Bluescan is one project open source from Sourcell Xu teams DBAPP Security HatLab.
When violating new Bluetooth targets, the scanner can help us gather information, such as:
- BR devices
- LE devices
- LMP features
- GATT services
- SDP services
- Vulnerabilities
System requirements
This tool is based on BlueZ, the official Bluetooth stack of Linux. The following packages must be installed:
sudo apt install libglib2.0-dev libbluetooth-dev
Installation
sudo pip3 install bluescan
Use
Scanning BR devices -m br
Classic Bluetooth devices may use three technologies: BR (Basic Rate), EDR (Enhanced Data Rate) and AMP (Alternate MAC / PHY). Since they all belong to the Basic Rate system, we call them BR scanners:
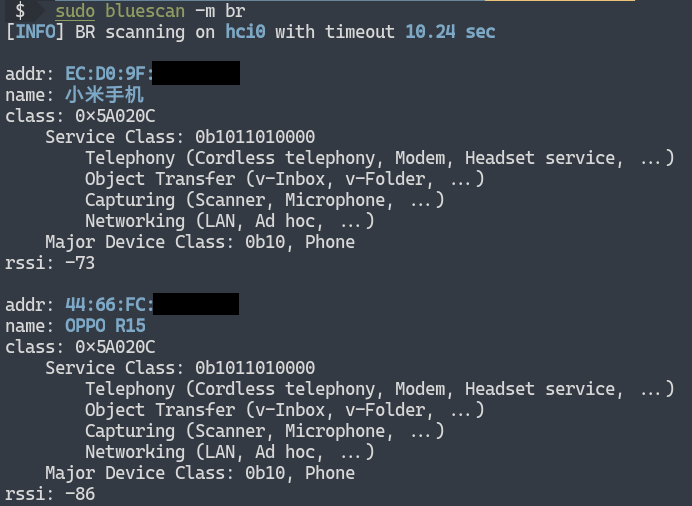
As shown above, by scanning BR devices, we can obtain the address, the name, device type and RSSI of the surrounding classic Bluetooth devices.
Scanning devices LE -m le
Bluetooth technology, in addition to the Basic Rate system, also has the low power system (LE). Scanning low power Bluetooth devices is called LE device scan:
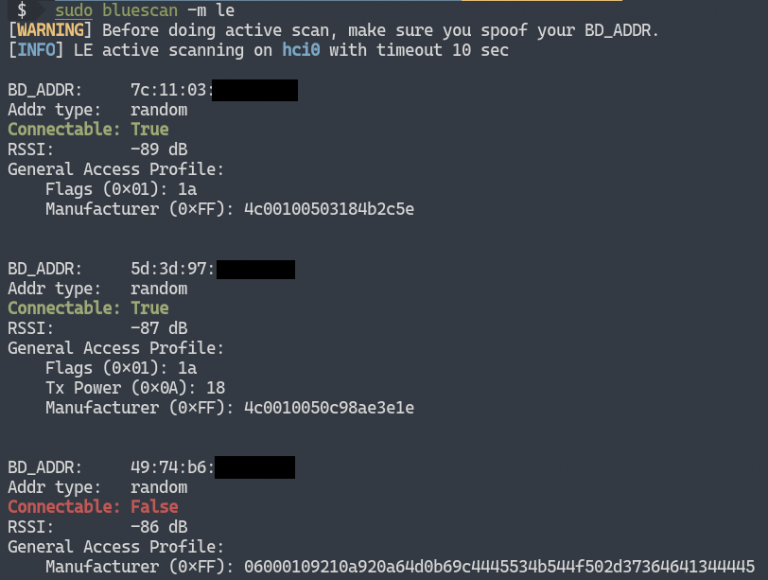
As shown above, by scanning LE devices, we can get the address, address type, connection status, RSSI and data GAP of surrounding LE devices.
