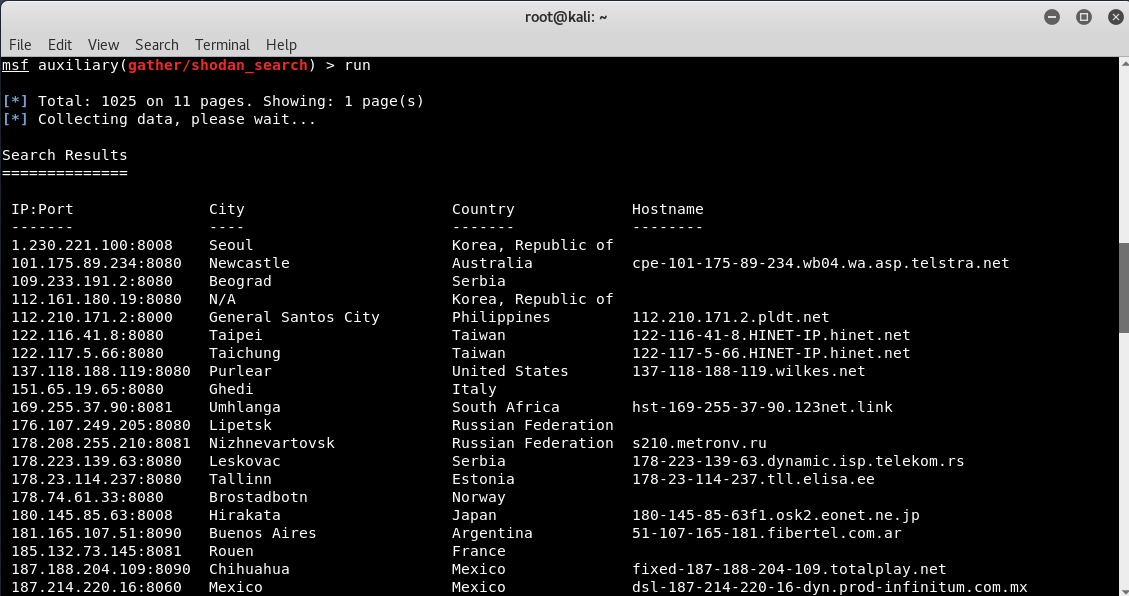
Some of these cameras are not protected, but most require authentication. The first step is to try the default username and password. We have created a short list of the default usernames and passwords of some of the most widely used webcams below.
- ACTi: admin / 123456 or Admin / 123456
- Axis (traditional): root / pass,
- Axis (new): requires a password created during the first login
- Cisco: No. default password, is created during the first login
- Grandstream: admin / admin
- IQinVision: root / system
- Mobotix: admin / meinsm
- Panasonic: admin / 12345
- Samsung Electronics: root / root or admin / 4321
- Samsung Techwin (old): admin / 1111111
- Samsung Techwin (new): admin / 4321
- Sony: admin / admin
- TRENDnet: admin / admin
- Toshiba: root / ikwd
- Vivotek: root/
- WebcamXP: admin/
We can not say for sure that the above credentials will work, but many careless and lazy administrators, as well as ordinary everyday users, leave the default settings and in these cases, the above usernames and passwords will give you access to private cameras around the world!
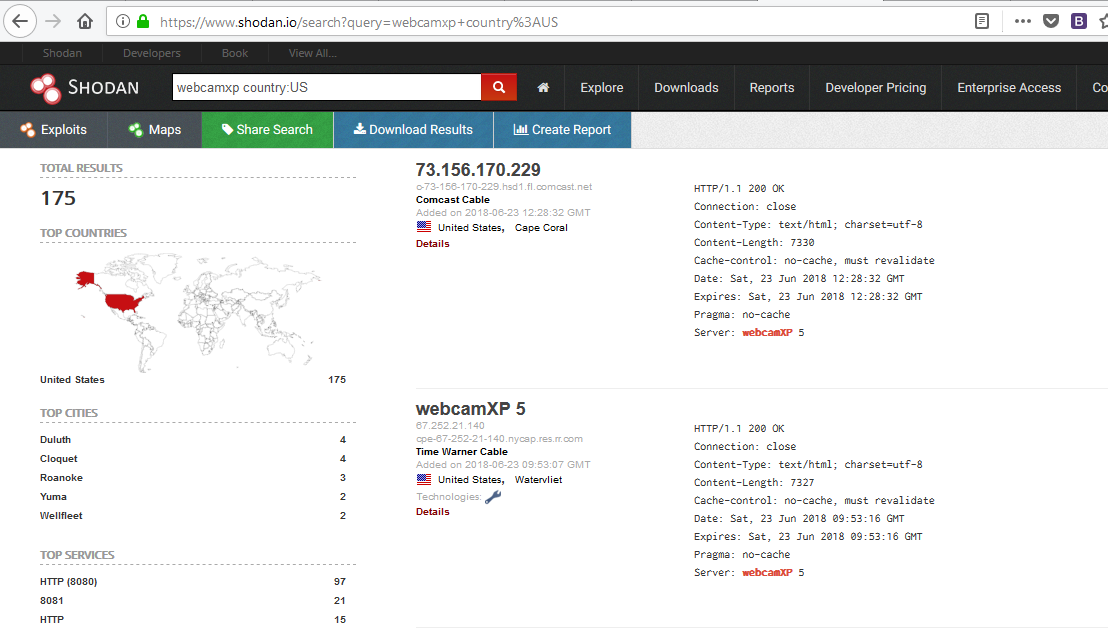
You can do the same through the web portal, for example, if you want to search the webcams only in the US, then the search query is “webcamxp country: US", Which will display all the results from the US, as shown below.
