Brute Shark is one network analysis tool (NFAT) for collecting, parsing, processing, and collecting network packets (mainly PCAP files). Includes: export passwords, create network mapping, reconstruct TCP sessions, extract hashed passwords, and even convert them to Hashcat format in order to perform an offline Brute Force attack.
The main goal of the program is to provide a reliable solution to penetration testers and network administrators in order to control network traffic while trying to identify weaknesses that can be used by a potential attacker to gain access to critical points in the network.
Two Brute Shark versions are available, one based on the GUI (Windows) and one with a command line interface (Windows and Linux).
The various functions of the program can also be used independently as an infrastructure for analyzing network traffic on Linux or Windows computers.
The project was developed in my spare time to address two of my main passions: software architecture and analysis data network.
Operation of the program
- Export and encode user credentials
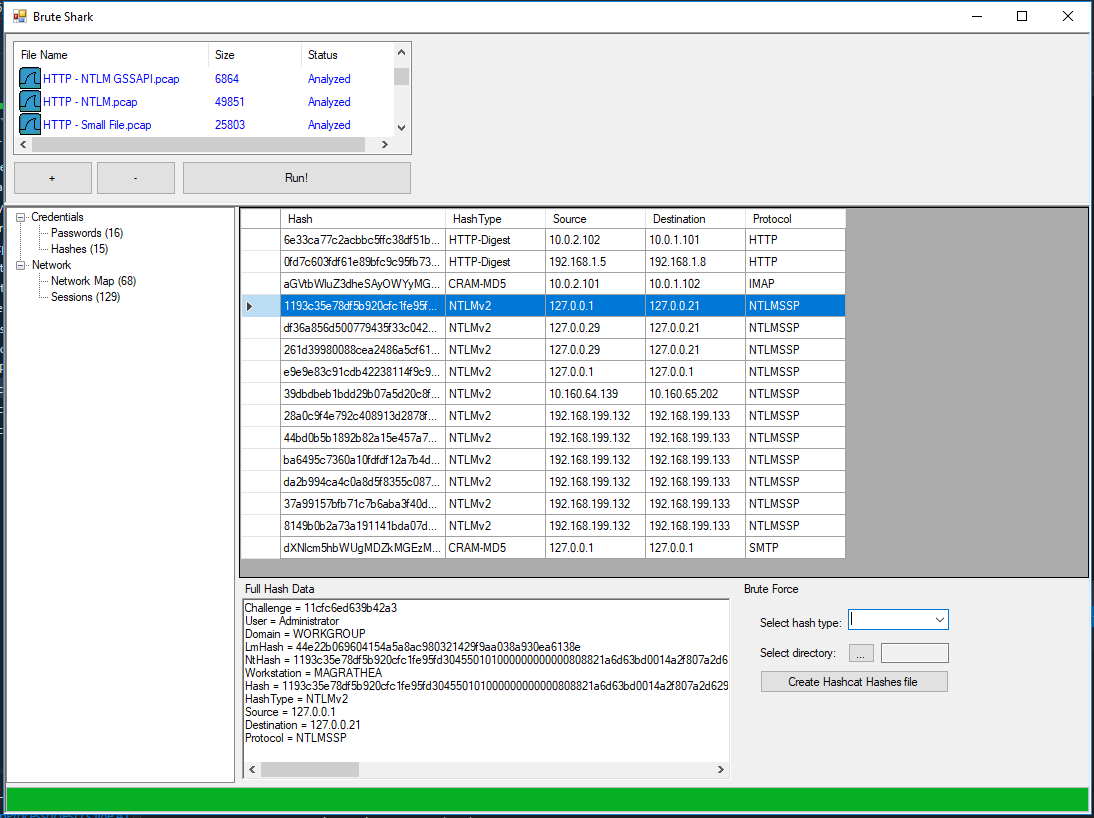
- Extract hashes and break through hashcat
