As the summer holiday season approaches, cybersecurity provider Check Point Software Technologies Ltd. is warning the public to remain vigilant due to increased cyber risks targeting both individuals and organizations.

Despite airport delays, rising costs and continued uncertainty surrounding COVID-19, international travel this summer is expected to grow 11% from pre-pandemic levels.
Στη βιασύνη τους να προλάβουν τις διακοπές τους, για ορισμένους είναι οι πρώτες μετά από τρία χρόνια, οι ταξιδιώτες είναι πιθανό να μην δώσουν την πρέπουσα προσοχή όσον αφορά την ασφάλεια στον κυβερνοχώρο και να βρεθούν αντιμέτωποι με κινδύνους που αφορούν στη διαδικτυακή τους δραστηριότητα. Οι εγκληματίες του κυβερνοχώρου γνωρίζουν καλά αυτή την vulnerability and if anything, they step up their efforts during the summer season.
According to the report Threat Intelligence Report by Check Point Research (CPR), the global average number of weekly attacks on travel and leisure organizations increased by 60% in June 2022 compared to the first half of June 2021.
Between May and August 2021 attacks on these sectors increased by 73% and this year is likely to see a similar surge, with one of the key trends involving hackers impersonating established brands in phishing attacks as holidaymakers look for last-minute holidays and travel, hotel and attraction offers with delayed availability.

Figure 1 Phishing email impersonating Delta Airlines
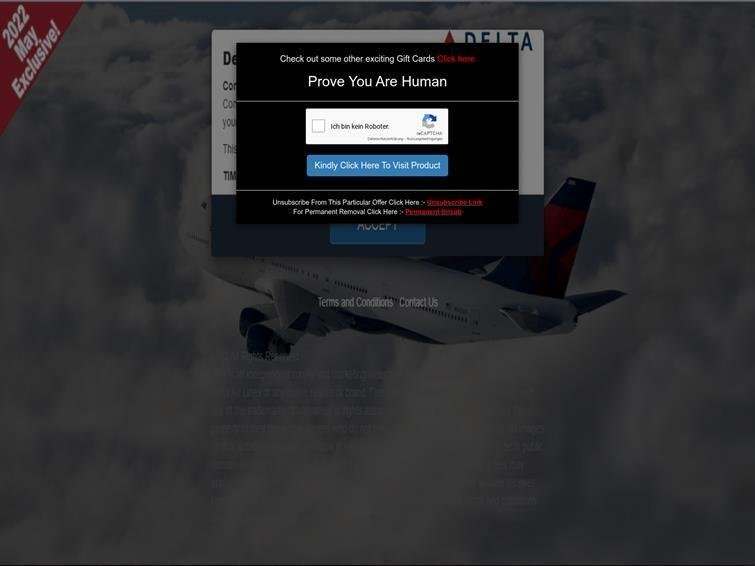
Figure 2 Deceptive Delta Airlines page
A potential vacationer who clicks on a phishing email or provides their login information over an unsecured public Wi-Fi connection could face personal risk in terms of credential theft, as well as lead to financial losses. However, there is also an even more serious risk to their employers.
The trend toward so-called hybrid vacations, where people work remotely for part of the summer vacation, makes this threat even more real. Personal laptops, tablets or mobiles often provide criminals with easy access to corporate networks, especially if BYOD devices are not adequately secured.
Meanwhile, corporate networks themselves are most vulnerable this time of year or even on weekends and holidays throughout the year. With security operations teams working understaffed, cyber attacks can go unnoticed until it's too late and the damage has been done. A typical example was the attack ransomware on Kaseya's network on July 4 last year by the Russian-speaking criminal gang REvil, which affected more than 1000 organizations worldwide, in addition to about 15 similar attacks per week during May and June, according to CPR.
For many of us, this may be our first time traveling abroad since the pandemic, and as such there may be some elements of our travel routine that we may have forgotten, including cyber security habits. This is highly desirable for opportunistic hackers looking to take advantage of lax behavior and unprotected devices. It is also a risk at an individual level in our hyper-connected world, as well as for any organization with which a person communicates, including their employer, said Michalis Bozos, Sales Manager Greece & Cyprus, Check Point Software.
By planning ahead, individuals can look forward to their vacation knowing they have taken simple but necessary precautions to secure their devices while protecting their employers' networks. That's why Check Point has put together ten top tips to help consumers stay safe during the summer months.
Top tips to keep your devices secure
1. Treat public Wi-Fi hotspots with caution. Free Wi-Fi access is attractive, but it can also pose some serious security threats. It's not uncommon for hackers to sit in airports, waiting for travelers to join public Wi-Fi networks so they can take advantage of unsuspecting travelers. Avoid unsecured Wi-Fi networks altogether if possible, but if you must use them, avoid accessing personal accounts or sensitive data while you are connected to these networks.
2. Pay attention to those around you. The person sitting next to you on the plane or while you are waiting to board your plane may have malicious intent. Someone could be looking over your shoulder while you're entering your credit card information or logging into social media. It's smart to get a screen protector, which can help you hide your information from prying eyes.
3. Double-check the websites you make travel reservations on. Travel-related cyberattacks can happen even before the trip begins, so it's vital to check the travel website you use. Scammers like to impersonate genuine websites and pretend to offer luxury vacations or discounted travel in order to steal your personal information. If an offer looks or sounds too good to be true, it probably is. Before proceeding, thoroughly research the company offering the deal. Use a credit card for travel transactions, not a debit card. Credit card companies often have fraud protection in case you fall victim to cybercrime, whereas with a debit card, your money is likely gone.
4. Beware of language mistakes. In this case, we are not talking about learning the local dialect, but rather be aware of any spelling or grammar mistakes, as well as authoritative phrases that push you to make hasty decisions, as this could indicate that something is not right. it's going great. That's because cybercriminals rely on people not taking the time to look at the small details that might signal an email or message isn't legitimate. To stay protected, always take an extra minute to verify the authenticity of a message, especially if it's trying to get you to reset your login details, as once a hacker gains access, it won't take long to wreak havoc.
5. Never share your credentials. Most people reuse the same usernames and passwords access to many online accounts, which is why credential theft is a common target of phishing scams. Therefore, you should be very careful whenever you are asked for your login information. Phishing emails/messages usually impersonate well-known brands, impersonate customer support specialists or even impersonate your employer. To keep your accounts secure, never share your credentials via email or text, and enter them online to access services only after you've authenticated the site by going directly from your chosen browser.
6. Turn off automatic Wi-Fi/Bluetooth connections. There may be a default setting on your smartphone to automatically connect to an available Wi-Fi or Bluetooth network, which may allow malicious actors to gain access to your device. Make sure this feature is disabled to prevent cybercriminals from hacking your device.
7. Use multi-factor authentication. When you are on vacation, you may need to access important services that contain confidential or financial data. To be safe, use a multi-factor authentication (MFA) process to ensure that you are the only person who can access these services and that you are notified if an unauthorized person attempts to connect.
8. Download the latest security updates. Before you get ready to leave for your trip, make sure all your devices are up to date with the latest security updates. This way you will keep them protected from the latest known threats.
9. Get informed about the latest attacks. It's a good practice to do some research on the latest attacks going around so you don't fall prey to any tricks threat actors might use to spread ransomware. Remember that not all scams are based on phishing and that you could still be exposed to provide your credentials over the phone or SMS.
10. Be suspicious of ATMs. Avoid withdrawing money from ATMs, as hackers, especially in tourist areas, have been known to attach credit card skimming devices to stand-alone ATMs. If you must use one, find an official machine banks, preferably one located within the lobby of your trusted bank.