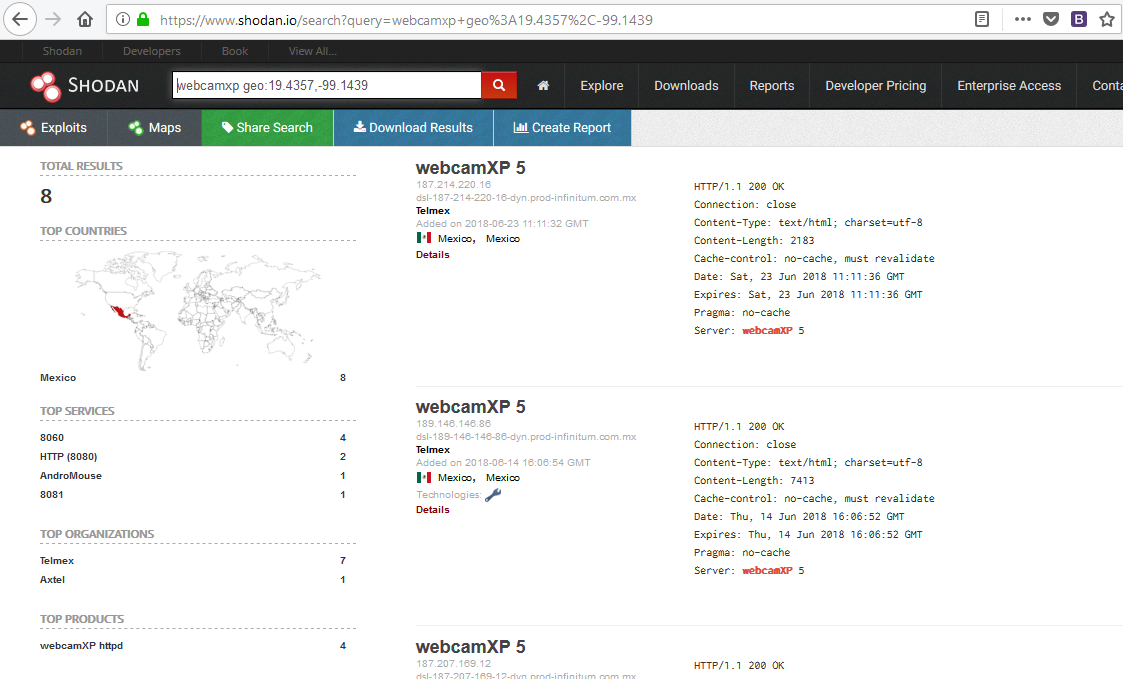
To be even more specific, we can limit our search to an individual city. Let's see what we can find in Mexico. We can find the following cameras by typing “webcamxp city: Mexico"
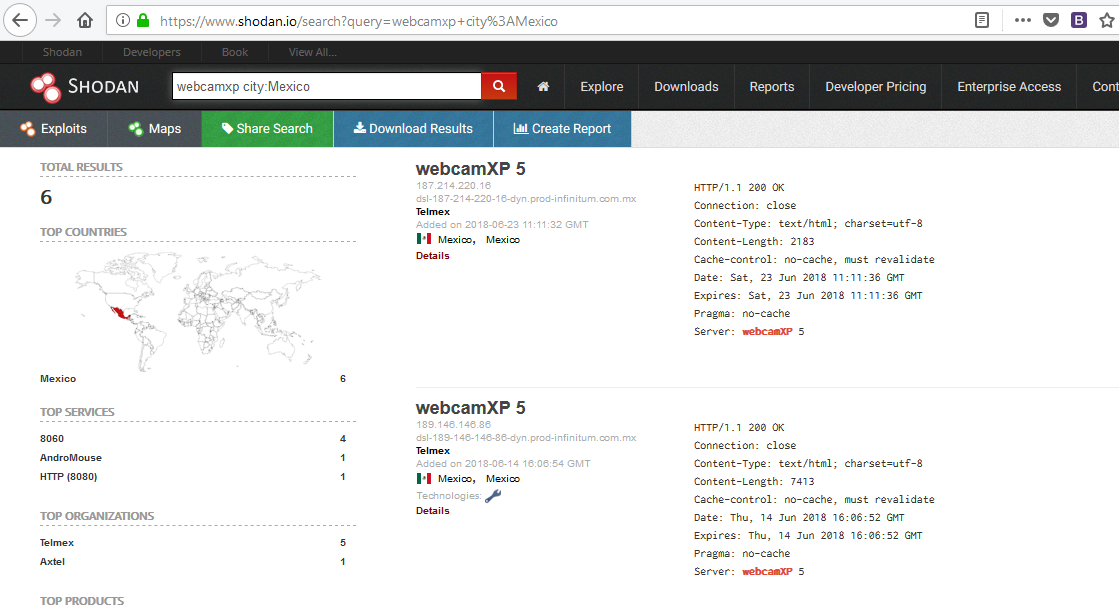
Shodan also allows us to be very specific in searching for web-enabled devices. In some cases, we can specify the length and width of the devices we want to find.
In this case, we will look for WebcamXP cameras in the length and width (19.4357, -99.1439) of Mexico City. When we search, we get a list of each WebXP camera in these coordinates in the world.