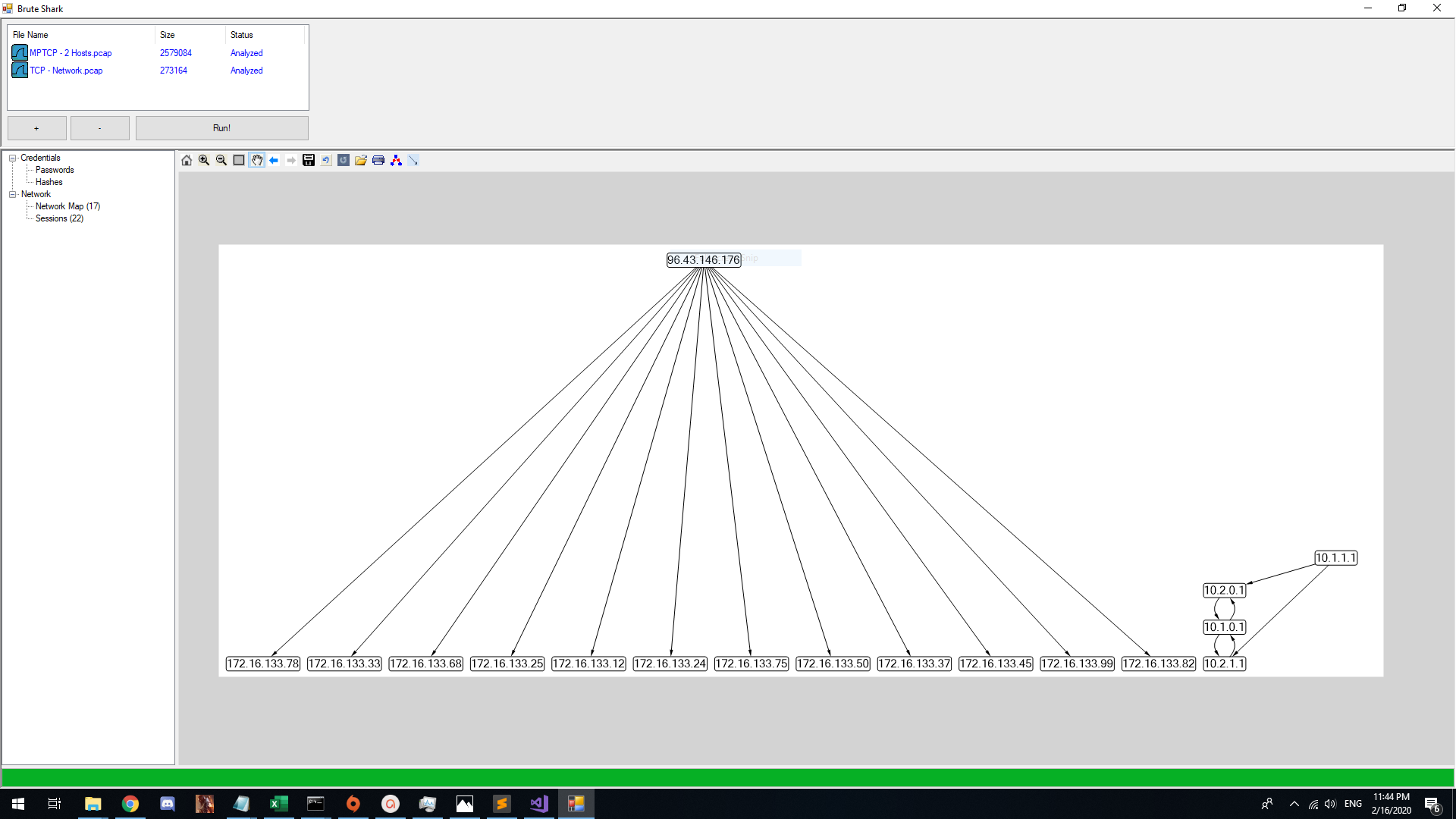
- Create a network diagram
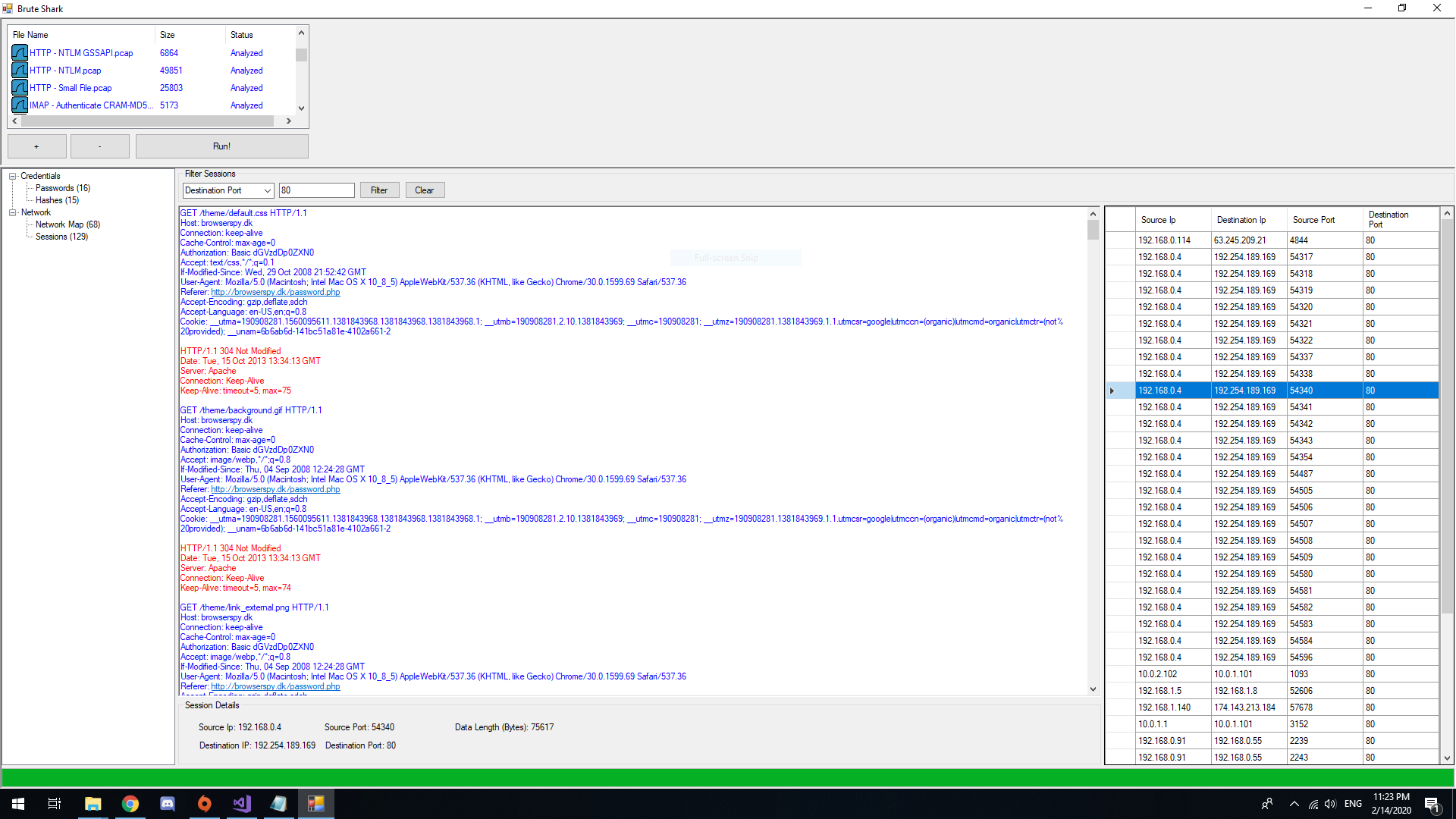
- TCP connection reconstructions
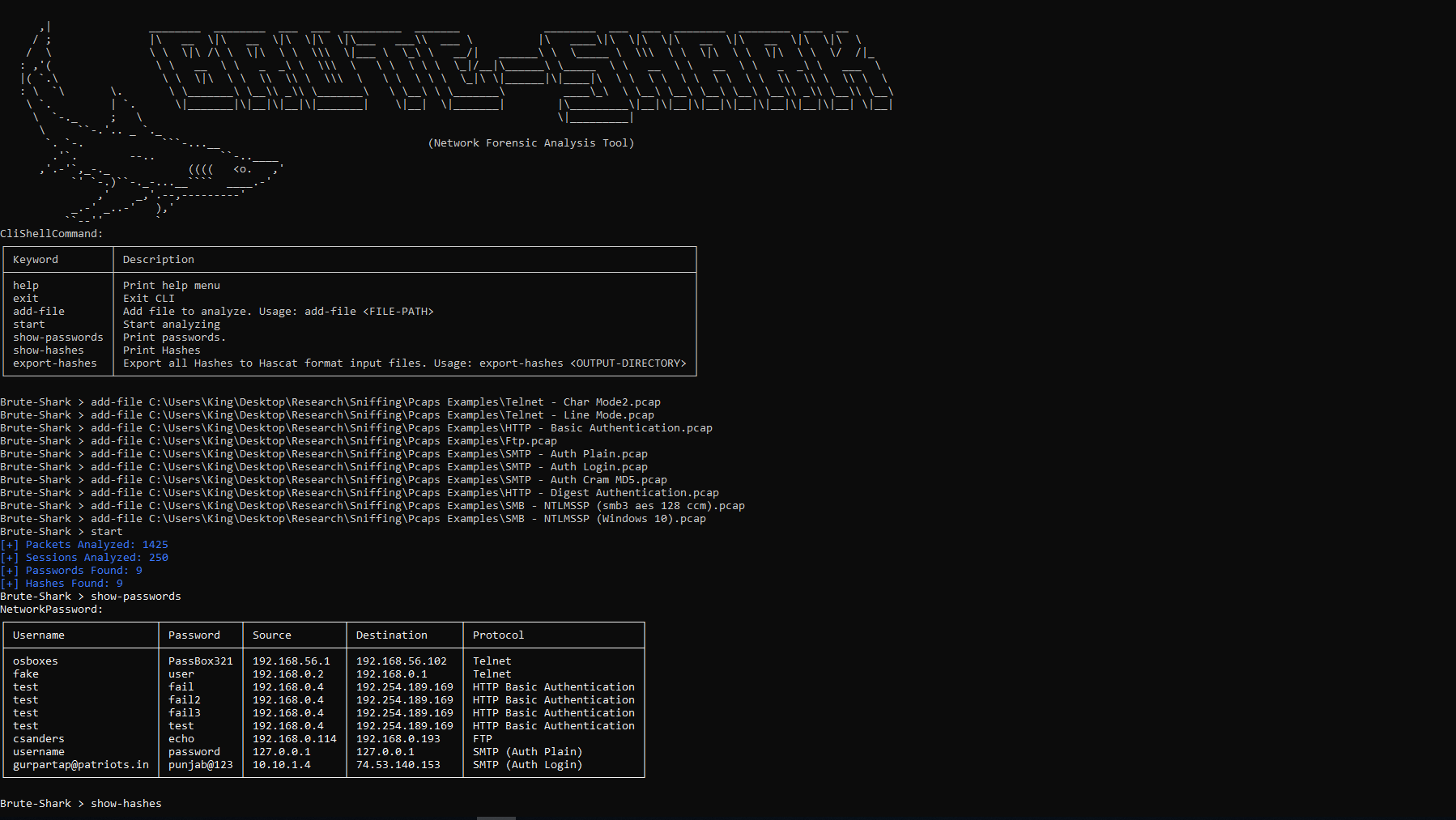
Password Extracting (HTTP, TELNET, IMAP, FTP, SMTP)
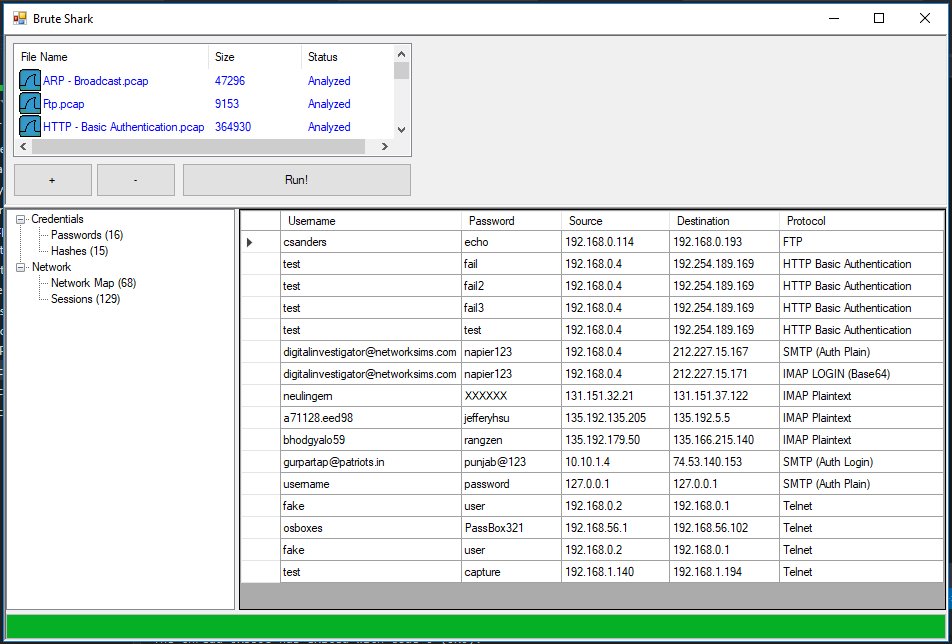
Hashes Extracting (HTTP-Digest, NTLM, CRAM-MD5)
Building a Network Diagram
Reconstruct all TCP Sessions
