Η Check Point Research (CPR) its research department Check Point Software spotted a variation botnet who has stolen nearly half a million dollars worth of cryptocurrencies through a technique called "crypto clipping".
The new variant, called Twizt, a descendant of Phorpiex, steals cryptocurrencies during transactions, automatically replacing the recipient's address with that of the perpetrator.
CPR warns cryptocurrency holders to be careful who they send money to, as 969 intercepted transactions have been recorded and the registrymeasurement goes on. Twizt can operate without active C&C servers, which allows it to bypass security mechanisms.
- In a period of 12 months, 3,64 were stolen Bitcoin, 55,87 Etherand $ 55.000 in ERC20 Tokens.
- 26 ETH were stolenin one case
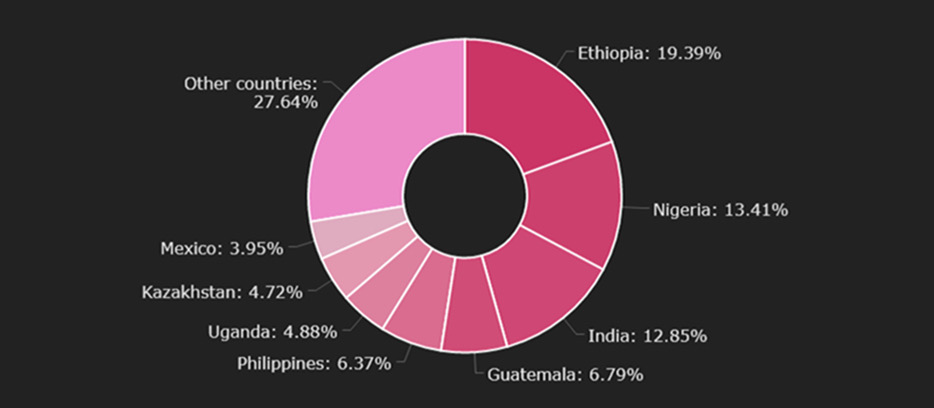
- The majority of the victims live in Ethiopia, Nigeria and India
Check Point Research (CPR) has identified a new variant of Phorpiex, a botnet known for sextortion and crypto-jacking. The new variant, called Twizt, operates without active command and control servers, meaning that any computer it infects can expand the botnet. CPR estimates that Twizt has stolen nearly half a million dollars worth of cryptocurrency. Twizt's new features have led CPR to believe that the botnet may become even more stable and, therefore, more dangerous.
How Twizt works
The Twizt utilizes a technique called “cryptoclipping", Which is the theft of cryptocurrencies during transactions through the use of malware that automatically replaces the wallet address intended with the perpetrator's wallet address. This results in the amounts going into the wrong hands.
The Victims
Over a period of one year, from November 2020 to November 2021, the Phorpiexbotsstole 969 trades, stealing 3,64 Bitcoin, 55,87 Etherand $ 55.000 in ERC20 Tokens. The value of the stolen goods at current prices is almost half a million US dollars. Several times the Phorpiexmanaged to steal large amounts of transactions. The largest was 26 ETHamount for a transaction Ethereum.
Graph 1. Victims by spaceα
Commentary: Alexander Chailytko, Cyber Security Research & Innovation Manager at Check Point Software:
"There are three main dangers of its new variant Phorpiex. First, the Twizt uses the model peer-to-peer and is able to receive commands and updates from thousands of other infected machines. One botnet peer-to-peer it is more difficult to destroy and shut down. That makes it Twizt more stable than previous versions of muzzle of Phorpiex.
Secondly, like the old versions Phorpiex, the Twizt is able to steal cryptocurrencies without any communication with C&C, therefore, it is easier to bypass security mechanisms such as firewalls, in order to do damage. Third, the Twiztsupports more than 30 different cryptocurrency wallets from different block chains, including the most important, such as Bitcoin, Ethereum, Dash, Monero.
This creates a huge range of attack, and virtually anyone using encryption could be affected. "I urge all cryptocurrency users to double-check the wallet addresses they copy and paste, as they could easily accidentally send their cryptocurrencies to the wrong hands."
Security tips
- Check the wallet address. When users copy and paste an address of one cryptowallet, must always double check that the original and the pasted address are the same.
- Try the transactions. Before sending large amounts of cryptocurrency, one needs to be done first test transaction with a minimum amount.
- Stay informed. The operating system must be up to date and not download software from unverified sources.
- Skip them advertisements. When searching for wallets or cryptocurrency trading platforms, they should always choose the first site in the search and not the ads. These can be misleading as well CPR has found many prices on google, which aim to extract money.
- Observe the addresses URL. They should always double check the addresses URL!