SDP scanning services
Classic Bluetooth devices inform the outside world that they are open services them through the SDP. After the SDP scan, we can get the service data of the specific classic Bluetooth device:
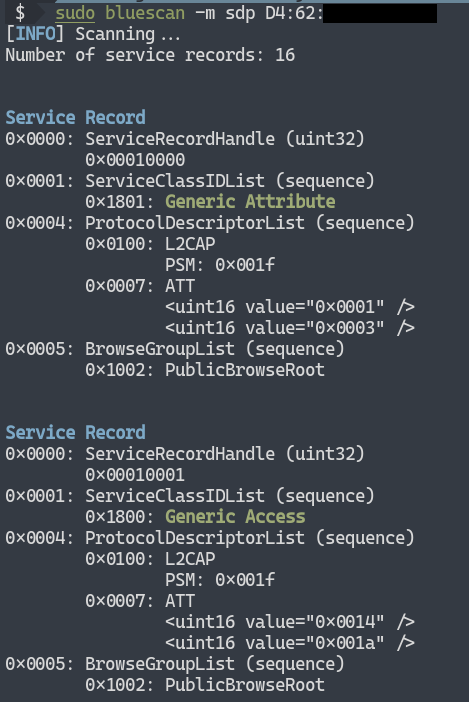
You can try to connect to these services for further benefits.
LMP scan functions
Detecting the LMP functions of classic Bluetooth devices allows us to judge the basic security features of the classic Bluetooth device:
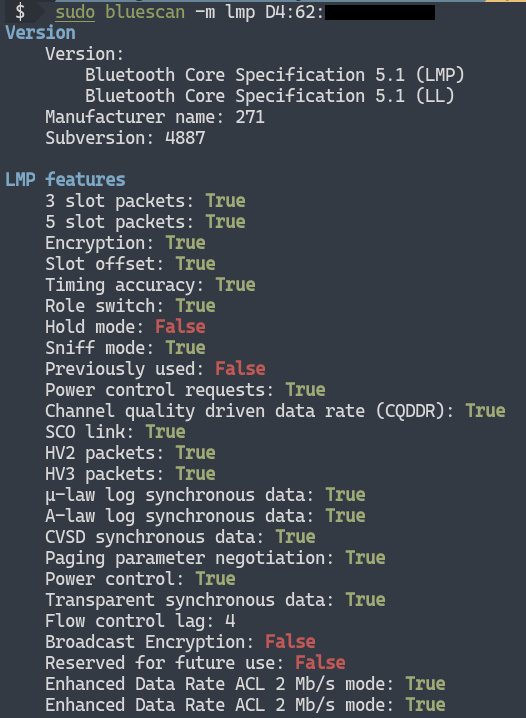
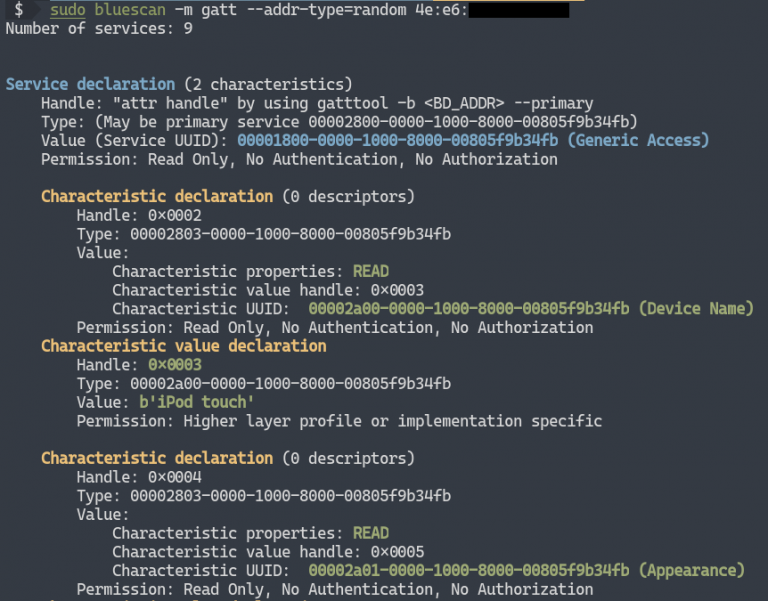
Scanning GATT services
LE devices inform the outside world about their open services through GATT. After scanning the GATT, we can receive the GATT service of the specified LE device. You can try to keep the GATT data for further breaches:
Vulnerability Scan (Demo)
The vulnerability scan is still in the demonstration phase and currently only supports CVE-2017-0785:
$ sudo bluescan -m vuln --addr-type = br ??: ??: ??: ??: ??: ?? ... ... CVE-2017-0785
You can download it program from here.