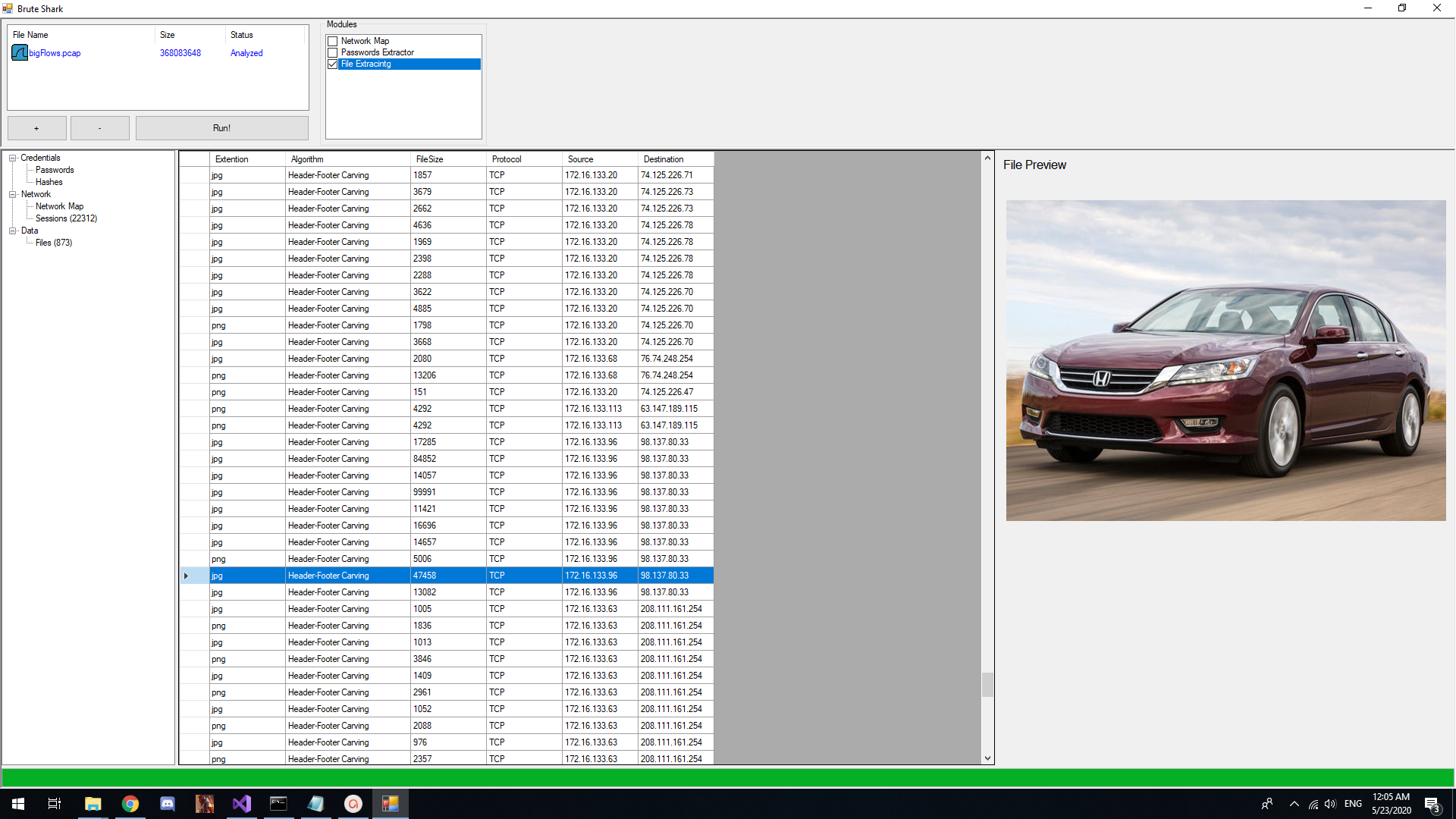
File Carving
Brute Shark CLI

Download
- Windows - download the file from here Windows Installer (64 Bit).
- Linux - download the file from here BruteSharkCli.zip and run BruteSharkCli.exe using MONO:
wget https://github.com/odedshimon/BruteShark/releases/latest/download/BruteSharkCli.zip unzip BruteSharkCli.zip mono BruteSharkCli / BruteSharkCli.exe





